Blog
The police browsing case details using the Crime and Criminal Tracking Network and Systems Technology in Hyderabad. Photo:K. RAMESH BABU
Respondents of various perspectives spoke for the public consultation regarding different sections of the Mapping Digital Media: India report.
CANDID CAMERA: Media coverage is often critical to whether someone relatively powerless is able to assert her rights against a very powerful person. Photo: Monica Tiwari
Privacy Events Poster
 Privacy Events.pdf
—
PDF document,
37 kB (38448 bytes)
Privacy Events.pdf
—
PDF document,
37 kB (38448 bytes)
CIS and International Coalition Calls upon Governments to Protect Privacy
On September 20 in Geneva, CIS joined a huge international coalition in calling upon countries across the globe, including India to assess whether national surveillance laws and activities are in line with their international human rights obligations.
The Centre for Internet and Society has endorsed a set of international principles against unchecked surveillance. The 13 Principles set out for the first time an evaluative framework for assessing surveillance practices in the context of international human rights obligations.
A group of civil society organizations officially presented the 13 Principles this past Friday in Geneva at a side event attended by Navi Pillay, the United Nations High Commissioner for Human Rights and the United Nations Special Rapporteur on Freedom of Expression and Opinion, Frank LaRue, during the 24th session of the Human Rights Council. The side event was hosted by the Permanent Missions of Austria, Germany, Liechtenstein, Norway, Switzerland and Hungary.
Elonnai Hickok, Programme Manager at the Centre for Internet and Society has noted that "the 13 Principles are an important first step towards informing governments, corporates, and individuals across jurisdictions, including India, about needed safeguards for surveillance practices and related policies to ensure that they are necessary and proportionate."
Navi Pillay, the United Nations High Commissioner for Human Rights, speaking at the Human Rights Council stated in her opening statement on September 9:
"Laws and policies must be adopted to address the potential for dramatic intrusion on individuals’ privacy which have been made possible by modern communications technology."
Navi Pillay, the United Nations High Commissioner for Human Rights, speaking at the event, said that:
"technological advancements have been powerful tools for democracy by giving access to all to participate in society, but increasing use of data mining by intelligence agencies blurs lines between legitimate surveillance and arbitrary mass surveillance."
Frank La Rue, the United Nations Special Rapporteur on Freedom of Expression and Opinion made clear the case for a direct relationship between state surveillance, privacy and freedom of expression in this latest report to the Human Rights Council:
"The right to privacy is often understood as an essential requirement for the realization of the right to freedom of expression. Undue interference with individuals’ privacy can both directly and indirectly limit the free development and exchange of ideas. … An infringement upon one right can be both the cause and consequence of an infringement upon the other."
Speaking at the event, the UN Special Rapporteur remarked that:
"previously surveillance was carried out on targeted basis but the Internet has changed the context by providing the possibility for carrying out mass surveillance. This is the danger."
Representatives of the Centre for Internet and Society, Privacy International, the Electronic Frontier Foundation,Access,Human Rights Watch,Reporters Without Borders, Association for Progressive Communications, and theCenter for Democracy and Technology all are taking part in the event.
Find out more about the Principles at https://NecessaryandProportionate.org
Contacts
NGOs currently in Geneva for the 24th Human Rights Council:
Access
Fabiola Carrion: [email protected]
Association for Progressive Communication
Shawna Finnegan: [email protected]
Center for Democracy and Technology
Matthew Shears: [email protected]
Electronic Frontier Foundation
Katitza Rodriguez: [email protected] - @txitua
Human Rights Watch
Cynthia Wong: [email protected]
Privacy International
Carly Nyst: [email protected]
Reporters Without Borders
Lucie Morillon: [email protected]
Hélène Sackstein: [email protected]
Signatories
Argentina
Ramiro Alvarez: [email protected]
Asociación por los Derechos Civiles
Argentina
Beatriz Busaniche: [email protected]
Fundación Via Libre
Colombia
Carolina Botero: [email protected]
Fundación Karisma
Egypt
Ahmed Ezzat: [email protected]
Afteegypt
Honduras
Hedme Sierra-Castro: [email protected]
ACI-Participa
India
Elonnai Hickok: [email protected]
Center for Internet and Society
Korea
Prof. Park: [email protected]
Open Net Korea
Macedonia
Bardhyl Jashari: [email protected]
Metamorphosis Foundation for Internet and Society
Mauritania, Senegal, Tanzania
Abadacar Diop: [email protected]
Jonction
Portugal
Andreia Martins: [email protected]
ASSOCIAÇÃO COOLPOLITICS
Peru
Miguel Morachimo: [email protected]
Hiperderecho
Russia
Andrei Soldatov: [email protected]
Agentura.ru
Serbia
Djordje Krivokapic: [email protected]
SHARE Foundation
Western Balkans
Valentina Pellizer: [email protected]
Oneworldsee
Brasil
Marcelo Saldanha: [email protected]
IBEBrasil
Bangalore + Social Good
 The Social Good Summit.pdf
—
PDF document,
181 kB (185484 bytes)
The Social Good Summit.pdf
—
PDF document,
181 kB (185484 bytes)
The National Cyber Security Policy: Not a Real Policy
This article was published in the Observer Research Foundation's Cyber Security Monitor Vol. I, Issue.1, August 2013.
For some time now, law and policy observers in India have been noticing a definite decline in the quality of national policies emanating from the Central Government. Unlike legislation, which is notionally subject to debate in the Parliament of India, policies face no public evaluation before they are brought in to force. Since, unlike legislation, policies are neither binding nor enforceable, there has been no principled ground for demanding public deliberation of significant national policies. While Parliament’s falling standard of competence has been almost unanimously condemned, there has been nearly no criticism of the corresponding failure of the Centre to invigilate the quality of the official policies of its ministries. Luckily for the drafters of the National Cyber Security Policy (NCSP), the rest of the country has also mostly failed to notice its poor content.
The NCSP was notified into effect on 2 July 2013 by the Department of Electronics and Information Technology – which calls itself DeitY – of the Ministry of Communications and Information Technology. As far as legislation and legal drafting go, DeitY has a dubious record. In March 2013, in a parliamentary appraisal of subordinate law framed by DeitY, a Lok Sabha committee found ambiguity, invasions of privacy and potentially illegal clauses. Apprehensions about statutory law administered by DeitY have also found their way to the Supreme Court of India, where a constitutional challenge to certain provisions of the Information Technology Act, 2000 (IT Act) continues. On more than one occasion, owing to poor drafting, DeitY has been forced to issue advisories and press releases to clarify the meaning of its laws. Ironically, the legal validity of these clarifications is also questionable.
A national policy must set out, in real and quantifiable terms, the objectives of the government in a particular field within a specified time frame. To do that, the policy must provide the social, economic, political and legal context prevalent at the time of its issue as well as a normative statement of factual conditions it seeks to achieve at the time of its expiry. Between these two points in time, the policy must identify and explain all the particular social, economic, political and legal measures it intends to implement to secure its success. Albeit concerned solely with economic growth, the Five-Year Plans – the Second and Tenth Plans in particular, without prejudice to their success or failure, are samples of policies that are well-drafted. In this background, the NCSP should be judged on the basis of how it addresses, in no particular order, national security, democratic freedoms, economic growth and knowledge development. Let us restrict ourselves to the first two issues.
There are broadly two intersections between national security and information technology; these are: (i) the security of networked communications used by the armed forces and intelligence services, and (ii) the storage of civil information of national importance. While the NCSP makes no mention of it, the adoption of the doctrine of network-centric warfare by the three armed forces is underway. Understanding the doctrine is simple – an intensive use of information technology to create networks of information aids situational awareness and enables collaboration to bestow an advantage in combat. However, the doctrine is vulnerable to asymmetric attack using both primitive and highly sophisticated means. Pre-empting such attacks should be a primary policy concern; not so, apparently, for the NCSP which is completely silent on this issue. The NCSP is slightly more forthcoming on the protection of critical information infrastructure of a civil nature. Critical information infrastructure, such as the national power grid or the Aadhar database, is narrowly defined in section 70 of the IT Act where it used to describe a protected system. Other provisions of the IT Act also deal with the protection of critical information infrastructure. The NCSP does not explain how these statutory provisions have worked or failed, as the case may be, to necessitate further mention in a policy document. For instance, section 70A of the IT Act, inserted in 2008, enables the creation of a national nodal agency to undertake research and development and other activities in respect of critical information infrastructure. Despite this, five years later, the NCSP makes a similar recommendation to operate a National Critical Information Infrastructure Protection Centre to undertake the same activities. In the absence of any meaningful explanation of intended policy measures, there is no reason to expect that the NCSP will succeed where an Act of Parliament has failed.
But, putting aside the shortcomings of its piece-meal provisions, the NCSP also fails to address high-level conceptual policy concerns. As information repositories and governance services through information technology become increasingly integrated and centralised, the security of the information that is stored or distributed decreases. Whether by intent or error, if these consolidated repositories of information are compromised, the quantity of information susceptible to damage is greater leading to higher insecurity. Simply put, if power transmission is centrally controlled instead of zonally, a single attack could black out the entire country instead of only a part of it. Or if personal data of citizens is centrally stored, a single leak could compromise the privacy of millions of people instead of only hundreds. Therefore, a credible policy must, before it advocates greater centralisation of information, examine the merits of diffused information storage to protect national security. The NCSP utterly fails in this regard.
Concerns short of national security, such as the maintenance of law and order, are also in issue because crime is often planned and perpetrated using information technology. The prevention of crime before it is committed and its prosecution afterwards is a key policy concern. While the specific context may vary depending on the nature of the crime – the facts of terrorism are different from those of insurance fraud – the principles of constitutional and criminal law continue to apply. However, the NCSP neither examines the present framework of cybersecurity-related offences nor suggests any changes in existing law. It merely calls for a “dynamic legal framework and its periodic review to address the cyber security challenges” (sic). This is self-evident, there was no need for a new national policy to make this discovery; and, ironically, it fails to conduct the very periodic review that it envisages. This is worrying because the NCSP presented DeitY with an opportunity to review existing laws and learn from past mistakes. There are concerns that cybersecurity laws, especially relevant provisions of the IT Act and its rules, betray a lack of understanding of India’s constitutional scheme. This is exemplified by the insertion, in 2008, of section 66A into the IT Act that criminalises the sending of annoying, offensive and inconvenient electronic messages without regard for the fact that free speech that is annoying is constitutionally protected.
In India, cybersecurity law and policy attempts to compensate for the state’s inability to regulate the internet by overreaching into and encroaching upon democratic freedoms. The Central Monitoring System (CMS) that is being assembled by the Centre is a case in point. Alarmed at its inability to be privy to private communications, the Centre proposes to build systems to intercept, in real time, all voice and data traffic in India. Whereas liberal democracies around the world require such interceptions to be judicially sanctioned, warranted and supported by probable cause, India does not even have statutory law to regulate such an enterprise. Given that, once completed, the CMS will represent the largest domestic interception effort in the world, the failure of the NCSP to examine the effect of such an exercise on daily cybersecurity is bewildering. This is made worse by the fact that the state does not possess the technological competence to build such a system by itself and is currently tendering private companies for equipment. The state’s incompetence is best portrayed by the activities of the Indian Computer Emergency Response Team (CERT-In) that was constituted under section 70B of the IT Act to respond to “cyber incidents”. CERT-In has repeatedly engaged in extra-judicial censorship and has ham-handedly responded to allegedly objectionable blogs or websites by blocking access to entire domains. Unfortunately, the NCSP, while reiterating the operations of CERT-In, attempts no evaluation of its activities precluding the scope for any meaningful policy measures.
The NCSP’s poor drafting, meaningless provisions, deficiency of analysis and lack of stated measures renders it hollow. Its notification into force adds little to the public or intellectual debate about cybersecurity and does nothing to further the trajectory of either national security or democratic freedoms in India. In fairness, this problem afflicts many other national policies. There is a need to revisit the high intellectual and practical standards set by most national policies that were issued in the years following Independence.
India:Privacy in Peril
The police browsing case details using the Crime and Criminal Tracking Network and Systems Technology in Hyderabad. Photo:K. RAMESH BABU
The article was originally published in the Frontline on July 12, 2013.
At the concluding scene of his latest movie, Superman disdainfully flings a surveillance drone down to earth in front of a horrified general. “You can’t control me,” he tells his military minder. “You can’t find out where I hang up my cape.” This exchange goes to the crux of surveillance: control. Surveillance is the means by which nation-states exercise control over people. If the logical basis of the nation-state is the establishment and maintenance of homogeneity, it is necessary to detect and interdict dissent before it threatens the boundedness and continuity of the national imagination. This imagination often cannot encompass diversity, so it constructs categories of others that include dissenters and outsiders. Admittedly, this happens less in India because the foundation of the Indian nation-state imagined a diverse society expressing a plurality of ideas in a variety of languages secured by a syncretic and democratic government that protected individual freedoms. Unfortunately, this vision is still to be realised, and the foundational idea of India continues to be challenged by poor governance, poverty, insurgencies and rebellion. Consequently, surveillance is, for the modern nation-state, a condicio sine qua non—an essential element without which it will eventually cease to exist. The challenge for democratic nation-states is to find the optimal balance between surveillance and the duty to protect the freedoms of its citizens.
History of wiretaps
Some countries, such as the United States, have assembled a vast apparatus of surveillance to monitor the activities of their citizens and foreigners. Let us review the recent controversy revealed by the whistle-blower Edward Snowden. In 1967, the U.S. Supreme Court ruled in Katz vs United States that wiretaps had to be warranted, judicially sanctioned and supported by probable cause. This resulted in the passage of the Wiretap Act of 1968 that regulated domestic surveillance. Following revelations that Washington was engaging in unrestricted foreign surveillance in the context of the Vietnam war and anti-war protests, the U.S. Congress enacted the Foreign Intelligence Surveillance Act (FISA) in 1978. FISA gave the U.S. government the power to conduct, without judicial sanction, surveillance for foreign intelligence information; and, with judicial sanction from a secret FISA court, surveillance of anybody if the ultimate target was a foreign power. Paradoxically, even a U.S. citizen could be a foreign power in certain circumstances. Domestically, FISA enabled secret warrants for specific items of information such as library book borrowers and car rentals.
Following the 9/11 World Trade Centre attacks, Congress enacted the Patriot Act of 2001, Section 215 of which dramatically expanded the scope of FISA to allow secret warrants to conduct surveillance in respect of “any tangible thing” that was relevant to a national security investigation. In exercise of this power, a secret FISA court issued secret warrants ordering a number of U.S. companies to share, in real time, voice and data traffic with the National Security Agency (NSA). We may never know the full scope of the NSA’s surveillance, but we know this: (a) Verizon Communications, a telecommunications major, was ordered to provide metadata for all telephone calls within and without the U.S.; (b) the NSA runs a clandestine programme called PRISM that accesses Internet traffic, such as e-mails, web searches, forum comments and blogs, in real time; and (c) the NSA manages a comprehensive data analysis system called Boundless Informant that intercepts and analyses voice and data traffic around the world and subjects them to automated pattern recognition. The documents leaked by Snowden allege that Google, Facebook, Apple, Dropbox, Microsoft and Yahoo! participate in PRISM, but these companies have denied their involvement.
India fifth-most monitored
How does this affect India? The Snowden documents reveal that India is the NSA’s fifth-most monitored country after Iran, Pakistan, Jordan and Egypt. Interestingly, China is monitored less than India. Several billion pieces of data from India, such as e-mails and telephone metadata, were intercepted and monitored by the NSA. For Indians, it is not inconceivable that our e-mails, should they be sent using Gmail, Yahoo! Mail or Hotmail, or our documents, should we be subscribing to Dropbox, or our Facebook posts, are being accessed and read by the NSA. Incredibly, most Indian governmental communication, including that of Ministers and senior civil servants, use private U.S. e-mail services. We no longer enjoy privacy online. The question of suspicious activity, irrespective of the rubric under which suspicion is measured, is moot. Any use of U.S. service providers is potentially compromised since U.S. law permits intrusive dragnet surveillance against foreigners. This clearly reveals a dichotomy in U.S. constitutional law: the Fourth Amendment’s guarantees of privacy, repeatedly upheld by U.S. courts, protect U.S. citizens to a far greater extent than they do foreigners. It is natural for a nation-state to privilege the rights of its citizens over others. As Indians, therefore, we must clearly look out for ourselves.
Privacy and personal liberty
Unfortunately, India does not have a persuasive jurisprudence of privacy protection. In the Kharak Singh (1964) and Gobind (1975) cases, the Supreme Court of India considered the question of privacy from physical surveillance by the police in and around homes of suspects. In the latter case, the court found that some of the Fundamental Rights “could be described as contributing to the right to privacy”, which was subject to a compelling public interest. This insipid inference held the field until 1994 when, in the Rajagopal (“Auto Shankar”, 1994) case, the Supreme Court, for the first time, directly located privacy within the ambit of the right to personal liberty recognised by Article 21 of the Constitution. However, Rajagopal dealt specifically with the publication of an autobiography, it did not consider the privacy of communications. In 1997, the Supreme Court considered the question of wiretaps in the People’s Union for Civil Liberties (PUCL) case. While finding that wiretaps invaded the privacy of communications, it continued to permit them subject to some procedural safeguards which continue to be routinely ignored. A more robust statement of the right to privacy was made by the Delhi High Court in the Naz Foundation case (2011) that decriminalised consensual homosexual acts; however, there is an appeal against the judgment in the Supreme Court.
Legislative silence
Judicial vagueness has been compounded by legislative silence. India does not have a law to operationalise a right to privacy. Consequently, a multitude of laws permit daily infractions of privacy. These infractions have survived because they are diverse, dissipated and quite disorganised. However, the technocratic impulse to centralise and consolidate surveillance and data collection has, in recent years, alarmed many citizens. The state hopes to, through enterprises such as the Central Monitoring System (CMS), the Crime and Criminals Tracking Network and System (CCTNS), the National Intelligence Grid (NATGRID), the Telephone Call Interception System (TCIS) and the Unique Identification Number (UID), replicate the U.S. successes in surveillance and monitoring and profiling all its citizens. However, unlike the U.S., India proposes to achieve this without an enabling law. Let us consider the CMS. No documents have been made available that indicate the scope and size of the CMS.
From a variety of police tenders for private equipment, it appears that the Central government hopes to put in place a system that will intercept, in real time, all voice and data traffic originating or terminating in India or being carried by Indian service providers. This data will be subject to pattern recognition and other automated tests to detect emotional markers, such as hate, compassion or intent. The sheer scale of this enterprise is intimidating; all communications in India’s many languages will be subject to interception and testing designed to detect different forms of dissent. This mammoth exercise in monitoring is taking place—it is understood that some components of the CMS are already operational—without statutory sanction. No credible authorities exist to supervise this exercise, no avenues for redress have been identified and no consequences have been laid down for abuse.
Statutory Surveillance
In a recent interview, Milind Deora, Minister of State for Communications and Information Technology, dismissed public scepticism of the CMS saying that direct state access to private communications was better for privacy since it reduced dependence on the interception abilities of private service providers. This circular argument is both disingenuous and incorrect. No doubt, trusting private persons with the power to intercept and store the private data of citizens is flawed. The leaking of the Niira Radia tapes, which contain the private communications of Niira Radia taped on the orders of the Income Tax Department, testifies to this flaw. However, bypassing private players to enable direct state access to private communications will preclude leaks and, thereby, remove from public knowledge the fact of surveillance. This messy situation may be obviated by a regime of statutory regulation of warranted surveillance by an independent and impartial authority. This system is favoured by liberal democracies around the world but conspicuously resisted by the Indian government.
The question of privacy legislation was recently considered by a committee chaired by Justice Ajit Prakash Shah, a former judge of the Delhi High Court who sat on the Bench that delivered the Naz Foundation judgment. The Shah Committee was constituted by the Planning Commission for a different reason: the need to protect personal data that are outsourced to India for processing. The lack of credible privacy law, it is foreseen, will result in European and other foreign personal data being sent to other attractive processing destinations, such as Vietnam, Israel or the Philippines, resulting in the decline of India’s outsourcing industry. However, the Shah Committee also noted the absence of law sufficient to protect against surveillance abuses. Most importantly, the Shah Committee formulated nine national privacy principles to inform any future privacy legislation (see story on page 26). In 2011, the Department of Personnel and Training (DoPT) of the Ministry of Human Resource Development, the same Ministry entrusted with implementing the Right to Information Act, 2005, leaked a draft privacy Bill, marked ‘Secret’, on the Internet. The DoPT Bill received substantive criticism from the Attorney General and some government Secretaries for the clumsy drafting. A new version of the DoPT Bill is reported to have been drafted and sent to the Ministry of Law for consideration. This revised Bill, which presumably contains chapters to regulate surveillance, including the interception of communications, has not been made public.
The need for privacy legislation cannot be overstated. The Snowden affair reveals the extent of possible state surveillance of private communications. For Indians who must now explore ways to protect their privacy against the juggernaut of state and private surveillance, the absence of regulatory law is damning. Permitting, through public inaction, unwarranted and non-targetted dragnet surveillance by the Indian state without reasonable cause would be an act of surrender of far-reaching implications.
Information, they say, is power. Allowing governments to exercise this power over us without thought for the rule of law constitutes the ultimate submission possible in a democratic nation-state. And, since superheroes are escapist fantasies, without the prospect of good laws we will all be subordinate to a new national imagination of control and monitoring, surveillance and profiling. If allowed to come to pass, this will be a betrayal of the foundational idea of India as a free and democratic republic tolerant of dissent.
Bhairav Acharya is a constitutional lawyer practising in the Supreme Court of India. He advises the Centre for Internet & Society, Bangalore, on privacy law and other constitutional issues.
The Central Monitoring System: Some Questions to be Raised in Parliament
Preliminary
- The Central Monitoring System (CMS) is a Central Government project to intercept communications, both voice and data, that is transmitted via telephones and the internet to, from and within India. Owing to the vast nature of this enterprise, the CMS cannot be succinctly described and the many issues surrounding this project are diverse. This Issue Brief will outline preliminary constitutional, legal and technical concerns that are presented by the CMS.
- At the outset, it must be clearly understood that no public documentation exists to explain the scope, functions and technical architecture of the CMS. This lack of transparency is the single-largest obstacle to understanding the Central Government’s motives in conceptualising and operationalizing the CMS. This lack of public documentation is also the chief reason for the brevity of this Issue Note. Without making public the policy, law and technical abilities of the CMS, there cannot be an informed national debate on the primary concerns posed by the CMS, i.e the extent of envisaged state surveillance upon Indian citizens and the safeguards, if any, to protect the individual right to privacy.
Surveillance and Privacy
- Surveillance is necessary to secure political organisation. Modern nation-states, which are theoretically organised on the basis of shared national and societal characteristics, require surveillance to detect threats to these characteristics. In democratic societies, beyond the immediate requirements of national integrity and security, surveillance must be targeted at securing the safety and rights of individual citizens. This Issue Brief does not dispute the fact that democratic countries, such as India, should conduct surveillance to secure legitimate ends. Concerns, however, arise when surveillance is conducted in a manner unrestricted and unregulated by law; these concerns are compounded when a lack of law is accompanied by a lack of transparency.
- Technological advancement leads to more intrusive surveillance. The evolution of surveillance in the United States resulted, in 1967, in the first judicial recognition of the right to privacy. In Katz v. United States the US Supreme Court ruled that the privacy of communications had to be balanced with the need to conduct surveillance; and, therefore, wiretaps had to be warranted, judicially sanctioned and supported by probable cause. Katz expanded the scope of the Fourth Amendment of the US Constitution, which protected against unreasonable searches and seizures. Most subsequent US legal developments relating to the privacy of communications from surveillance originate in the Katz judgement. Other common law countries, such as the United Kingdom and Canada, have experienced similar judicial evolution to recognise that the right to privacy must be balanced with governance.
Right to Privacy in India
- Unfortunately, India does not have a persuasive jurisprudence of privacy protection. In the Kharak Singh (1964) and Gobind (1975) cases, the Supreme Court of India considered the question of privacy from physical surveillance by the police in and around the homes of suspects. In the latter case, the Supreme Court found that some of the Fundamental Rights “could be described as contributing to the right to privacy” which was nevertheless subject to a compelling public interest. This insipid inference held the field until 1994 when, in the Rajagopal (“Auto Shankar”, 1994) case, the Supreme Court, for the first time, directly located privacy within the ambit of the right to personal liberty recognised by Article 21 of the Constitution. However, Rajagopal dealt specifically with the publication of an autobiography, it did not consider the privacy of communications. In 1997, the Supreme Court considered the question of wiretaps in the PUCL case. While finding that wiretaps invaded the privacy of communications, it continued to permit them subject to some procedural safeguards which continue to be routinely ignored. A more robust statement of the right to privacy was made recently by the Delhi High Court in the Naz Foundation case (2011) that de-criminalised consensual homosexual acts; however, this judgment has been appealed to the Supreme Court.
Issues Pertaining to the CMS
- While judicial protection from physical surveillance was cursorily dealt with in the Kharak Singh and Gobind cases, the Supreme Court of India directly considered the issue of wiretaps in the PUCL case. Wiretaps in India primarily occur on the strength of powers granted to certain authorities under section 5(2) of the Indian Telegraph Act, 1885. The Court found that the Telegraph Act, and Rules made thereunder, did not prescribe adequate procedural safeguards to create a “just and fair” mechanism to conduct wiretaps. Therefore, it laid down the following procedure to conduct wiretaps:
(a) the order should be issued by the relevant Home Secretary (this power is delegable to a Joint Secretary),
(b) the interception must be carried out exactly in terms of the order and not in excess of it,
(c) a determination of whether the information could be reasonably secured by other means,
(d) the interception shall cease after sixty (60) days.
- Therefore, prima facie, any voice interception conducted through the CMS will be in violation of this Supreme Court judgement. The CMS will enforce blanket surveillance upon the entire country without regard for reasonable cause or necessity. This movement away from targeted surveillance to blanket surveillance without cause, conducted without statutory sanction and without transparency, is worrying.
- Accordingly, the following questions may be raised, in Parliament, to learn more about the CMS project:
- Which statutes, Government Orders, notifications etc deal with the establishment and maintenance of the CMS?
- Which is the nodal agency in charge of implementing the CMS?
- What are the powers and functions of the nodal agency?
- What guarantees exist to protect ordinary Indian citizens from intrusive surveillance without cause?
- What are the technical parameters of the CMS?
- What are the consequences for misuse or abuse of powers by any person working in the CMS project?
- What recourse is available to Indian citizens against whom there is unnecessary surveillance or against whom there has been a misuse or abuse of power?
CYFY 2013 Event Brochure
 cyfy flyer prog.pdf
—
PDF document,
854 kB (875361 bytes)
cyfy flyer prog.pdf
—
PDF document,
854 kB (875361 bytes)
Privacy Timeline
 Timeline.pdf
—
PDF document,
42 kB (43167 bytes)
Timeline.pdf
—
PDF document,
42 kB (43167 bytes)
Privacy Roundtable Delhi (October)
 Invite-Delhi.pdf
—
PDF document,
2395 kB (2453051 bytes)
Invite-Delhi.pdf
—
PDF document,
2395 kB (2453051 bytes)
Privacy Protection Bill (September 2013)
 Privacy (Protection) Bill - 20 Sep 2013.pdf
—
PDF document,
199 kB (204657 bytes)
Privacy (Protection) Bill - 20 Sep 2013.pdf
—
PDF document,
199 kB (204657 bytes)
Privacy (Protection) Bill, 2013: Updated Third Draft
This research is being undertaken as part of the 'SAFEGUARDS' project that CIS is doing with Privacy International and IDRC. The following is the latest version with changes based on the Round Table held on August 24:
[Preamble]
CHAPTER I
Preliminary
1. Short title, extent and commencement. – (1) This Act may be called the Privacy (Protection) Act, 2013.
(2) It extends to the whole of India.
(3) It shall come into force on such date as the Central Government may, by notification in the Official Gazette, appoint.
2. Definitions. – In this Act and in any rules made thereunder, unless the context otherwise requires, –
(a) “anonymise” means, in relation to personal data, the removal of all data that may, whether directly or indirectly in conjunction with any other data, be used to identify the data subject;
(b) “appropriate government” means, in relation the Central Government or a Union Territory Administration, the Central Government; in relation a State Government, that State Government; and, in relation to a public authority which is established, constituted, owned, controlled or substantially financed by funds provided directly or indirectly –
(i) by the Central Government or a Union Territory Administration, the Central Government;
(ii) by a State Government, that State Government;
(c) “authorised officer” means an officer, not below the rank of a Gazetted Officer, of an All India Service or a Central Civil Service, as the case may be, who is empowered by the Central Government, by notification in the Official Gazette, to intercept a communication of another person or carry out surveillance of another person under this Act;
(d) “biometric data” means any data relating to the physical, physiological or behavioural characteristics of a person which allow their unique identification including, but not restricted to, facial images, finger prints, hand prints, foot prints, iris recognition, hand writing, typing dynamics, gait analysis and speech recognition;
(e) “Chairperson” and “Member” mean the Chairperson and Member appointed under sub-section (1) of section 17;
(f) “collect”, with its grammatical variations and cognate expressions, means, in relation to personal data, any action or activity that results in a data controller obtaining, or coming into the possession or control of, any personal data of a data subject;
(g) “communication” means a word or words, spoken, written or indicated, in any form, manner or language, encrypted or unencrypted, meaningful or otherwise, and includes visual representations of words, ideas, symbols and images, whether transmitted or not transmitted and, if transmitted, irrespective of the medium of transmission;
(h) “competent organisation” means an organisation or public authority listed in the Schedule;
(i) “data controller” means a person who, either alone or jointly or in concert with other persons, determines the purposes for which and the manner in which any personal data is processed;
(j) “data processor” means any person who processes any personal data on behalf of a data controller;
(k) “Data Protection Authority” means the Data Protection Authority constituted under sub-section (1) of section 17;
(l) “data subject” means a person who is the subject of personal data;
(m) “deoxyribonucleic acid data” means all data, of whatever type, concerning the characteristics of a person that are inherited or acquired during early prenatal development;
(n) “destroy”, with its grammatical variations and cognate expressions, means, in relation to personal data, to cease the existence of, by deletion, erasure or otherwise, any personal data;
(o) “disclose”, with its grammatical variations and cognate expressions, means, in relation to personal data, any action or activity that results in a person who is not the data subject coming into the possession or control of that personal data;
(p) “intelligence organisation” means an intelligence organisation under the Intelligence Organisations (Restriction of Rights) Act, 1985 (58 of 1985);
(q) “interception” or “intercept” means any activity intended to capture, read, listen to or understand the communication of a person;
(r) “personal data” means any data which relates to a natural person if that person can, whether directly or indirectly in conjunction with any other data, be identified from it and includes sensitive personal data;
(s) “prescribed” means prescribed by rules made under this Act;
(t) “process”, with its grammatical variations and cognate expressions, means, in relation to personal data, any action or operation which is performed upon personal data, whether or not by automated means including, but not restricted to, organisation, structuring, adaptation, modification, retrieval, consultation, use, alignment or destruction;
(u) “receive”, with its grammatical variations and cognate expressions, means, in relation to personal data, to come into the possession or control of any personal data;
(v) “sensitive personal data” means personal data as to the data subject’s –
(i) biometric data;
(ii) deoxyribonucleic acid data;
(iii) sexual preferences and practices;
(iv) medical history and health;
(v) political affiliation;
(vi) commission, or alleged commission, of any offence;
(vii) ethnicity, religion, race or caste; and
(viii) financial and credit information.
(w) “store”, with its grammatical variations and cognate expressions, means, in relation to personal data, to retain, in any form or manner and for any purpose or reason, any personal data;
(x) “surveillance” means any activity intended to watch, monitor, record or collect, or to enhance the ability to watch, record or collect, any images, signals, data, movement, behaviour or actions, of a person, a group of persons, a place or an object, for the purpose of obtaining information of a person;
and all other expressions used herein shall have the meanings ascribed to them under the General Clauses Act, 1897 (10 of 1897) or the Code of Criminal Procedure, 1973 (2 of 1974), as the case may be.
CHAPTER II
Regulation of Personal Data
3. Regulation of personal data. – Notwithstanding anything contained in any other law for time being in force, no person shall collect, store, process, disclose or otherwise handle any personal data of another person except in accordance with the provisions of this Act and any rules made thereunder.
4. Exemption. – Nothing in this Act shall apply to the collection, storage, processing or disclosure of personal data for personal or domestic use.
CHAPTER III
Protection of Personal Data
5. Regulation of collection of personal data. – (1) No personal data of a data subject shall be collected except in conformity with section 6 and section 7.
(2) No personal data of a data subject may be collected under this Act unless it is necessary for the achievement of a purpose of the person seeking its collection.
(3) Subject to section 6 and section 7, no personal data may be collected under this Act prior to the data subject being given notice, in such and form and manner as may be prescribed, of the collection.
6. Collection of personal data with prior informed consent. – (1) Subject to sub-section (2), a person seeking to collect personal data under this section shall, prior to its collection, obtain the consent of the data subject.
(2) Prior to a collection of personal data under this section, the person seeking its collection shall inform the data subject of the following details in respect of his personal data, namely: –
(a) when it will be collected;
(b) its content and nature;
(c) the purpose of its collection;
(d) the manner in which it may be accessed, checked and modified;
(e) the security practices, privacy policies and other policies, if any, to which it will be subject;
(f) the conditions and manner of its disclosure; and
(g) the procedure for recourse in case of any grievance in relation to it.
(3) Consent to the collection of personal data under this section may be obtained from the data subject in any manner or medium but shall not be obtained as a result of a threat, duress or coercion:
Provided that the data subject may, at any time after his consent to the collection of personal data has been obtained, withdraw the consent for any reason whatsoever and all personal data collected following the original grant of consent shall be destroyed forthwith:
Provided that the person who collected the personal data in respect of which consent is subsequently withdrawn may, if the personal data is necessary for the delivery of any good or the provision of any service, not deliver that good or deny that service to the data subject who withdrew his grant of consent.
7. Collection of personal data without prior consent. – Personal data may be collected without the prior consent of the data subject if it is –
(a) necessary for the provision of an emergency medical service to the data subject;
(b) required for the establishment of the identity of the data subject and the collection is authorised by a law in this regard;
(c) necessary to prevent a reasonable threat to national security, defence or public order; or
(d) necessary to prevent, investigate or prosecute a cognisable offence.
8. Regulation of storage of personal data. – (1) No person shall store any personal data for a period longer than is necessary to achieve the purpose for which it was collected or received, or, if that purpose is achieved or ceases to exist for any reason, for any period following such achievement or cessation.
(2) Save as provided in sub-section (3), any personal data collected or received in relation to the achievement of a purpose shall, if that purpose is achieved or ceases to exist for any reason, be destroyed forthwith.
(3) Notwithstanding anything contained in this section, any personal data may be stored for a period longer than is necessary to achieve the purpose for which it was collected or received, or, if that purpose has been achieved or ceases to exist for any reason, for any period following such achievement or cessation, if –
(a) the data subject grants his consent to such storage prior to the purpose for which it was collected or received being achieved or ceasing to exist;
(b) it is adduced for an evidentiary purpose in a legal proceeding; or
(c) it is required to be stored under the provisions of an Act of Parliament:
Provided that only that amount of personal data that is necessary to achieve the purpose of storage under this sub-section shall be stored and any personal data that is not required to be stored for such purpose shall be destroyed forthwith:
Provided further that any personal data stored under this sub-section shall, to the extent possible, be anonymised.
9. Regulation of processing of personal data. – (1) No person shall process any personal data that is not necessary for the achievement of the purpose for which it was collected or received.
(2) Save as provided in sub-section (3), no personal data shall be processed for any purpose other than the purpose for which it was collected or received.
(3) Notwithstanding anything contained in this section, any personal data may be processed for a purpose other than the purpose for which it was collected or received if –
(a) the data subject grants his consent to the processing and only that amount of personal data that is necessary to achieve the other purpose is processed;
(b) it is necessary to perform a contractual duty to the data subject;
(c) it is necessary to prevent a reasonable threat to national security, defence or public order; or
(d) it necessary to prevent, investigate or prosecute a cognisable offence.
10. Transfer of personal data for processing. – (1) Subject to the provisions of this section, personal data that has been collected in conformity with this Act may be transferred by a data controller to a data processor, whether located in India or otherwise, if the transfer is pursuant to an agreement that explicitly binds the data processor to same or stronger measures in respect of the storage, processing, destruction, disclosure and other handling of the personal data as are contained in this Act.
(2) No data processor shall process any personal data transferred under this section except to achieve the purpose for which it was collected.
(3) A data controller that transfers personal data under this section shall remain liable to the data subject for the actions of the data processor.
11. Security of personal data and duty of confidentiality. – (1) No person shall collect, receive, store, process or otherwise handle any personal data without implementing measures, including, but not restricted to, technological, physical and administrative measures, adequate to secure its confidentiality, secrecy, integrity and safety, including from theft, loss, damage or destruction.
(2) Data controllers and data processors shall be subject to a duty of confidentiality and secrecy in respect of personal data in their possession or control.
(3) Without prejudice to the provisions of this section, a data controller or data processor shall, if the confidentiality, secrecy, integrity or safety of personal data in its possession or control is violated by theft, loss, damage or destruction, or as a result of any disclosure contrary to the provisions of this Act, or for any other reason whatsoever, notify the data subject, in such form and manner as may be prescribed, forthwith.
12. Regulation of disclosure of personal data. – Subject to section 10, section 13 and section 14, no person shall disclose, or otherwise cause any other person to receive, the content or nature of any personal data that has been collected in conformity with this Act.
13. Disclosure of personal data with prior informed consent. – (1) Subject to sub-section (2), a data controller or data processor seeking to disclose personal data under this section shall, prior to its disclosure, obtain the consent of the data subject.
(2) Prior to a disclosure of personal data under this section, the data controller or data processor, as the case may be, seeking to disclose the personal data, shall inform the data subject of the following details in respect of his personal data, namely: –
(a) when it will be disclosed;
(b) the purpose of its disclosure;
(c) the security practices, privacy policies and other policies, if any, that will protect it; and
(d) the procedure for recourse in case of any grievance in relation to it.
14. Disclosure of personal data without prior consent. – (1) Subject to sub-section (2), personal data may be disclosed without the prior consent of the data subject if it is necessary –
(a) to prevent a reasonable threat to national security, defence or public order; or
(b) to prevent, investigate or prosecute a cognisable offence.
(2) No data controller or data processor shall disclose any personal data unless it has received an order in writing from a police officer not below the rank of [___] in such form and manner as may be prescribed:
Provided that an order for the disclosure of personal data made under this sub-section shall not require the disclosure of any personal data that is not necessary to achieve the purpose for which the disclosure is sought:
Provided further that the data subject shall be notified, in such form and manner as may be prescribed, of the disclosure of his personal data, including details of its content and nature, and the identity of the police officer who ordered its disclosure, forthwith.
15. Quality and accuracy of personal data. – (1) Each data controller and data processor shall, to the extent possible, ensure that the personal data in its possession or control, is accurate and, where necessary, is kept up to date.
(2) No data controller or data processor shall deny a data subject whose personal data is in its possession or control the opportunity to review his personal data and, where necessary, rectify anything that is inaccurate or not up to date.
(3) A data subject may, if he finds personal data in the possession or control of a data controller or data processor that is not necessary to achieve the purpose for which it was collected, received or stored, demand its destruction, and the data controller shall destroy, or cause the destruction of, the personal data forthwith.
16. Special provisions for sensitive personal data. – Notwithstanding anything contained in this Act and the provisions of any other law for the time being in force –
(a) no person shall store sensitive personal data for a period longer than is necessary to achieve the purpose for which it was collected or received, or, if that purpose has been achieved or ceases to exist for any reason, for any period following such achievement or cessation;
(b) no person shall process sensitive personal data for a purpose other than the purpose for which it was collected or received;
(c) no person shall disclose sensitive personal data to another person, or otherwise cause any other person to come into the possession or control of, the content or nature of any sensitive personal data, including any other details in respect thereof.
CHAPTER IV
The Data Protection Authority
17. Constitution of the Data Protection Authority. – (1) The Central Government shall, by notification, constitute, with effect from such date as may be specified therein, a body to be called the Data Protection Authority consisting of a Chairperson and not more than four other Members, to exercise the jurisdiction and powers and discharge the functions and duties conferred or imposed upon it by or under this Act.
(2) The Chairperson shall be a person who has been a Judge of the Supreme Court:
Provided that the appointment of the Chairperson shall be made only after consultation with the Chief Justice of India.
(3) Each Member shall be a person of ability, integrity and standing who has a special knowledge of, and professional experience of not less than ten years in privacy law and policy.
18. Term of office, conditions of service, etc. of Chairperson and Members. – (1) Before appointing any person as the Chairperson or Member, the Central Government shall satisfy itself that the person does not, and will not, have any such financial or other interest as is likely to affect prejudicially his functions as such Chairperson or Member.
(2) The Chairperson and every Member shall hold office for such period, not exceeding five years, as may be specified in the order of his appointment, but shall be eligible for reappointment:
Provided that no person shall hold office as the Chairperson or Member after he has attained the age of sixty-seven years.
(3) Notwithstanding anything contained in sub-section (2), the Chairperson or any Member may –
(a) by writing under his hand resign his office at any time;
(b) be removed from office in accordance with the provisions of section 19 of this Act.
(4) A vacancy caused by the resignation or removal of the Chairperson or Member under sub-section (3) shall be filled by fresh appointment.
(5) In the event of the occurrence of a vacancy in the office of the Chairperson, such one of the Members as the Central Government may, by notification, authorise in this behalf, shall act as the Chairperson till the date on which a new Chairperson, appointed in accordance with the provisions of this Act, to fill such vacancy, enters upon his office.
(6) When the Chairperson is unable to discharge his functions owing to absence, illness or any other cause, such one of the Members as the Chairperson may authorise in writing in this behalf shall discharge the functions of the Chairperson, till the date on which the Chairperson resumes his duties.
(7) The salaries and allowances payable to and the other terms and conditions of service of the Chairperson and Members shall be such as may be prescribed:
Provided that neither the salary and allowances nor the other terms and conditions of service of the Chairperson and any member shall be varied to his disadvantage after his appointment.
19. Removal of Chairperson and Members from office in certain circumstances. – The Central Government may remove from office the Chairperson or any Member, who –
(a) is adjudged an insolvent; or
(b) engages during his term of office in any paid employment outside the duties of his office; or
(c) is unfit to continue in office by reason of infirmity of mind or body; or
(d) is of unsound mind and stands so declared by a competent court; or
(e) is convicted for an offence which in the opinion of the President involves moral turpitude; or
(f) has acquired such financial or other interest as is likely to affect prejudicially his functions as a Chairperson or Member, or
(g) has so abused his position as to render his continuance in offence prejudicial to the public interest.
20. Functions of the Data Protection Authority. – (1) The Chairperson may inquire, suo moto or on a petition presented to it by any person or by someone acting on his behalf, in respect of any matter connected with the collection, storage, processing, disclosure or other handling of any personal data and give such directions or pass such orders as are necessary for reasons to be recorded in writing.
(2) Without prejudice to the generality of the foregoing provision, the Data Protection Authority shall perform all or any of the following functions, namely –
(a) review the safeguards provided by or under this Act and other law for the time being in force for the protection of personal data and recommend measures for their effective implementation;
(b) review any measures taken by any entity for the protection of personal data and take such further action is it deems fit;
(c) review any action, policy or procedure of any entity to ensure compliance with this Act and any rules made hereunder;
(d) formulate, in consultation with experts, norms for the effective protection of personal data;
(e) promote awareness and knowledge of personal data protection through any means necessary;
(f) undertake and promote research in the field of protection of personal data;
(g) encourage the efforts of non-governmental organisations and institutions working in the field of personal data protection;
(h) publish periodic reports concerning the incidence of collection, processing, storage, disclosure and other handling of personal data;
(i) such other functions as it may consider necessary for the protection of personal data.
(3) Subject to the provisions of any rules prescribed in this behalf by the Central Government, the Data Protection Authority shall have the power to review any decision, judgement, decree or order made by it.
(4) In the exercise of its functions under this Act, the Data Protection Authority shall give such directions or pass such orders as are necessary for reasons to be recorded in writing.
(5) The Data Protection Authority may, in its own name, sue or be sued.
21. Secretary, officers and other employees of the Data Protection Authority. – (1) The Central Government shall appoint a Secretary to the Data Protection Authority to exercise and perform, under the control of the Chairperson such powers and duties as may be prescribed or as may be specified by the Chairperson.
(2) The Central Government may provide the Data Protection Authority with such other officers and employees as may be necessary for the efficient performance of the functions of the Data Protection Authority.
(3) The salaries and allowances payable to and the conditions of service of the Secretary and other officers and employees of the Data Protection Authority shall be such as may be prescribed.
22. Salaries, etc. be defrayed out of the Consolidated Fund of India. – The salaries and allowances payable to the Chairperson and Members and the administrative expenses, including salaries, allowances and pension, payable to or in respect of the officers and other employees of the of the Data Protection Authority shall be defrayed out of the Consolidated Fund of India.
23. Vacancies, etc. not to invalidate proceedings of the Data Protection Authority. – No act or proceeding of the Data Protection Authority shall be questioned on the ground merely of the existence of any vacancy or defect in the constitution of the Data Protection Authority or any defect in the appointment of a person acting as the Chairperson or Member.
24. Chairperson, Members and employees of the Data Protection Authority to be public servants. – The Chairperson and Members and other employees of the Data Protection Authority shall be deemed to be public servants within the meaning of section 21 of the Indian Penal Code, 1860 (45 of 1860).
25. Location of the office of the Data Protection Authority. – The offices of the Data Protection Authority shall be in [___] or any other location as directed by the Chairperson in consultation with the Central Government.
26. Procedure to be followed by the Data Protection Authority. – (1) Subject to the provisions of this Act, the Data Protection Authority shall have powers to regulate –
(a) the procedure and conduct of its business;
(b) the delegation to one or more Members of such powers or functions as the Chairperson may specify.
(2) In particular and without prejudice to the generality of the foregoing provisions, the powers of the Data Protection Authority shall include the power to determine the extent to which persons interested or claiming to be interested in the subject-matter of any proceeding before it may be allowed to be present or to be heard, either by themselves or by their representatives or to cross-examine witnesses or otherwise take part in the proceedings:
Provided that any such procedure as may be prescribed or followed shall be guided by the principles of natural justice.
27. Power relating to inquiries. – (1) The Data Protection Authority shall, for the purposes of any inquiry or for any other purpose under this Act, have the same powers as vested in a civil court under the Code of Civil Procedure, 1908 (5 of 1908), while trying suits in respect of the following matters, namely –
(a) the summoning and enforcing the attendance of any person from any part of India and examining him on oath;
(b) the discovery and production of any document or other material object producible as evidence;
(c) the reception of evidence on affidavit;
(d) the requisitioning of any public record from any court or office;
(e) the issuing of any commission for the examination of witnesses; and,
(f) any other matter which may be prescribed.
(2) The Data Protection Authority shall have power to require any person, subject to any privilege which may be claimed by that person under any law for the time being in force, to furnish information on such points or matters as, in the opinion of the Data Protection Authority, may be useful for, or relevant to, the subject matter of an inquiry and any person so required shall be deemed to be legally bound to furnish such information within the meaning of section 176 and section 177 of the Indian Penal Code, 1860 (45 of 1860).
(3) The Data Protection Authority or any other officer, not below the rank of a Gazetted Officer, specially authorised in this behalf by the Data Protection Authority may enter any building or place where the Data Protection Authority has reason to believe that any document relating to the subject matter of the inquiry may be found, and may seize any such document or take extracts or copies therefrom subject to the provisions of section 100 of the Code of Criminal Procedure, 1973 (2 of 1974), in so far as it may be applicable.
(4) The Data Protection Authority shall be deemed to be a civil court and when any offence as is described in section 175, section 178, section 179, section 180 or section 228 of the Indian Penal Code, 1860 (45 of 1860) is committed in the view or presence of the Data Protection Authority, the Data Protection Authority may, after recording the facts constituting the offence and the statement of the accused as provided for in the Code of Criminal Procedure, 1973 (2 of 1974), forward the case to a Magistrate having jurisdiction to try the same and the Magistrate to whom any such case is forwarded shall proceed to hear the complaint against the accused as if the case had been forwarded to him under section 346 of the Code of Criminal Procedure, 1973 (2 of 1974).
28. Decisions of the Data Protection Authority. – (1) The decisions of the Data Protection Authority shall be binding.
(2) In its decisions, the Data Protection Authority has the power to –
(a) require an entity to take such steps as may be necessary to secure compliance with the provisions of this Act;
(b) require an entity to compensate any person for any loss or detriment suffered;
(c) impose any of the penalties provided under this Act.
29. Proceedings before the Data Protection Authority to be judicial proceedings. – The Data Protection Authority shall be deemed to be a civil court for the purposes of section 195 and Chapter XXVI of the Code of Criminal Procedure, 1973 (2 of 1974), and every proceeding before the Data Protection Authority shall be deemed to be a judicial proceeding within the meaning of section 193 and section 228 and for the purposes of section 196 of the Indian Penal Code, 1860 (45 of 1860).
CHAPTER V
Regulation by Data Controllers and Data Processors
30. Co-regulation by Data Controllers and the Data Protection Authority. – (1) The Data Protection Authority may, in consultation with data controllers, formulate codes of conduct for the collection, storage, processing, disclosure or other handling of any personal data.
(2) No code of conduct formulated under sub-section (1) shall be binding on a data controller unless –
(a) it has received the written approval of the Data Protection Authority; and
(b) it has received the approval, by signature of a director or authorised signatory, of the data controller.
31. Co-regulation without prejudice to other remedies. – Any code of conduct formulated under this chapter shall be without prejudice to the jurisdiction, powers and functions of the Data Protection Authority.
32. Self-regulation by data controllers. – (1) The Data Protection Authority may encourage data controllers and data processors to formulate professional codes of conduct to establish rules for the collection, storage, processing, disclosure or other handling of any personal data.
(2) No code of conduct formulated under sub-section (1) shall be effective unless it is registered, in such form and manner as may be prescribed, by the Data Protection Authority.
(3) The Data Protection Authority shall, for reasons to be recorded in writing, not register any code of conduct formulated under sub-section (1) that is not adequate to protect personal data.
CHAPTER IV
Surveillance and Interception of Communications
33. Surveillance and interception of communication to be warranted. – Notwithstanding anything contained in any other law for the time being in force, no –
(i) surveillance shall be carried out, and no person shall order any surveillance of another person;
(ii) communication shall be intercepted, and no person shall order the interception of any communication of another person; save in execution of a warrant issued under section 36, or an order made under section 38, of this Act.
34. Application for issuance of warrant. – (1) Any authorised officer seeking to carry out any surveillance or intercept any communication of another person shall prefer an application for issuance of a warrant to the Magistrate.
(2) The application for issuance of the warrant shall be in the form and manner prescribed in the Schedule and shall state the purpose for which the warrant is sought.
(3) The application for issuance of the warrant shall be accompanied by –
(i) a report by the authorised officer of the suspicious conduct of the person in respect of whom the warrant is sought, and all supporting material thereof;
(ii) an affidavit of the authorised officer, or a declaration under his hand and seal, that the contents of the report and application are true to the best of his knowledge, information and belief, and that the warrant shall be executed only for the purpose stated in the application and shall not be misused or abused in any manner including to interfere in the privacy of any person;
(iii) details of all warrants previously issued in respect of the person in respect of whom the warrant is sought, if any.
35. Considerations prior to the issuance of warrant. – (1) No warrant shall issue unless the requirements of section 34 and this section have been met.
(2) The Magistrate shall consider the application made under section 34 and shall satisfy himself that the information contained therein sets out –
(i) a reasonable threat to national security, defence or public order; or
(ii) a cognisable offence, the prevention, investigation or prosecution of which is necessary in the public interest.
(3) The Magistrate shall satisfy himself that all other lawful means to acquire the information that is sought by the execution of the warrant have been exhausted.
(4) The Magistrate shall verify the identity of the authorised officer and shall satisfy himself that the application for issuance of the warrant is authentic.
36. Issue of warrant. – (1) Subject to section 34 and section 35, the Magistrate may issue a warrant for surveillance or interception of communication, or both of them.
(2) The Magistrate may issue the warrant in Chambers.
37. Magistrate may reject application for issuance of warrant. – If the Magistrate is not satisfied that the requirements of section 34 and section 35 have been met, he may, for reasons to be recorded in writing, –
(i) refuse to issue the warrant and dispose of the application;
(ii) return the application to the authorised officer without disposing of it;
(iii) pass any order that he thinks fit.
38. Order by Home Secretary in emergent circumstances. – (1) Notwithstanding anything contained in section 35, if the Home Secretary of the appropriate government is satisfied that a grave threat to national security, defence or public order exists, he may, for reasons to be recorded in writing, order any surveillance or interception of communication.
(2) An authorised officer seeking an order for surveillance or interception of communication under this section shall prefer an application to the Home Secretary in the form and manner prescribed in the Schedule and accompanied by the documents required under sub-section (3) of section 34.
(3) No order for surveillance or interception of communication made by the Home Secretary under this section shall be valid upon the expiry of a period of seven days from the date of the order.
(4) Before the expiry of a period of seven days from the date of an order for surveillance or interception of communication made under this section, the authorised officer who applied for the order shall place the application before the Magistrate for confirmation.
39. Duration of warrant or order. – (1) The warrant or order for surveillance or interception of communication shall specify the period of its validity and, upon its expiry, all surveillance and interception of communication, as the case may be, carried out in relation to that warrant or order shall cease forthwith:
Provided that no warrant or order shall be valid upon the expiry of a period of sixty days from the date of its issue.
(2) A warrant issued under section 36, or an order issued under section 38, for surveillance or interception of communication, or both of them, may be renewed by a Magistrate if he is satisfied that the requirements of sub-section (2) of section 35 continue to exist.
40. Duty to inform the person concerned. – Subject to sub-section (2), before the expiry of a period of sixty days from the conclusion of any surveillance or interception of communication carried out under this Act, the authorised officer who carried out the surveillance or interception of communication shall, in writing in such form and manner as may be prescribed, notify, with reference to the warrant of the Magistrate, and, if applicable, the order of the Home Secretary, each person in respect of whom the warrant or order was issued, of the fact of such surveillance or interception and duration thereof.
(2) The Magistrate may, on an application made by an authorised officer in such form and manner as may be prescribed, if he is satisfied that the notification under sub-section (1) would –
(a) present a reasonable threat to national security, defence or public order, or
(b) adversely affect the prevention, investigation or prosecution of a cognisable offence,
for reasons to be recorded in writing addressed to the authorised officer, order that the person in respect of whom the warrant or order of surveillance or interception of communication was issued, not be notified of the fact of such interception or the duration thereof:
41. Security and duty of confidentiality and secrecy. – (1) No person shall carry out any surveillance or intercept any communication of another person without implementing measures, including, but not restricted to, technological, physical and administrative measures, to secure the confidentiality and secrecy of all information obtained as a result of the surveillance or interception of communication, as the case may be, including from theft, loss or unauthorised disclosure.
(2) Any person who carries out any surveillance or interception of any communication, or who obtains any information, including personal data, as a result of surveillance or interception of communication, shall be subject to a duty of confidentiality and secrecy in respect of it.
(3) Every competent organisation shall, before the expiry of a period of one hundred days from the enactment of this Act, designate as many officers as it deems fit as Privacy Officers who shall be administratively responsible for all interceptions of communications carried out by that competent organisation.
42. Disclosure of information. – (1) Save as provided in this section, no person shall disclose to any other person, or otherwise cause any other person to come into the knowledge or possession of, the content or nature of any information, including personal data, obtained as a result of any surveillance or interception carried out under this Act.
(2) Notwithstanding anything contained in this section, if the disclosure of any information, including personal data, obtained as a result of any surveillance or interception of any communication is necessary to –
(a) prevent a reasonable threat to national security, defence or public order, or
(b) prevent, investigate or prosecute a cognisable offence,
an authorised officer may disclose the information, including personal data, to any authorised officer of any other competent organisation.
CHAPTER VI
Offences and penalties
43. Punishment for offences related to personal data. – (1) Whoever, except in conformity with the provisions of this Act, collects, receives, stores, processes or otherwise handles any personal data shall be punishable with imprisonment for a term which may extend to [___] years and may also be liable to fine which may extend to [___] rupees.
(2) Whoever attempts to commit any offence under sub section (1) shall be punishable with the punishment provided for such offence under that sub-section.
(3) Whoever, except in conformity with the provisions of this Act, collects, receives, stores, processes or otherwise handles any sensitive personal data shall be punishable with imprisonment for a term which may extend to [increased for sensitive personal data] years and and may also be liable to fine which may extend to [___] rupees.
(4) Whoever attempts to commit any offence under sub section (3) shall be punishable with the punishment provided for such offence under that sub-section.
44. Abetment and repeat offenders. – (1) Whoever abets any offence punishable under this Act shall, if the act abetted is committed in consequence of the abetment, be punishable with the punishment provided for that offence.
(2) Whoever, having been convicted of an offence under any provision of this Act is again convicted of an offence under the same provision, shall be punishable, for the second and for each subsequent offence, with double the penalty provided for that offence.
45. Offences by companies. – (1) Where an offence under this Act has been committed by a company, every person who, at the time of the offence was committed, was in charge of, and was responsible to, the company for the conduct of the business of the company, as well as the company shall be deemed to be guilty of the offence and shall be liable to be proceeded against and punished accordingly:
Provided that nothing contained in this sub-section shall render any such person liable to any punishment, if he proves that the offence was committed without his knowledge or that he had exercised all due diligence to prevent the commission of such offence.
(2) Notwithstanding anything contained in sub-section (1), where any offence under this Act has been committed by a company and it is proved that the offence has been committed with the consent or connivance of, or is attributable to any neglect on the part of any director, manager, secretary or other officer of the company, such director, manager, secretary or other officer shall be deemed to be guilty of that offence, and shall be liable to be proceeded against and punished accordingly.
46. Cognisance. – Notwithstanding anything contained in the Code of Criminal Procedure, 1973 (2 of 1974), the offences under section 43, section 44 and section 45 shall be cognisable and non-bailable.
47. General penalty. – Whoever, in any case in which a penalty is not expressly provided by this Act, fails to comply with any notice or order issued under any provisions thereof, or otherwise contravenes any of the provisions of this Act, shall be punishable with fine which may extend to [___] rupees, and, in the case of a continuing failure or contravention, with an additional fine which may extend to [___] rupees for every day after the first during which he has persisted in such failure or contravention.
48. Punishment to be without prejudice to any other action. – The award of punishment for an offence under this Act shall be without prejudice to any other action which has been or which may be taken under this Act with respect to such contravention.
CHAPTER VII
Miscellaneous
49. Power to make rules. – (1) The Central Government may, by notification in the Official Gazette, make rules to carry out the provisions of this Act.
(2) In particular, and without prejudice to the generality of the foregoing power, such rules may provide for –
[__]
(3) Every rule made under this section shall be laid, as soon as may be after it is made, before each House of Parliament while it is in session for a period of thirty days which may be comprised in one session or in two successive sessions and if before the expiry of the session in which it is so laid or the session immediately following, both Houses agree in making any modification in the rule, or both Houses agree that the rule should not be made, the rule shall thereafter have effect only in such modified form or be of no effect, as the case may be, so however, that any such modification or annulment shall be without prejudice to the validity of anything previously done under that rule.
50. Bar of jurisdiction. – (1) On and from the appointed day, no court or authority shall have, or be entitled to exercise, any jurisdiction, powers or authority (except the Supreme Court and a High Court exercising powers under Article 32, Article 226 and Article 227 of the Constitution) in relation to matters specified in this Act.
(2) No order passed under this Act shall be appealable except as provided therein and no civil court shall have jurisdiction in respect of any matter which the Data Protection Authority is empowered by, or under, this Act to determine and no injunction shall be granted by any court or other authority in respect of any action taken or to be taken in pursuance of any power conferred by or under this Act.
51. Protection of action taken in good faith. – No suit or other legal proceeding shall lie against the Central Government, State Government, Data Protection Authority, Chairperson, Member or any person acting under the direction either of the Central Government, State Government, Data Protection Authority, Chairperson or Member in respect of anything which is in good faith done or intended to be done in pursuance of this Act or of any rules or any order made thereunder.
52. Power to remove difficulties. – (1) If any difficulty arises in giving effect to the provisions of this Act, the Central Government may, by order, published in the Official Gazette, make such provisions, not inconsistent with the provisions of this Act, as appears to it to be necessary or expedient for removing the difficulty:
Provided that no such order shall be made under this section after the expiry of a period of three years from the commencement of this Act.
(2) Every order made under this section shall be laid, as soon as may be after it is made, before each House of Parliament.
53. Act to have overriding effect. – The provisions of this Act shall have effect notwithstanding anything inconsistent therewith contained in any other law for the time being in force.
US Privacy FTC
 US-FTC Privacy Overview (India 2013).pdf
—
PDF document,
1628 kB (1668070 bytes)
US-FTC Privacy Overview (India 2013).pdf
—
PDF document,
1628 kB (1668070 bytes)
A Privacy Meeting with the Federal Trade Commission in New Delhi
As a note, thoughts shared during the meeting represented personal perspectives, and did not constitute the official position of the Federal Trade Commission.
When explaining the U.S regulatory framework for privacy the FTC attorneys highlighted that the United States does not have comprehensive privacy legislation, like in Europe, but instead has sectoral laws that address different aspects of privacy. For example, the Fair Credit Reporting Act maintains confidentiality of consumer credit report information, the Gramm Leach Bliley Act imposes privacy and security requirements for financial institutions, HIPAA applies to patient health information, and the Children’s Online Privacy Protection Act prevents the collection and posting of personal information from minors. It was discussed that the sectoral model followed by the United States allows for a nuanced balance to be struck between privacy protection and the market. It was noted, however, that some have critiqued the U.S. regulatory framework for lacking clear principles that apply to the commercial world and lay out strong privacy protections for the individual. In light of this, the White House is developing a Privacy Bill of Rights.
The Federal Trade Commission is an independent agency in the United States Government with responsibility for enforcing both consumer protection and competition laws. It is composed of five commissioners, and a staff of roughly 1,000, which includes attorneys and economists. The FTC is primarily a law enforcement agency, but also undertakes policy development through workshops and reports, Consumer education is another key function of the agency.
On the consumer protection side, Congress has directed the FTC to enforce the Federal Trade Commission Act, as well as some more specific statutes, such as those that protect consumers from unwanted telemarketing laws, and the protection of children on line. Its main objectives are to protect consumer interests, and prevent fraud and unfair and deceptive business practices. The FTC carries out its privacy work through its consumer protection mission.
When understanding the FTC’s role in relation to privacy, it is important to understand that the FTC’s jurisdiction applies only to certain industries as defined by Congress. Thus, for example, the FTC does not have jurisdiction over banks or telecommunications.
The most critical part of the FTC’s activities is its law enforcement function. The FTC can investigate an organization if the staff believes that the entity may be involved in conduct that contravenes the FTC Act’s prohibition on unfair or deceptive practices, or another specific privacy law. The FTC has brought a number of privacy-related cases against major companies including Facebook, Google, ChoicePoint, and Twitter. Many of these cases address new challenges brought about by rapidly changing technologies.
The vast majority of the FTC’s actions have been settled with consent judgments. When the statute that the FTC enforces allows for the imposition of a civil penalty, the FTC sets the penalty at a level that ensures that it is fair and provides a deterrent, but will not impose a hardship on the company. As a civil enforcement agency, the FTC cannot seek criminal sanctions. While enforcement is the cornerstone of the FTC’s approach to privacy, the agency also supports self-regulation, where appropriate. In this system the FTC does not pre-approve an organization’s practices or define principles that all companies should abide by as it is felt that every organization is unique and has different needs and abilities, and assigning specific technical standards may stifle innovation.
In the meeting it was also discussed how US privacy laws may apply to overseas companies where they are providing services for US consumers or working on behalf of US companies. For example, under the Gramm Leach Bliley Act the FTC has created the Safeguards Rule, which speaks to how financial data by financial institutions must be handled and protected. This Rule applies to companies overseas if the company is performing work for US companies or US consumers. In other words, a US company cannot avoid compliance by outsourcing its work to an off shore organization. Discussions during the meeting also focused on consent and the key role that context, accessibility, and timing play in ensuring individuals have the ability to provide informed consent. Some of the attendees suggested that this practice could be greatly improved in India. For example, currently in India there are companies that only provide consumers access to the company privacy policy after an individual has consented and signed up to the service. When asked about the challenges to privacy that exist in India, many shared that, culturally, there is a different understanding of privacy in India than in many western countries.
Other thoughts included that the Indian government is currently imagining privacy regulation as being either fluid and purely self regulatory or being enforced through strict legal provisions. Instead, the government needs to begin to expand the possibilities for a regulatory framework for privacy in India in such a way that allows for strong legal enforcement, and flexible standards. The right to be forgotten was also discussed and it was mentioned that California has proposed a law that will allow individuals to request deletion of information.
CPR South 1
 CPR South 1.pdf
—
PDF document,
221 kB (226687 bytes)
CPR South 1.pdf
—
PDF document,
221 kB (226687 bytes)
CPR South 2
 CPR South 2.pdf
—
PDF document,
163 kB (167757 bytes)
CPR South 2.pdf
—
PDF document,
163 kB (167757 bytes)
An Analysis of the Cases Filed under Section 46 of the Information Technology Act, 2000 for Adjudication in the State of Maharashtra
Background
Section 46 of the Act grants the Central Government the power to appoint an adjudicating officer to hold an enquiry to adjudge, upon complaints being filed before that adjudicating officer, contraventions of the Act. The adjudicating officer may be of the Central Government or of the State Government [see section 46(1) of the Act], must have field experience with information technology and law [see section 46(3) of the Act] and exercises jurisdiction over claims for damages up to `5,00,00,000 [see section 46(1A) of the Act]. For the purpose of adjudication, the officer is vested with certain powers of a civil court [see section 46(5) of the Act] and must follow basic principles of natural justice while conducting adjudications [see section 46(2) of the Act]. Hence, the adjudicating officer appointed under section 46 is a quasi-judicial authority.
In addition, the quasi-judicial adjudicating officer may impose penalties, thereby vesting him with some of the powers of a criminal court [see section 46(2) of the Act], and award compensation, the quantum of which is to be determined after taking into account factors including unfair advantage, loss and repeat offences [see section 47 of the Act]. The adjudicating officer may impose penalties for any of the offences described in section 43, section 44 and section 45 of the Act; and, further, may award compensation for losses suffered as a result of contraventions of section 43 and section 43A. The text of these sections is reproduced in the Schedule below. Further law as to the appointment of the adjudicating officer and the procedure attendant on all adjudications was made by Information Technology (Qualification and Experience of Adjudicating Officers and the Manner of Holding Enquiry) Rules, 2003.[1]
It is clear that the adjudicating officer is vested with significant judicial powers, including the power to enforce certain criminal penalties, and is an important quasi-judicial authority.
Excursus
At the outset, it is important to understand the distinction between compensation and damages. Compensation is a sum of money awarded by a civil court, before or along with the primary decree, to indemnify a person for injury or loss. It is usually awarded to a person who has a suffered a monetary loss as a result of the acts or omissions of another party. Its quantification is usually guided by principles of equity. [See Shantilal Mangaldas AIR 1969 SC 634 and Ranbir Kumar Arora AIR 1983 P&H 431]. On the hand, damages are punitive and, in addition to restoring an indemnitee to wholeness, may be imposed to deter an offender, punish exemplary offences, and recover consequential losses, amongst other objectives. Damages that are punitive, while not judicially popular in India, are usually imposed by a criminal court in common law jurisdictions. They are distinct from civil and equitable actions. [See the seminal case of The Owners of the Steamship Mediana [1900] AC 113 (HL)].
Unfortunately, section 46 of the Act uses the terms “damage”, “injury” and “compensation” interchangeably without regard for the long and rich jurisprudence that finds them to be different concepts.
The Cases related to Privacy
In the State of Maharashtra, there have been a total of 47 cases filed under section 46 of the Act. Of these, 33 cases have been disposed of by the Adjudicating Officer and 14 are currently pending disposal. [2] At least three of these cases before the Adjudicating Officer deal with issues related to privacy of communications and personal data. They are:
| Case Title | Forum | Date |
|---|---|---|
|
Vinod Kaushik v. Madhvika Joshi |
Shri Rajesh Aggarwal Adjudicating Officer, ex-officio Secretary, IT Government of Maharashtra |
10.10.2011 |
| Amit D. Patwardhan v. Rud India Chains | Shri Rajesh Aggarwal Adjudicating Officer, ex-officio Secretary, IT Government of Maharashtra |
15.04.2013 |
| Nirmalkumar Bagherwal v. Minal Bagherwal | Shri Rajesh Aggarwal Adjudicating Officer, ex-officio Secretary, IT Government of Maharashtra |
26.08.2013 |
In all three cases the Adjudicating Officer was called upon to determine and penalise unauthorised access to personal data of the complainants. In the Vinod Kaushik case, the complainants’ emails and chat sessions were accessed, copied and made available to the police for legal proceedings without the permission of the complainants. In the Amit Patwardhan and Nirmalkumar Bagherwal cases, the complainants’ financial information in the form of bank account statements were obtained from their respective banks without their consent and used against them in legal proceedings.
The Vinod Kaushik complaint was filed in 2010 for privacy violations committed between 2008 and 2009. The complaint was made against the complainant’s daughter-in-law – the respondent, who was estranged from her husband, the complainant’s son. The respondent had, independent of the proceedings before the Adjudicating Officer, instituted criminal proceedings alleging cruelty and dowry-related harassment against her estranged husband and the complainant. To support some of the claims made in the criminal proceedings, the respondent accessed the email accounts of her estranged husband and the complainant and printed copies of certain communications, both emails and chat transcripts. The complaint to the Adjudicating Officer was made in relation to these emails and chat transcripts that were obtained without the consent and knowledge of the complainant and his son. On 09.08.2010, the then Adjudicating Officer dismissed the complaint after finding that, owing to the marriage between the respondent and the complainant’s son, there was a relation of mutual trust between them that resulted in the complainant and his son consensually sharing their email account passwords with the respondent. This ruling was appealed to the Cyber Appellate Tribunal ("CyAT") which, in a decision of 29.06.2011, found irregularities in the complainant’s son’s privity to the proceedings and remanded the complaint to the Adjudicating Officer for re-adjudication. The re-adjudication, which was conducted by Shri Rajesh Aggarwal as Adjudicating Officer, resulted in a final order of 10.10.2011 ("the final order") that is the subject of this analysis. The final order found that the respondent had violated the privacy of the complainant and his son by her unauthorised access of their email accounts and sharing of their private communications. However, the Adjudicating Officer found that the intent of the unauthorised access – to obtain evidence to support a criminal proceeding – was mitigatory and hence ordered the respondent to pay only a small token amount in compensation, not to the complainants but instead to the State Treasury. The Delhi High Court, which was moved in appeal because the CyAT was non-functional, upheld the final order in its decision of 27.01.2012.
The Amit Patwardhan complaint was filed against the complainant’s ex-employer – the respondent, for illegally obtaining copies of the complainant’s bank account statement. The complainant had left the employ of the respondent to work with a competing business company but not before colluding with the competing business company and diverting the respondent’s customers to them. For redress, the respondent filed suit for a decree of compensation and lead the complainant’s bank statements in evidence to prove unlawful gratification. Since the bank statements were obtained electronically by the respondent without the complainant’s consent, the jurisdiction of the Adjudicating Officer was invoked. In his order of 15.04.2013, Shri Rajesh Aggarwal, the Adjudicating Officer, found that the respondent had, by unlawfully obtaining the complainant’s bank account statements which constitute sensitive personal data, violated the complainant’s privacy. The Adjudicating Officer astutely applied the equitable doctrine of clean hands to deny compensation to the complainant; however, because the complainant’s bank was not a party to the complaint, the Adjudicating Officer was unable to make a ruling on the lack of action by the bank to protect the sensitive personal data of its depositors.
The Nirmalkumar Bagherwal complaint bears a few similarities to the preceding two cases. Like the Vinod Kaushik matter, the issue concerned the manner in which a wife, estranged but still legally married, accessed electronic records of personal data of the complainants; and, like the Amit Patwardhan matter, the object of the privacy violation was the bank account statements of the complainants that constitute sensitive personal data. The respondent was the estranged wife of one of the complainants who, along with his complainant father, managed the third complainant company. To support her claim for maintenance from the complainant and his family in an independent legal proceeding, the respondent obtained certain bank account statements of the complainants without their consent and, possibly, with the collusion of the respondent bank. After reviewing relevant law from the European Union and the United States, and observant of relevant sectoral regulations applicable in India including the relevant Master Circular of the Reserve Bank of India, and further noting preceding consumer case law on the subject, the Adjudicating Officer issued an order on 26.08.2013. The order found that the complainant’s right to privacy was violated by both the respondents but, while determining the quantum of compensation, distinguished between the respondents in respect of the degree of liability; the respondent wife was ordered to pay a token compensation amount while the respondent bank was ordered to pay higher compensation to each of the three complainants individually.
The high quality of each of the three orders bears specific mention. Despite the superb quality of the judgments of the Indian higher judiciary in the decades after independence, the overall quality of judgment-writing appears to have declined. [3] In the last decade, several Indian judges have called for higher standards of judgment writing from their fellow judges. [4] In this background, it is notable that Shri Rajesh Aggarwal, despite not being a member of the judiciary, has delivered well-reasoned, articulate and clear orders that are cognisant of legal issues and also easily understandable to a non-legal reader.
In each of these cases, the Adjudicating Officer has successfully navigated around the fact that none of the primary parties were interacting and transacting at arm’s length. In the Vinod Kaushik and Nirmalkumar Bagherwal matters, the primary parties were estranged but still legally married partners and in the Amit Patwardhan matter the parties were in an employer-employee relationship. The first Adjudicating Officer in the Vinod Kaushik matter failed, in his order of 09.08.2010, to appreciate that the individual communications of individual persons were privileged by an expectation of privacy, regardless of their relationship. Hence, despite acknowledging that the marital partners in that matter were in conflict with each other, and despite being told by one party that the other party’s access to those private communications was made without consent, the Adjudicating Officer allowed his non-judicial opinion of marriage to influence his order. This mistake was corrected when the matter was remanded for re-adjudication. In the re-adjudication, the new Adjudicating Officer correctly noted that the respondent wife could have chosen to approach the police or a court to follow the proper investigative procedure for accessing emails and other private communications of another person and that her unauthorised use of the complainant’s passwords amounted to a violation of their privacy.
Popular conceptions of different types of relationships may affect the (quasi) judicial imagination of privacy. In comparison to the Vinod Kaushik matter, the Nirmalkumar Bagherwal and Amit Patwardhan matters both dealt with unauthorised access to bank account statements, by a wife and by an ex-employer respectively. In any event, the same Adjudicating Officer presided over all three matters and correctly found that the facts in all three matters admitted to contraventions of the privacy of the complainants. The conjecture as to whether the first Adjudicating Officer in the Vinod Kaushik matter would have applied the same standard of family unity to unauthorised access of bank account statements by an estranged wife who was seeking maintenance remains untested. However, the reliance placed on the decision of the Delhi State Consumer Protection Commission in the matter of Rupa Mahajan Pahwa, [5] where the Commission found that unauthorised access to a bank pass book by an estranged husband violated the privacy of the wife, would suggest that judges clothe financial information with a standard of privacy higher than that given to emails.
Emails are a form of electronic communication. The PUCL case (Supreme Court of India, 1996)[6] while it did not explicitly deal with the standard of protection accorded to emails, held that personal communications were protected by an individual right to privacy that emanated from the protection of personal liberty guaranteed under Article 21 of the Constitution of India. Following the Maneka Gandhi case (Supreme Court of India, 1978)[7]
it is settled that persons may be deprived of their personal liberty only by a just, fair and reasonable procedure established by law. As a result, interceptions of private communications that are protected by Article 21 may only be conducted in pursuance of such a procedure. This procedure exists in the form of the Information Technology (Procedure and Safeguards for Interception, Monitoring and Decryption of Information) Rules, 2009 that came into effect on 27 October 2009 ("the Interception Rules"). The Interception Rules set out a regime for accessing private emails in certain conditions. The powers and procedure of Section 91 of the Code of Criminal Procedure ("CrPC") may also apply to obtain data at rest, such as emails stored in an inbox or sent-mail folder.
Finally, the orders of the Adjudicating Officer reveal a well-reasoned and progressive understanding of the law and principles relating to the quantification of compensation. By choosing to impose larger amounts of compensation on the bank that violated the privacy of the complainant in the Nirmalkumar Bagherwal matter, the Adjudicating Officer has indicated that the institutions that hold sensitive personal data, such as financial information, are subject to a higher duty of care in relation of it. But, most importantly, the act of imposing monetary compensation of privacy violations is a step forward because, for the first time in India, it recognises that privacy violations are civil wrongs or injuries that demand compensation.
[1]. These Rules were issued vide GSR 220(E), dated 17 March 2003 and published in the Gazette of India, Extraordinary, Part II, Section 3(i). These Rules can be accessed here – http://it.maharashtra.gov.in/PDF/Qual_ExpAdjudicatingOfficer_Manner_of_Holding_Enquiry_Rules.PDF (visited on 30 September 2013).
[2]. These cases and statistics may be viewed here – http://it.maharashtra.gov.in/1089/IT-Act-Judgements (visited on 30 September 2013).
[3]. See generally, Upendra Baxi “"The Fair Name of Justice": The Memorable Voyage of Chief Justice Chandrachud” in A Chandrachud Reader (Justice V. S. Deshpande ed., Delhi: Documentation Centre etc., 1985) and, Rajeev Dhavan, "Judging the Judges" in Judges and the Judicial Power: Essays in Honour of Justice V. R. Krishna Iyer (Rajeev Dhavan and Salman Khurshid eds., London: Sweet & Maxwell, 1985).
[4]. See generally, Justice B.G .Harindranath, Art of Writing Judgments (Bangalore: Karnataka Judicial Academy, 2004); Justice T .S. Sivagnanam, The Salient Features of the Art of Writing Orders and Judgments (Chennai: Tamil Nadu State Judicial Academy, 2010); and, Justice Sunil Ambwani, “Writing Judgments: Comparative Models” Presentation at the National Judicial Academy, Bhopal (2006) available here – http://districtcourtallahabad.up.nic.in/articles/writing%20judgment.pdf (visited on 29 Sep 2013).
[5]. Appeal No. FA-2008/659 of the Delhi State Consumer Protection Commission, decided on 16 October 2008.
[6]. (1997) 1 SCC 301.
[7]. (1978) 1 SCC 248.
CIS Cybersecurity Series (Part 11) - Anja Kovacs
"Having the cyber security debate become more and more important was a real challenge for civil society. I think in part because many of us who were focused on human rights aren't necessarily techies. And so, when you have a conversation with a government bureaucrat, and ask questions about the kind of decisions they decided to take, very often they will come up with a technical answer in response. And then, if you don't have that expertise, it is difficult to react. In the meantime though, I think it has become clear that this is one of the biggest issues in the internet field at the moment. It is also one of the big issues that is driving the desires of governments to have a bigger role to play in internet governance. So it is an area that is unavoidable for activists. What has happened slowly is that we have come to realize that the first thing, as in most other areas, is not the technical details, but principles, and those principles are fairly similar to how they are in many other fields." - Anja Kovacs, Internet Democracy Project
Centre for Internet and Society presents its eleventh installment of the CIS Cybersecurity Series.
The CIS Cybersecurity Series seeks to address hotly debated aspects of cybersecurity and hopes to encourage wider public discourse around the topic.
In this installment, CIS speaks to Anja Kovacs, director of the Internet Democracy Project. Her work focuses on a wide range of questions regarding freedom of expression, cybersecurity and the architecture of Internet governance as they relate to the Internet and democracy. Anja is currently also a member of the of the Investment Committee of the Digital Defenders Partnership and of the interim Steering Group of Best Bits, a global network of civil society members.
(Bio from internetdemocracy.in)
Internet Democracy Project homepage: http://internetdemocracy.in/
This work was carried out as part of the Cyber Stewards Network with aid of a grant from the International Development Research Centre, Ottawa, Canada.
The India Privacy Monitor Map
In a country of twenty-eight diverse states and seven union territories, it remained unclear to what extent surveillance, biometric and other privacy-intrusive schemes are being implemented. We are trying to make up for this by mapping out data in every single state in India on the UID, CCTNS and NPR schemes, as well as on the installation of CCTV cameras and the use of Unmanned Aerial Vehicles (UAVs), otherwise known as drones.
In particular, the map in its current format includes data on the following:
UID: The Unique Identification Number (UID), also known as AADHAAR, is a 12-digit unique identification number which the Unique Identification Authority of India (UIDAI) is currently issuing for all residents in India (on a voluntary basis). Each UID is stored in a centralised database and linked to the basic demographic and biometric information of each individual. The UIDAI and AADHAAR currently lack legal backing.
NPR: Under the National Population Register (NPR), the demographic data of all residents in India is collected on a mandatory basis. The Unique Identification Authority of India (UIDAI) supplements the NPR with the collection of biometric data and the issue of the AADHAAR number.
CCTV: Closed-circuit television cameras which can produce images or recordings for surveillance purposes.
UAV: Unmanned Aerial Vehicles (UAVs), otherwise known as drones, are aircrafts without a human pilot on board. The flight of a UAV is controlled either autonomously by computers in the vehicle or under the remote control of a pilot on the ground or in another vehicle. UAVs are used for surveillance purposes.
CCTNS: The Crime and Criminal Tracking Networks and Systems (CCTNS) is a nationwide networking infrastructure for enhancing efficiency and effectiveness of policing and sharing data among 14,000 police stations across India.
Our India Privacy Monitor Map can be viewed through the following link: http://cis-india.org/cisprivacymonitor
This map is part of on-going research and will hopefully expand to include other schemes and projects which are potentially privacy-intrusive. We encourage all feedback and additional data!
Interview with Big Brother Watch on Privacy and Surveillance
For all those of you who haven't heard of Big Brother Watch, it's a London-based campaign group which was founded in 2009 to protect individual privacy and defend civil liberties.
Big Brother Watch was set up to challenge policies that threaten our privacy, our freedoms and our civil liberties, and to expose the true scale of the surveillance state. The campaign group has produced unique research exposing the erosion of civil liberties in the UK, looking at the dramatic expansion of surveillance powers, the growth of the database state and the misuse of personal information. Big Brother Watch campaigns to give individuals more control over their personal data, and hold to account those who fail to respect our privacy, whether private companies, government departments or local authorities.
Emma Carr joined Big Brother Watch as Deputy Director in February 2012 and has since been regularly quoted in the UK press. The Centre for Internet and Society interviewed Emma Carr on the following questions:
-
How do you define privacy?
-
Can privacy and freedom of expression co-exist? Why/Why not?
-
What is the balance between Internet freedom and surveillance?
-
According to your research, most people worldwide care about their online privacy – yet they give up most of it through the use of social networking sites and other online services. Why, in your opinion, does this occur and what are the potential implications?
-
Should people have the right to give up their right to privacy? Why/Why not?
-
What implications on human rights can mass surveillance potentially have?
-
“I'm not a terrorist and I have nothing to hide...and thus surveillance can't affect me personally.” Please comment.
-
Do we have Internet freedom?
VIDEO
Interview with Bruce Schneier - Internationally Renowned Security Technologist
Bruce Schneier is an internationally renowned security technologist, called a "security guru" by The Economist.
He is the author of 12 books -- including Liars and Outliers: Enabling the Trust Society Needs to Survive -- as well as hundreds of articles, essays, and academic papers. His influential newsletter "Crypto-Gram" and his blog "Schneier on Security" are read by over 250,000 people. He has testified before Congress, is a frequent guest on television and radio, has served on several government committees, and is regularly quoted in the press.
Schneier is a fellow at the Berkman Center for Internet and Society at Harvard Law School, a program fellow at the New America Foundation's Open Technology Institute, a board member of the Electronic Frontier Foundation, an Advisory Board Member of the Electronic Privacy Information Center, and the Security Futurologist for BT -- formerly British Telecom.
The Centre for Internet and Society (CIS) interviewed Bruce Schneier on the following questions:
-
Do you think India needs privacy legislation? Why/ Why not?
-
The majoity of India's population lives below the line of poverty and barely has any Internet access. Is surveillance an elitist issue or should it concern the entire population in the country? Why/ Why not?
-
“I'm not a terrorist and I have nothing to hide...and thus surveillance can't affect me personally.” Please comment.
-
Can free speech and privacy co-exist? What is the balance between privacy and freedom of expression?
-
Should people have the right to give up their right to privacy? Why/ Why not?
-
Should surveillance technologies be treated as traditional arms/weapons? Why/ Why not?
-
How can individuals protect their data (and themselves) from spyware, such as FinFisher?
-
How would you advise young people working in the surveillance industry?
VIDEO
Interview with the Tactical Technology Collective on Privacy and Surveillance
For all those of you who haven't heard of the Tactical Technology Collective, it's a Berlin and Bangalore-based non-profit organisation which aims to advance the skills, tools and techniques of rights advocates, empowering them to use information and communications to help marginalised communities understand and effect progressive social, environmental and political change.
Tactical Tech's Privacy & Expression programme builds the digital security awareness and capacity of human rights defenders, independent journalists, anti-corruption advocates and activists. The programme's activities range from awareness-raising comic films aimed at audiences new to digital security issues, to direct training and materials for high-risk defenders working in some of the world's most repressive environments.
Anne Roth works with Tactical Tech on the Privacy & Expression programme as a researcher and editor. Anne holds a degree in political science from the Free University of Berlin. She cofounded one of the first interactive media activist websites, Indymedia, in Germany in 2001 and has been involved with media activism and various forms of activist online media ever since. She has worked as a web editor and translator in the past. Since 2007 she has written a blog that covers privacy, surveillance, media, net politics and feminist issues.
The Centre for Internet and Society interviewed Anne Roth on the following questions:
-
How do you define privacy?
-
Can privacy and freedom of expression co-exist? Why/ Why not?
-
What is the balance between Internet freedom and surveillance?
-
According to research, most people worldwide care about their online privacy – yet they give up most of it through the use of social networking sites and other online services. Why, in your opinion, does this occur and what are the potential implications?
-
Should people have the right to give up their right to privacy? Why/ Why not?
-
What implications on human rights can mass surveillance potentially have?
-
“I'm not a terrorist and I have nothing to hide...and thus surveillance can't affect me personally”. Please comment.
-
Do we have Internet freedom?
VIDEO
Tweets from Bali IGF 2013
To enable research by those who don't want to mess around with Twitter's APIs, we are making available CSV files available to the general public. These files can be opened up in any spreadsheet software (including web-based ones), or even in a text editor.
These files will be updated with the latest version at the end of each evening in Bali.
If you have any ideas as to other keywords we should capture, or about visualizations that we should engage in, do get in touch with pranesh AT cis-india DOT org.
Open Letter to Members of the European Parliament of the Civil Liberties, Justice and Home Affairs Committee
Dear Members of the European Parliament of the Civil Liberties, Justice and Home Affairs Committee,
On behalf of The Centre for Internet and Society, Bangalore, India, we are writing to express our support of the European Commission’s proposed General Data Protection Regulation (COM (2012) 11).
The legal framework established under the 1995 Data Protection Directive (95/46/EC) in Europe has positively influenced many existing privacy regimes worldwide, serving as a model legal framework in jurisdictions that are in the process of developing privacy regimes, including India. The positive impact of the Data Protection Directive shows the potential of the Regulation to become a global model for the protection of personal data. The Regulation seeks to address new scenarios that have arisen in the context of rapidly changing technologies and practices, increasing its potential for positively influencing privacy rights for individuals globally.
India is currently in the process of considering the enactment of privacy legislation, in part with the aim of ensuring adequate safeguards to enable and enhance information flows into India from countries around the world, including Europe. At the same time, India is seeking Data Secure Status from the EU, on the basis of its current regime.
It is clear that the EU framework for data protection has a major influence on the current and emerging privacy regime in India. India is only one country of many that are in the beginning stages of developing a comprehensive privacy regime. Thus, we ask that you keep in mind how the Regulation will impact the rights of individual in countries outside of Europe, particularly in countries that are in the process of developing privacy regimes.
We ask that you take into consideration the four following points that we believe need to be addressed in the Regulation to help ensure adequate protection of the rights of individuals in the European Union and around the world.
- Strengthen the principle of purpose limitation: The Regulation should incorporate a strong purpose limitation principle that strictly limits present and future uses of personal data to the purposes for which it was originally collected. Currently, Article 6(4) allows for the further processing of data when the processing is “not compatible with the one for which the personal data have been collected”. Though the provision establishes legal requirements, one of which must be before information can be used for a further purpose, this is has proven insufficient in the existing Directive. The current provision in the Regulation dilutes the principle of purpose limitation as well as weakening an individual’s ability to make informed decisions about their personal data.
- Define principles for interpretation of broad terms: The Regulation should create principles for interpreting broad terms such as “legitimate interest” and “public interest”. These vague terms are used throughout the Regulation, and create the potential for loopholes or abuse. Because these terms can be interpreted in many different ways, it is important to create a set of principles to guide their interpretation by data protection authorities and courts to avoid inconsistent application and enforcement of the Regulation.
- Clarify the scope of the Regulation: The Regulation should clearly describe the jurisdictional scope and reach of its provisions. Currently Article 3(1) states that the Regulation will apply to the processing of data “in the context of the activities of an establishment of a controller or a processor in the Union”. The flow of information on the online environment coupled with trends such as cloud computing, outsourcing, and cross border business creates a scenario where defining what constitutes “context of the activities of an establishment”, is difficult and could lead to situations where personal data is not protected, as the collection, use, or storage of it does not necessarily fall within the “context of the activities”.
- Address access by foreign alliance bodies: In light of growing demands by law enforcement for access, use, and transfer of personal information for investigative purposes across jurisdictions– the Regulation should define the circumstances in which personal data protected by its provisions can be accessed and used by foreign intelligence bodies, and the procedure by which to do so. The Regulation should address challenges such as access by foreign intelligence bodies to data stored on the cloud and data that has passed through/is stored on foreign networks/servers.
Interview with Dr. Alexander Dix - Berlin Data Protection and Freedom of Information Commissioner
Dr. Alexander Dix has been Berlin's Data Protection and Freedom of Information Commissioner since June 2005. He has more than 26 years of practical experience in German data protection authorities and previously served as Commissioner for the state of Bradenburg for seven years.
Dr. Dix is a specialist in telecommunications and media and has dealt with a number of issues regarding the cross-border protection of citizen’s privacy. He chairs the International Working Group on Data Protection in Telecommunications (“Berlin Group”) and is a member of the Article 29 Working Party of European Data Protection Supervisory Authorities. In this Working Party he represents the Data Protection Authorities of the 16 German States (Länder).
A native of Bad Homburg, Hessen, Dr. Alexander Dix graduated from Hamburg University with a degree in law in 1975. He received a Master of Laws degree from the London School of Economics and Political Science in 1976 and a Doctorate in law from Hamburg University in 1984. He has published extensively on issues of data protection and freedom of information. Inter alia he is a co-editor of the German Yearbook on Freedom of Information and Information Law.
The Centre for Internet and Society interviewed Dr. Alexander Dix on the following questions:
-
What activities and functions does the Berlin data commissioner's office undertake?
-
What powers does the Berlin data commissioner's office have? In your opinion, are these sufficient? Which powers have been most useful? If there is a lack, what would you feel is needed?
-
How is the office of the Berlin Data Protection Commissioner funded?
-
What is the organisational structure at the Office of the Berlin Data Protection Commissioner and the responsibilities of the key executives?
-
If India creates a Privacy Commissioner, what structure/framework would you suggest for the office?
-
What challenges has your office faced?
-
What is the most common type of privacy violation that your office is faced with?
-
Does your office differ from other EU data protection commissioner offices?
-
How do you think data should be regulated in India?
-
Do you support the idea of co-regulation or self-regulation?
-
How can India protect its citizens' data when it is stored in foreign servers?
VIDEO
An Interview with Jacob Kohnstamm, Dutch Data Protection Authority and Chairman of the Article 29 Working Party
What activities and functions does your office undertake?
The activities and functions of the Dutch data protection authority can roughly be divided in 4 different categories: supervisory activities, giving advise on draft legislation, raising awareness and international tasks.
The Dutch DPA supervises the legislation applicable in the Netherlands with regard to the use of personal data. The most important law is the Dutch Data Protection Act, but the Dutch DPA also supervises for example the Acts governing data processing by police and justice as well as parts of the Telecoms Act.
The supervisory activities mainly consist of investigating, ex officio, violations of the law, with the focus on violations that are serious, structural and impact a large amount of people. Where necessary, the Dutch DPA can use its sanctioning powers, including imposing a conditional fine, to enforce the law. The Dutch DPA can also decide to examine sector-wide codes of conduct that are submitted to it and provide its views in the form of a formal opinion.
In addition to investigations, the Dutch DPA advises the government, and sometimes the parliament, on draft legislation related to the processing of personal data. Following the Data Protection Act, the government is obliged to submit both primary and secondary legislation related to data processing to the DPA for advice.
As regards awareness-raising, next to publishing the results of the investigations, its views on codes of conduct and its advice on legislation, the Dutch DPA also issues guidelines, on its own initiative, explaining legal norms. Via its websites, the Dutch DPA provides more information to both data subjects and controllers on how data can and cannot be processed. Specifically for data subjects, self-empowerment tools – including standard letters to exercise their rights – are made available. Furthermore, they can contact the Dutch DPA daily via a telephone hotline.
Last but not least, the Dutch DPA participates in several International and European fora, including the Article 29 Working Party of which I am the Chair, the European and the International Conference of data protection and privacy commissioners, of whose Executive Committee I am also the Chair.
What powers does your office have? in your opinion are these sufficient? Which powers have been most useful? If there is a lack, what do you feel is needed?
The Dutch DPA has a broad range investigative powers, including the power to order the controller to hand over all relevant information and entering the premises of the controller unannounced. All organisations subjected to the supervision of the Dutch DPA are obligated to cooperate.
The Dutch DPA also has a considerable range of sanctioning powers, it can for example order the suspension or termination of certain processing operations and can also impose a conditional fine. Currently a bill is before Parliament to provide the Dutch DPA with fining powers as well.
Especially when the bill providing the Dutch DPA with fining powers will be passed, I feel the powers are sufficient, giving us all the necessary enforcement tools to ensure compliance with the law.
How is your office funded?
The Dutch DPA is funded through the government who, together with the parliament, each year determines the budget for the next year. The budget is drafted on the basis of a proposal from the Dutch DPA.
What is the organizational structure of your office and the responsibilities of the key executives?
The Dutch DPA consists of a college of commissioners and the supporting Secretariat, itself consisting of 6 departments and headed by the Director. The Dutch DPA has 2 supervision departments, one for the private and one for the public sector, a legal department, a communications department, an international department and a department providing the operational support.
If India creates a framework of co-regulation, how would you suggest the overseeing body be structured?
Considering the many differences between India and the Netherlands - and Europe - this is a very hard question to answer. But whatever construction is chosen in India, it is of utmost importance to guarantee the independence of the supervisory authorit(y)(ies), who shall be provided with sufficient and scalable powers to be able to sanction violations.
What legal challenges has your office faced?
The biggest legal challenge we face at the moment is the new European legal framework currently being discussed. It is as yet uncertain whether and when this will enter into force, but it is clear that it will bring new challenges for our office.
What are the main differences between your offices?
Generally, I think that the differences between my office and the UK and Canadian offices mostly stem from our different legal and cultural backgrounds, especially the difference between the common law and codified law systems.
In addition, the norms and powers differ per supervisory authority. The Dutch DPA for example can enter a building without prior notice, while the ICO, if I understand correctly, can only enter with the consent of the supervised organisation.
I however prefer to look at the similarities and possibilities to overcome our differences, because I think that we all feel that providing a high level of data protection and ensuring user control are all of our main priorities.
Naturally, I am very curious to hear from Chrisopher and Chantal as well.
What are the most recent privacy developments for each of your respective offices?
The technological developments of the past decades and the increasing use of smartphones and tablets, have also made privacy developments necessary and have obliged us, as data protection authorities, to consider the rules and norms in this new environment.
What would you broadly recommend for a privacy legislation for India?
In my view the privacy legislation in India should in any case contain the basic principles of the protection of personal data, applicable to both the public and the private sector. Naturally with some exceptions for law enforcement purposes.
Furthermore, the Indian law should protect the imported data of citizens from other parts of the world as well, including the EU.
And as mentioned in my answer to question 5, it is of utmost importance that the Indian legislation guarantees the establishment of (a) completely independent supervisory authorit(y)(ies), provided with sufficient sanctioning powers, to supervise compliance with the legislation also of the government, including police and justice.
What India can Learn from the Snowden Revelations
The title of the article was changed in the version published by Yahoo on October 23, 2013.
Since the ‘Snowden revelations’, which uncovered the United States government’s massive global surveillance through the PRISM program, there have been reactions aplenty to their impact.
The Snowden revelations highlighted the issue of human rights in the context of the existing cross-border and jurisdictional nightmare: the data of foreign citizens surveilled and harvested by agencies such as the National Security Agency through programs such as PRISM are not subject to protection found in the laws of the country. Thus, the US government has the right to access and use the data, but has no responsibility in terms of how the data will be used or respecting the rights of the people from whom the data was harvested.
The Snowden revelations demonstrated that the biggest global surveillance efforts are now being conducted by democratically elected governments – institutions of the people, by the people, for the people – that are increasingly becoming suspicious of all people.
Adding irony to this worrying trend, Snowden sought asylum from many of the most repressive regimes: this dynamic speaks to the state of society today. The Snowden revelations also demonstrate how government surveillance is shifting from targeted surveillance, warranted for a specific reason and towards a specified individual, to blanket surveillance where security agencies monitor and filter massive amounts of information.
This is happening with few checks and balances for cross-border and domestic surveillance in place, and even fewer forms of redress for the individual. This is true for many governments, including India.
India’s reaction
After the first news of the Snowden revelations, the Indian Supreme Court agreed to hear a Public Interest Litigation requesting that foreign companies that shared the information with US security agencies be held accountable for the disclosure. In response to the PIL, the Supreme Court stated it did not have jurisdiction over the US government.
The response of the Supreme Court of India demonstrates the potency of jurisdiction in today’s global information economy in the context of governmental surveillance. Despite being upset at the actions of America’s National Security Agency (NSA), there is little direct legal action that any government or individual can take against the US government or companies incorporated there.
In the PIL, the demand that companies be held responsible is interesting and representative of a global debate, as it implies that in the context of governmental surveillance, companies have a responsibility to actively evaluate and reject or accept governmental surveillance requests. Although I do not disagree with this as a principle, in reality, this evaluation is a difficult step for companies to take.
For example, in India, under Section 69 of the Information Technology Act, 2000, service providers are penalized with up to seven years in prison for non-compliance with a governmental request for surveillance. The incentives for companies to actually reject governmental requests are minimal, but one factor that could possibly push companies to become more pronounced in their resistance to installing backdoors for the government and complying with governmental surveillance requests is market pressure from consumers.
To a certain extent, this has already started to happen. Companies such as Facebook, Yahoo and Google have created ‘transparency reports’ that provide – at different granularities – information about governmental requests and the company’s compliance or rejection of the same.
In India, P. Rajeev, Member of Parliament from Kerala, has started a petition asking that the companies disclose information on Indian data given to US security agencies. Although transparency by complying companies does not translate directly into regulation of surveillance, it allows the customer to make informed choices and decide whether a company’s level of compliance with governmental requests will impact his/her use of that service.
The PIL also called for the establishment of Indian servers to protect the privacy of Indian data. This solution has been voiced by many, including government officials. Though the creation of domestic servers would ensure that the US government does not have direct and unfettered access to Indian data, as it would require that foreign governments access Indian information through a formal Mutual Legal Assistance Treaty process, it does not necessarily enhance the privacy of Indian data.
As a note, India has MLAT treaties with 34 countries. If domestic servers were established, the information would be subject to Indian laws and regulations.
Snooping
The Snowden Revelations are not the first instance to spark a discussion on domestic servers by the Government of India.
For example, in the back-and-forth between the Indian government and the Canadian company RIM, now BlackBerry, the company eventually set up servers in Mumbai and provided a lawful interception solution that satisfied the Indian government. The Indian government made similar demands from Skype and Google. In these instances, the domestic servers were meant to facilitate greater surveillance by Indian law enforcement agencies.
Currently in India there are a number of ways in which the government can legally track data online and offline. For example, the interception of telephonic communications is regulated by the Indian Telegraph Act, 1885, and relies on an order from the Secretary to the Ministry of Home Affairs. Interception, decryption, and monitoring of digital communications are governed by Section 69 of the Information Technology Act, 2000 and again rely on the order of the executive.
The collection and monitoring of traffic data is governed by Section 69B of the Information Technology Act and relies on the order of the Secretary to the government of India in the Department of Information Technology. Access to stored data, on the other hand, is regulated by Section 91 of the Code of Criminal Procedure and permits access on the authorization of an officer in charge of a police station.
The gaps in the Indian surveillance regime are many and begin with a lack of enforcement and harmonization of existing safeguards and protocols. Presently, India is in the process of realizing a privacy legislation.
In 2012, a committee chaired by Justice AP Shah (of which the Center for Internet and Society was a member) wrote The Report of the Group of Experts on Privacy, which laid out nine national privacy principles meant to be applied to different legislation and sectors – including Indian provisions on surveillance.
The creation of domestic servers is just one example of how the Indian government has been seeking greater access to information flowing within its borders. New requirements for Indian service providers and the creation of projects that go beyond the legal limits of governmental surveillance in India enable greater access to details about an individual on a real-time and blanket basis.
For example, telecoms in India are now required to include user location data as part of the ‘call detail record’ and be able to provide the same to law enforcement agencies on request under provisions in the Unified Access Service and Internet Service Provider Licenses.
At the same time, the Government of India is in the process of putting in place a Central Monitoring System that would provide Indian security agencies the ability to directly intercept communications, bypassing the service provider.
Even if the Central Monitoring System were to adhere to the legal safeguards and procedures defined under the Indian Telegraph Act and Information Technology Act, the system can only do so partially, as both provisions create a clear chain of custody that the government and service providers must follow – that is, the service provider was included as an integral component of the interception process.
If the Indian government implements the Central Monitoring System, it could remove governmental surveillance completely from the public eye. Bypassing the service provider allows the government to fully determine how much the public knows about surveillance. It also removes the market and any pressure that consumers could exert from insight provided by companies on the surveillance requests that they are facing.
Though the Indian government could (and should) be transparent about the amount and type of surveillance it is undertaking, currently there is no legal requirement for the government of India to disclose this information, and security agencies are exempt from the Right to Information Act. Thus, unless India has a Snowden somewhere in the apparatus, the Indian public cannot hope to get an idea of how prevalent or extensive Indian surveillance really is.
Policy vacuum
For any government, the surveillance of its citizens, to some degree, might be necessary. But the Snowden revelations demonstrate that there is a vacuum when it comes to surveillance policy and practices. This vacuum has permitted draconian measures of surveillance to take place and created an environment of mistrust between citizens and governments across the globe.
When governments undertake surveillance, it is critical that the purpose, necessity and legality of monitoring, and the use of the material collected are built into the regime to ensure it does not violate the human rights of the people surveilled, foreign or domestic.
In 2013, the International Principles on the Application of Human Rights to Communications Surveillance were drafted, in part, to address this vacuum. The principles seek to explain how international human rights law applies to surveillance of communications in the current digital and technological environment. They define safeguards to ensure that human rights are protected and upheld when governments undertake surveillance of communications.
When the Indian surveillance regime is measured against these principles, it appears to miss a number of them, and does not fully meet several others. In the context of surveillance projects like the Central Monitoring System, and in order to avoid an Indian version of the PRISM program, India should take into consideration the safeguards defined in the principles and strengthen its surveillance regime to ensure not only the protection of human rights in the context of surveillance, but to also establish trust in its surveillance regime and practices with other countries.
Elonnai Hickok is the Program Manager for Internet Governance at the Centre for Internet and Society, and leads its research on privacy.
(IMDEC) 2013
 Proposed-Program-IMDEC.pdf
—
PDF document,
120 kB (122998 bytes)
Proposed-Program-IMDEC.pdf
—
PDF document,
120 kB (122998 bytes)
Mapping Digital Media Background Note
 Background note_MDM.pdf
—
PDF document,
447 kB (458684 bytes)
Background note_MDM.pdf
—
PDF document,
447 kB (458684 bytes)
MDM Invite Poster
 MDM Invite_Poster.pdf
—
PDF document,
1104 kB (1130749 bytes)
MDM Invite_Poster.pdf
—
PDF document,
1104 kB (1130749 bytes)
MDM Press Invite
 MDM_Press Invite.pdf
—
PDF document,
775 kB (794198 bytes)
MDM_Press Invite.pdf
—
PDF document,
775 kB (794198 bytes)
MDM Digital Media Press Release
 Press release_MDM Public Consultation (1).pdf
—
PDF document,
216 kB (221365 bytes)
Press release_MDM Public Consultation (1).pdf
—
PDF document,
216 kB (221365 bytes)
Spy Files 3: WikiLeaks Sheds More Light On The Global Surveillance Industry
Last month, WikiLeaks released “Spy Files 3”, a mass exposure of the global surveillance trade and industry. WikiLeaks first released the Spy Files in December 2011, which entail brochures, presentations, marketing videos and technical specifications on the global trade of surveillance technologies. Spy Files 3 supplements this with 294 additional documents from 92 global intelligence contractors.
So what do the latest Spy Files reveal about India?
When we think about India, the first issues that probably come to mind are poverty and corruption, while surveillance appears to be a more “Western” and elitist issue. However, while many other developing countries are excluded from WikiLeaks’ list of surveillance technology companies, India is once again on the list with some of the most controversial spyware.
ISS World Surveillance Trade Shows
The latest Spy Files include a brochure of the ISS World 2013 -the so-called “wiretapper’s ball”- which is the world’s largest surveillance trade show. This years’ ISS World Asia will take place in Malaysia during the first week of December and law enforcement agencies from around the world will have another opportunity to view and purchase the latest surveillance tech. The leaked ISS World 2013 brochure entails a list of last years’ global attendees. According to the brochure, 53% of the attendees included law enforcement agencies and individuals from the defense, public safety and interior security sectors, 41% of the attendees were ISS vendors and technology integrators, while only 6% of the attendees were telecom operators and from the private enterprise. The brochure boasts that 4,635 individuals from 110 countries attended the ISS World trade shows last year and that the percentage of attendance is increasing.
The following table lists the Indian attendees at last years’ ISS World:
|
Law Enforcement, Defense and Interior Security Attendees |
Telecom Operators and Private Enterprises Attendees |
ISS Vendors and Technology Integrators Attendees |
|---|---|---|
|
Andhra Pradesh India Police |
BT |
AGC Networks |
|
CBI Academy |
Cogence Investment Bank |
Aqsacom India |
|
Government of India, Telecom Department |
India Reliance Communications |
ClearTrail Technologies |
|
India Cabinet Secretariat |
Span Telecom Pvt. Ldt. |
Foundation Technologies |
|
India Centre for Development of Telematics (C-DOT) |
Kommlabs |
|
|
India Chandigarh Police |
Paladion Networks |
|
|
India Defence Agency |
Polaris Wireless |
|
|
India General Police |
Polixel Security Systems |
|
|
India Intelligence Department |
Pyramid Cyber Security |
|
|
India National Institute of Criminology |
Schleicher Group |
|
|
India office LOKAYUKTA NCT DELHI |
Span Technologies |
|
|
India Police Department, A.P. |
TATA India |
|
|
India Tamil Nadu Police Department |
Tata Consultancy Services |
|
|
Indian Police Service, Vigilance |
Telecommunications India |
|
|
Indian Telecommunications Authority |
Vehere Interactive |
|
|
NTRO India |
||
|
SAIC Indian Tamil Nadu Police |
| 17 4 15 |
|---|
According to the above table - which is based on data from the WikiLeaks’ ISS World 2013 brochure- the majority of Indian attendees at last years’ ISS World were from the law enforcement, defense and interior security sectors. 15 Indian companies exhibited and sold their surveillance technologies to law enforcement agencies from around the world and it is notable that India’s popular ISP provider, Reliance Communications, attended the trade show too.
In addition to the ISS World 2013 brochure, the Spy Files 3 entail a detailed brochure of a major Indian surveillance technology company: ClearTrail Technologies.
ClearTrail Technologies
ClearTrail Technologies is an Indian company based in Indore. The document titled “Internet Monitoring Suite” from ClearTrail Technologies boasts about the company’s mass monitoring, deep packet inspection, COMINT, SIGINT, tactical Internet monitoring, network recording and lawful interception technologies. ClearTrail’s Internet Monitoring Suite includes the following products:
1. ComTrail: Mass Monitoring of IP and Voice Networks
ComTrail is an integrated product suite for centralized interception and monitoring of voice and data networks. It is equipped with an advanced analysis engine for pro-active analysis of thousands of connections and is integrated with various tools, such as Link Analysis, Voice Recognition and Target Location.
ComTrail is deployed within a service provider network and its monitoring function correlates voice and data intercepts across diverse networks to provide a comprehensive intelligence picture. ComTrail supports the capture, record and replay of a variety of Voice and IP communications in pretty much any type of communication, including - but not limited to- Gmail, Yahoo, Hotmail, BlackBerry, ICQ and GSM voice calls.
Additionally, ComTrail intercepts data from any type of network -whether Wireless, packet data, Wire line or VoIP networks- and can decode hundreds of protocols and P2P applications, including HTTP, Instant Messengers, Web-mails, VoIP Calls and MMS.
In short, ComTrail’s key features include the following:
- Equipped to handle millions of communications per day intercepted over high speed STM & Ethernet Links
- Doubles up as Targeted Monitoring System
- On demand data retention, capacity exceeding several years
- Instant Analysis across thousands of Terabytes
- Correlates Identities across multiple networks
- Speaker Recognition and Target Location
2. xTrail: Targeted IP Monitoring
xTrail is a solution for interception, decoding and analysis of high speed data traffic over IP networks and independently monitors ISPs/GPRS and 3G networks. xTrail has been designed in such a way that it can be deployed within minutes and enables law enforcement agencies to intercept and monitor targeted communications without degrading the service quality of the IP network. This product is capable of intercepting all types of networks -including wireline, wireless, cable, VoIP and VSAT networks- and acts as a black box for “record and replay” targeted Internet communications.
Interestingly enough, xTrail can filter based on a “pure keyword”, a URL/Domain with a keyword, an IP address, a mobile number or even with just a user identity, such as an email ID, chat ID or VoIP ID. Furthermore, xTrail can be integrated with link analysis tools and can export data in a digital format which can allegedly be presented in court as evidence.
In short, xTrail’s key features include the following:
- Pure passive probe
- Designed for rapid field operations at ISP/GPRS/Wi-Max/VSAT Network Gateways
- Stand-alone solution for interception, decoding and analysis of multi Gigabit IP traffic
- Portable trolley based for simplified logistics, can easily be deployed and removed from any network location
- Huge data retention, rich analysis interface and tamper proof court evidence
- Easily integrates with any existing centralized monitoring system for extended coverage
3. QuickTrail: Tactical Wi-Fi Monitoring
Some of the biggest IP monitoring challenges that law enforcement agencies face include cases when targets operate from public Internet networks and/or use encryption.
QuickTrail is a device which is designed to gather intelligence from public Internet networks, when a target is operating from a cyber cafe, a hotel, a university campus or a free Wi-Fi zone. In particular, QuickTrail is equipped with multiple monitoring tools and techniques that can help intercept almost any wired, Wi-Fi or hybrid Internet network so that a target communication can be monitored. QuickTrail can be deployed within fractions of seconds to intercept, reconstruct, replay and analyze email, chat, VoIP and other Internet activities of a target. This device supports real time monitoring and wiretapping of Ethernet LANs.
According to ClearTrail’s brochure, QuickTrail is a “all-in-one” device which can intercept secured communications, know passwords with c-Jack attack, alert on activities of a target, support active and passive interception of Wi-Fi and wired LAN and capture, reconstruct and replay. It is noteworthy that QuickTrail can identify a target machine on the basis of an IP address, MAC ID, machine name, activity status and several other parameters. In addition, QuickTrail supports protocol decoding, including HTTP, SMTP, POP3 and HTTPS. This device also enables the remote and central management of field operations at geographically different locations.
In short, QuickTrail’s key features include the following:
- Conveniently housed in a laptop computer
- Intercepts Wi-Fi and wired LANs in five different ways
- Breaks WEP, WPA/WPA2 to rip-off secured Wi-Fi networks
- Deploys spyware into a target’s machine
- Monitor’s Gmail, Yahoo and all other HTTPS-based communications
- Reconstructs webmails, chats, VoIP calls, news groups and social networks
4. mTrail: Off-The-Air Interception
mTrail offers active and passive ‘off-the-air’ interception of GSM 900/1800/1900 Mhz phone calls and data to meet law enforcement surveillance and investigation requirements. The mTrail passive interception system works in the stealth mode so that there is no dependence on the network operator and so that the target is unaware of the interception of its communications.
The mTrail system has the capability to scale from interception of 2 channels (carrier frequencies) to 32 channels. mTrail can be deployed either in a mobile or fixed mode: in the mobile mode the system is able to fit into a briefcase, while in the fixed mode the system fits in a rack-mount industrial grade chassis.
Target location identification is supported by using signal strength, target numbers, such as IMSI, TIMSI, IMEI or MSI SDN, which makes it possible to listen to the conversation on so-called “lawfully intercepted” calls in near real-time, as well as to store all calls. Additionally, mTrail supports the interception of targeted calls from pre-defined suspect lists and the monitoring of SMS and protocol information.
In short, mTrail’s key features include the following:
- Designed for passive interception of GSM communications
- Intercepts Voice and SMS “off-the-air”
- Detects the location of the target
- Can be deployed as a fixed unit or mounted in a surveillance van
- No support required from GSM operator
5. Astra: Remote Monitoring and Infection framework
“Astra” is a remote monitoring and infection framework which incorporates both conventional and proprietary infection methods to ensure bot delivery to the targeted devices. It also offers a varied choice in handling the behavior of bots and ensuring non-traceable payload delivery to the controller.
The conventional methods of infection include physical access to a targeted device by using exposed interfaces, such as a CD-ROM, DVD and USB ports, as well as the use of social media engineering techniques. However, Astra also supports bot deployment without requiring any physical access to the target device.
In particular, Astra can push bot to any targeted machine sharing the same LAN (wired, wi-fi or hybrid). The SEED is a generic bot which can identify a target’s location, log keystrokes, capture screen-shots, capture Mic, listen to Skype calls, capture webcams and search the target’s browsing history. Additionally, the SEED bot can also be remotely activated, deactivated or terminated, as and when required. Astra allegedly provides an un-traceable reporting mechanism that operates without using any proxies, which overrules the possibility of getting traced by the target.
Astra’s key features include the following:
- Proactive intelligence gathering
- End-to-end remote infection and monitoring framework
- Follow the target, beat encryption, listen to in-room conversations, capture keystrokes and screen shots
- Designed for centralized management of thousands of targets
- A wide range of deployment mechanisms to optimize success ration
- Non-traceable, non-detectable delivery mechanism
- Intrusive yet stealthy
- Easy interface for handling most complex tasks
- Successfully tested over the current top 10 anti-virus available in the market
- No third party dependencies
- Free from any back-door intervention
ClearTrail Technologies argue that they meet lawful interception regulatory requirements across the globe. In particular, they claim that their products are compliant with ETSI and CALEA regulations and that they are efficient to cater to region specific requirements as well.
The latest Spy Files also include data on foreign surveillance technology companies operating in India, such as Telesoft Technologies, AGT International and Verint Systems. In particular, Verint Systems has its headquarters in New York and offices all around the world, including Bangalore in India. Founded in 1994 and run by Dan Bodner, Verint Systems produces a wide range of surveillance technologies, including the following:
- Impact 360 Speech Analytics
- Impact 360 Text Analytics
- Nextiva Video Management Software (VMS)
- Nextiva Physical Security Information Management (PSIM)
- Nextiva Network Video Recorders (NVRs)
- Nextiva Video Business Intelligence (VBI)
- Nextiva Surveillance Analytics
- Nextiva IP cameras
- CYBERVISION Network Security
- ENGAGE suite
- FOCAL-INFO (FOCAL-COLLECT & FOCAL-ANALYTICS)
- RELIANT
- STAR-GATE
- VANTAGE
While Verint Systems claims to be in compliance with ETSI, CALEA and other worldwide lawful interception and standards and regulations, it remains unclear whether such products successfully help law enforcement agencies in tackling crime and terrorism, without violating individuals’ right to privacy and other human rights. After all, Verint Systems has participated in ISS World Trade shows which exhibit some of the most controversial spyware in the world, used to target individuals and for mass surveillance.
And what do the latest Spy Files mean for India?
Why is it even important to look at the latest Spy Files? Well, for starters, they reveal data about which Indian law enforcement agencies are interested in surveillance and which companies are interested in selling and/or buying the latest spy gear. And why is any of this important? I can think of three main reasons:
1. The Central Monitoring System (CMS)
2. Is any of this surveillance even legal in India?
3. Can such surveillance result in the violation of human rights?
Spy Files 3...and the Central Monitoring System (CMS)
Following the Mumbai 2008 terrorist attacks, the Telecom Enforcement, Resource and Monitoring (TREM) cells and the Centre for Development of Telematics (C-DOT) started preparing the Central Monitoring System (CMS). As of April 2013, this project is being manned by the Intelligence Bureau, while agencies which are planned to have access to it include the Research & Analysis Wing (RAW) and the Central Bureau of Investigation (CBI). ISP and Telecom operators are required to install the gear which enables law enforcement agencies to carry out the Central Monitoring System under the Unified Access Services (UAS) License Agreement.
The Central Monitoring System aims at centrally monitoring all telecommunications and Internet communications in India and its estimated cost is Rs. 4 billion. In addition to equipping government agencies with Direct Electronic Provisioning, filters and alerts on the target numbers, the CMS will also enable Call Data Records (CDR) analysis and data mining to identify personal information of the target numbers. The CMS supplements regional Internet Monitoring Systems, such as that of Assam, by providing a nationwide monitoring of telecommunications and Internet communications, supposedly to assist law enforcement agencies in tackling crime and terrorism.
However, data monitored and collected through the CMS will be stored in a centralised database, which could potentially increase the probability of centralized cyber attacks and thus increase, rather than reduce, threats to national security. Furthermore, some basic rules of statistics indicate that the bigger the amount of data, the bigger the probability of an error in matching profiles, which could potentially result in innocent people being charged with crimes they did not commit. And most importantly: the CMS currently lacks adequate legal oversight, which means that it remains unclear how monitored data will be used. The UAS License Agreement regarding the CMS mandates mass surveillance by requiring ISPs and Telecom operators to enable the monitoring and interception of communications. However, targeted and mass surveillance through the CMS not only raises serious questions around its legality, but also creates the potential for abuse of the right to privacy and other human rights.
Interestingly enough, Indian law enforcement agencies which attended last years’ ISS World trade shows are linked to the Central Monitoring System. In particular, last years’ law enforcement, defense and interior security attendees include the Centre for Development of Telematics (C-DOT) and the Department of Telecommunications, both of which prepared the Central Monitoring System. The list of attendees also includes India’s Intelligence Bureau, which is manning the CMS, as well as the agencies which will have access to the CMS: the Central Bureau of Investigation (CBI), the Research and Analysis Wing (RAW), the National Technical Research Organization (NTRO) and various other state police departments and intelligence agencies.
Furthermore, Spy Files 3 entail a list of last years’ ISS World security company attendees, which includes several Indian companies. Again, interestingly enough, many of these companies may potentially be aiding law enforcement with the technology to carry out the Central Monitoring System. ClearTrail Technologies, in particular, provides solutions for targeted and mass monitoring of IP and voice networks, as well as remote monitoring and infection frameworks - all of which would potentially be perfect to aid the Central Monitoring System.
In fact, ClearTrail states in its brochure that its ComTrail product is equipped to handle millions of communications per day, while its xTrail product can easily be integrated with any existing centralised monitoring system for extended coverage. And if that’s not enough, ClearTrail’s “Astra” is designed for the centralized management of thousands of targets. While there may not be any concrete proof that ClearTrail is indeed aiding the Centralized Monitoring System, the facts speak for themselves: ClearTrail is an Indian company which sells target and mass monitoring products to law enforcement agencies. The Centralized Monitoring System is currently being implemented. What are the odds that ClearTrail is not equipping the CMS? And what are the odds that such technology is not being used for other mass electronic surveillance programmes, such as the Lawful Intercept and Monitoring (LIM)?
Spy Files 3...and the legality of India’s surveillance technologies
ClearTrail Technologies’ brochure -the only leaked document on Indian surveillance technology by the latest Spy Files- states that the company complies with ETSI and CALEA regulations. While it’s clear that the company complies with U.S. and European regulations on the interception of communications to attract more customers in the international market, such regulations don’t really apply within India, which is part of ClearTrail’s market. Notably enough, ClearTrail does not mention any compliance with Indian regulations in its brochure. So let’s have a look at them.
India has five laws which regulate surveillance:
1. The Indian Telegraph Act, 1885
2. The Indian Post Office Act, 1898
3. The Indian Wireless Telegraphy Act, 1933
4. The Code of Criminal Procedure (CrPc), 1973: Section 91
5. The Information Technology (Amendment) Act, 2008
The Indian Post Offices Act does not cover electronic communications and the Indian Wireless Telegraphy Act lacks procedures which would determine if surveillance should be targeted or not. Neither the Indian Telegraph Act nor the Information Technology (Amendment) Act cover mass surveillance, but are both limited to targeted surveillance. Moreover, targeted interception in India according to these laws requires case-by-case authorization by either the home secretary or the secretary department of information technology. In other words, unauthorized, limitless, mass surveillance is not technically permitted by law in India.
The Indian Telegraph Act mandates that the interception of communications can only be carried out on account of a public emergency or for public safety. However, in 2008, the Information Technology Act copied most of the interception provisions of the Indian Telegraph Act, but removed the preconditions of public emergency or public safety, and instead expanded the power of the government to order interception for the “investigation of any offense”.
The interception of Internet communications is mainly covered by the 2009 Rules under the Information Technology Act 2008 and Sections 69 and 69B are particularly noteworthy. According to these Sections, an Intelligence Bureau officer who leaked national secrets may be imprisoned for up to three years, while Section 69 not only allows for the interception of any information transmitted through a computer resource, but also requires that users disclose their encryption keys upon request or face a jail sentence of up to seven years.
While these laws allow for the interception of communications and can be viewed as widely controversial, they do not technically permit the mass surveillance of communications. In other words, ClearTrail’s products, such as ComTrail, which enable the mass interception of IP networks, lack legal backing. However, the Unified Access Services (UAS) License Agreement regarding the Central Monitoring System mandates mass surveillance and requires ISP and Telecom operators to comply.
Through the licenses of the Department of Telecommunications, Internet service providers, cellular providers and telecoms are required to provide the Government of India direct access to all communications data and content even without a warrant, which is not permitted under the laws on interception. These licenses also require cellular providers to have ‘bulk encryption’ of less than 40 bits, which means that potentially any person can use off-the-air interception to monitor phone calls. However, such licenses do not regulate the capture of signal strength, target numbers like IMSI, TIMSI, IMEI or MSI SDN, which can be captured through ClearTrail’s mTrail product.
More importantly, following allegations that the National Technical Research Organization (NTRO) had been using off-the-air interception equipment to snoop on politicians in 2011, the Home Ministry issued a directive to ban the possession or use of all off-the-air phone interception gear. As a result, the Indian Government asked the Customs Department to provide an inventory of all all such equipment imported over a ten year period, and it was uncovered that as many as 73,000 pieces of equipment had been imported. Since, the Home Ministry has informed the heads of law enforcement agencies that there has been a compete ban on use of such equipment and that all those who possess such equipment and fail to inform the Government will face prosecution and imprisonment. In short, ClearTrail's product, mTrail, which undertakes off-the-air phone monitoring is illegal and Indian law enforcement agencies are prohibited from using it.
ClearTrail’s “Astra” product is capable of remote infection and monitoring, which can push bot to any targeted machine sharing the same LAN. While India’s ISP and telecommunications licenses generally provide some regulations, they appear to be inadequate in regulating specific surveillance technologies which have the capability to target machines and remotely monitor them. Such licenses mandate mass surveillance, but legally, wireless communications are completely unregulated, which raises the question of whether the interception of public Internet networks is allowed. In other words, it is not clear if ClearTrail’s QuickTrail is technically legal or not. The UAS License agreement mandates mass surveillance, and while the law does not prohibit it, it does not mandate mass surveillance either. This remains a grey area.
The issue of data retention arises from ClearTrail’s leaked brochure. In particular, ClearTrail states in its brochure that ComTrail - which undertakes mass monitoring of IP and Voice networks - retains data upon request, with a capacity that exceeds several years. xTrail - for targeted IP monitoring - has the ability to retain huge volumes of data which can potentially be used as proof in court. However, India currently lacks privacy legislation which would regulate data retention, which means that data collected by ClearTrail could potentially be stored indefinitely.
Section 7 of the Information Technology (Amendment) Act, 2008, deals with the retention of electronic records. However, this section does not state a particular data retention period, nor who will have authorized access to data during its retention, who can authorize such access, whether retained data can be shared with third parties and, if so, under what conditions. Section 7 of the Information Technology (Amendment) Act, 2008, appears to be incredibly vague and to fail to regulate data retention adequately.
Data retention requirements for service providers are included in the ISP and UASL licenses and, while they clarify the type of data they retain, they do not specify adequate conditions for data retention. Due to the lack of data protection legislation in India, it remains unclear how long data collected by companies, such as ClearTrail, would be stored for, as well as who would have authorized access to such data during its retention period, whether such data would be shared with third parties and disclosed and if so, under what conditions.
India currently lacks specific regulations for the use of various types of technologies, which makes it unclear whether ClearTrail’s spy products are technically legal or not. It is clear that ClearTrail’s mass interception products, such as ComTrail, are not legalized - since Indian laws allow for targeted interception- but they are mandated through the UAS License agreement regarding the Central Monitoring System.
In short, the legality of ClearTrail’s surveillance technologies remains ambiguous. While India’s ISP and telecom licenses and the UAS License Agreement mandate mass surveillance, the laws - particularly the 2009 Information Technology Rules- mandate targeted surveillance and remain silent on the issue of mass surveillance. Technically, this does not constitute mass surveillance legal or illegal, but rather a grey area. Furthermore, while India’s Telegraph Act, Information Technology Act and 2009 Rules allow for the interception, monitoring and decryption of communications and surveillance in general, they do not explicitly regulate the various types of surveillance technologies, but rather attempt to “legalize” them through the blanket term of surveillance.
One thing is clear: India’s license agreements ensure that all ISPs and telecom operators are a part of the surveillance regime. The lack of regulations for India’s surveillance technologies appear to create a grey zone for the expansion of mass surveillance in the country. According to Saikat Datta, an investigative journalist, a senior privacy telecom official stated:
“Do you really think a private telecom company can stand up to the government or any intelligence agency and cite law if they want to tap someone’s phone?”
Spy Files 3...and human rights in India
The facts speak for themselves. The latest Spy Files confirm that the same agencies involved in the development of the Central Monitoring System (CMS) are also interested in the latest surveillance technology sold in the global market. Spy Files 3 also provide data on one of India’s largest surveillance technology companies, ClearTrail, which sells a wide range of surveillance technologies to law enforcement agencies around the world. And Spy Files 3 show us exactly what these technologies can do.
In particular, ClearTrail’s ComTrail provides mass monitoring of IP and voice networks, which means that law enforcement agencies using it are capable of intercepting millions of communications every day through Gmail, Yahoo, Hotmail and others, of correlating our identities across networks and of targeting our location. xTrail enables law enforcement agencies to monitor us based on our “harmless” metadata, such as our IP address, our mobile number and our email ID. Think our data is secure when using the Internet through a cyber cafe? Well QuickTrail proves us wrong, as it’s able to assist law enforcement agencies in monitoring and intercepting our communications even when we are using public Internet networks.
And indeed, carrying a mobile phone is like carrying a GPS device, especially since mTrail provides law enforcement with off-the-air interception of mobile communications. Not only can mTrail target our location, listen to our calls and store our data, but it can also undertake passive off-the-air interception and monitor our voice, SMS and protocol information. Interestingly enough, mTrail also intercepts targeted calls from a predefined suspect list. The questions though which arise are: who is a suspect? How do we even know if we are suspects? In the age of the War on Terror, potentially anyone could be a suspect and thus potentially anyone’s mobile communications could be intercepted. After all, mass surveillance dictates that we are all suspicious until proven innocent.
And if anyone can potentially be a suspect, then potentially anyone can be remotely infected and monitored by Astra. Having physical access to a targeted device is a conventional surveillance mean of the past. Today, Astra can remotely push bot to our laptops and listen to our Skype calls, capture our Webcams, search our browsing history, identify our location and much more. And why is any of this concerning? Because contrary to mainstream belief, we should all have something to hide!
Privacy protects us from abuse from those in power and safeguards our individuality and autonomy as human beings. If we are opposed to the idea of the police searching our home without a search warrant, we should be opposed to the idea of our indiscriminate mass surveillance. After all, mass surveillance - especially the type undertaken by ClearTrail’s products - can potentially result in the access, sharing, disclosure and retention of data much more valuable than that acquired by the police searching our home. Our credit card details, our photos, our acquaintances, our personal thoughts and opinions, and other sensitive personal information can usually be found in our laptops, which potentially can constitute much more incriminating information than that found in our homes.
And most importantly: even if we think that we have nothing to hide, it’s really not up to us to decide: it’s up to data analysts. While we may think that our data is “harmless”, a data analyst linking our data to various other people and search activities we have undertaken might indicate otherwise. Five years ago, a UK student studying Islamic terrorism for his Masters dissertation was detained for six days. The student may not have been a terrorist, but his data said this: “Young, male, Muslim... who is downloading Al-Qaeda’s training material” - and that was enough for him to get detained. Clearly, the data analysts mining his online activity did not care about the fact that the only reason why he was downloading Al-Qaeda material was for his Masters dissertation. The fact that he was a male Muslim downloading terrorist material was incriminating enough.
This incident reveals several concerning points: The first is that he was clearly already under surveillance, prior to downloading Al-Qaeda’s material. However, given that he did not have a criminal record and was “just a Masters student in the UK”, there does not appear to be any probable cause for his surveillance in the first place. Clearly he was on some suspect list on the premise that he is male and Muslim - which is a discriminative approach. The second point is that after this incident, it is likely that some male Muslims may be more cautious about their online activity - with the fear of being on some suspect list and eventually being prosecuted because their data shows that “they’re a terrorist”. Thus, mass surveillance today appears to also have implications on freedom of expression. The third point is that this incident reveals the extent of mass surveillance, since even a document downloaded by a Masters student is being monitored.
This case proves that innocent people can potentially be under surveillance and prosecuted, as a result of mass, indiscriminate surveillance. Anyone can potentially be a suspect today, and maybe for the wrong reasons. It does not matter if we think our data is “harmless”, but what matters is who is looking at our data, when and why. Every bit of data potentially hides several other bits of information which we are not aware of, but which will be revealed within a data analysis. We should always “have something to hide”, as that is the only way to protect us from abuse by those in power.
In the contemporary surveillance state, we are all suspects and mass surveillance technologies, such as the ones sold by ClearTrail, can potentially pose major threats to our right to privacy, freedom of expression and other human rights. And probably the main reason for this is because surveillance technologies in India legally fall in a grey area. Thus, it is recommended that law enforcement agencies in India regulate the various types of surveillance technologies in compliance with the International Principles on Communications Surveillance and Human Rights.
Spy Files 3 show us why our human rights are at peril and why we should fight for our right to be free from suspicion.
This article was cross-posted in Medianama on 6th November 2013.
Re: The Human DNA Profiling Bill, 2012
Note: Clause-by-clause comments on the Working Draft version of April 29, 2012 from the Centre for Internet and Society
- This short note speaks to legal issues arising from the proposed Human DNA Profiling Bill, 2012 ("DBT Bill") that was circulated within the Experts Committee constituted under the aegis of the Department of Biotechnology of the Ministry of Science and Technology, Government of India.
- This note must be read against the relevant provisions of the DBT Bill and, where indicated, together with the proposed Forensic DNA Profiling (Regulation) Bill, 2013 that was drafted by the Centre for Internet & Society, Bangalore ("CIS Bill"). These comments must also be read alongside the two-page submission titled “A Brief Note on the Forensic DNA Profiling (Regulation) Bill, 2013” ("CIS Note"). Whereas the aforesaid CIS Note raised issues that informed the drafting of the CIS Bill, this present note seeks to provide legal comments on the DBT Bill.
Preamble - The DBT Bill, in its current working form, lacks a preamble. No doubt, a preamble will be added later once the text of the DBT Bill is finalised. Instead, the DBT Bill contains an introduction. It must be borne in mind that the purpose of the legislation should be spelt out in the preamble since preambular clauses have interpretative value. [See, A. Thangal Kunju Musaliar AIR 1956 SC 246; Burrakur Coal Co. Ltd. AIR 1961 SC 954; and Arnit Das (2000) 5 SCC 488]. Hence, a preamble that states the intent of Parliament to create permissible conditions for DNA source material collection, profiling, retention and forensic use in criminal trials is necessary.
Objects Clause - An ‘objects clause,’ detailing the intention of the legislature and containing principles to inform the application of a statute, in the main body of the statute is an enforceable mechanism to give directions to a statute and can be a formidable primary aid in statutory interpretation. [See, for example, section 83 of the Patents Act, 1970 that directly informed the Order of the Controller of Patents, Mumbai, in the matter of NATCO Pharma and Bayer Corporation in Compulsory Licence Application No. 1 of 2011.] Therefore, the DBT Bill should incorporate an objects clause that makes clear that (i) the principles of notice, confidentiality, collection limitation, personal autonomy, purpose limitation and data minimisation must be adhered to at all times; (ii) DNA profiles merely estimate the identity of persons, they do not conclusively establish unique identity; (iii) all individuals have a right to privacy that must be continuously weighed against efforts to collect and retain DNA; (iv) centralised databases are inherently dangerous because of the volume of information that is at risk; (v) forensic DNA profiling is intended to have probative value; therefore, if there is any doubt regarding a DNA profile, it should not be received in evidence by a court; (vi) once adduced, the evidence created by a DNA profile is only corroborative and must be treated on par with other biometric evidence such as fingerprint measurements.
Definitions - The definition of “analytical procedure” in clause 2(1)(a) of the DBT Bill is practically redundant and should be removed. It is used only twice – in clauses 24 and 66(2)(p) which give the DNA Profiling Board the power to frame procedural regulations. In the absence of specifying the content of any analytical procedure, the definition serves no purpose.
- The definition of “audit” in clause 2(1)(b) is relevant for measuring the training programmes and laboratory conditions specified in clauses 12(f) and 27. However, the term “audit” is subsequently used in an entirely different manner in Chapter IX which relates to financial information and transparency. This is a conflicting definition. The term “audit” has a well-established use for financial information that does not require a definition. Hence, this definition should be removed.
- The definition of “calibration” in clause 2(1)(d) is redundant and should be removed since the term is not meaningfully used in the DBT Bill.
- The definition of “DNA Data Bank” in clause 2(1)(h) is unnecessary. The DBT Bill seeks to establish a National DNA Data Bank, State DNA Data Banks and Regional DNA Data Banks vide clause 32. These national, state and regional databases must be defined individually with reference to their establishment clauses. Defining a “DNA Data Bank”, exclusive of the national, state and regional databases, creates the assumption that any private individual can start and maintain a database. This is a drafting error.
- The definition of “DNA Data Bank Manager” in clause 2(1)(i) is misleading since, in the text of the DBT Bill, it is only used in relation to the proposed National DNA Data Bank and never in relation to the State and Regional Data Banks. If it is the intention of DBT Bill that only the national database should have a manager, the definition should be renamed to ‘National DNA Data Bank Manager’ and the clause should specifically identify the National DNA Data Bank. This is a drafting error.
- The definition of “DNA laboratory” in clause 2(1)(j) should refer to the specific clauses that empower the Central Government and State Governments to license and recognise DNA laboratories. This is a drafting error.
- The definition of “DNA profile” in clause 2(1)(l) is too vague. Merely the results of an analysis of a DNA sample may not be sufficient to create an actual DNA profile. Further, the results of the analysis may yield DNA information that, because of incompleteness or lack of information, is inconclusive. These incomplete bits of information should not be recognised as DNA profiles. This definition should be amended to clearly specify the contents of a complete and valid DNA profile that contains, at least, numerical representations of 17 or more loci of short tandem repeats that are sufficient to estimate biometric individuality of a person.
- The definition of “forensic material” in clause 2(1)(o) needs to be amended to remove the references to intimate and non-intimate body samples. If the references are retained, then evidence collected from a crime scene, where an intimate or non-intimate collection procedure was obviously not followed, will not fall within the scope of “forensic material”.
- The terms “intimate body sample” and “non-intimate body sample” that are defined in clauses 2(1)(q) and 2(1)(v) respectively are not used anywhere outside the definitions clause except for an inconsequential reference to non-intimate body samples only in the rule-making provision of clause 66(2)(zg). “Intimate body sample” is not used anywhere outside the definitions clause. Both these definitions are redundant and should be removed.
- The terms “intimate forensic procedure” and “non-intimate forensic procedure”, that are defined in clauses 2(1)(r) and 2(1)(w) respectively, are not used anywhere except for an inconsequential reference of non-intimate forensic procedure in the rule-making provision of clause 66(2)(zg). “Intimate forensic procedure” is not used anywhere outside the definitions clause. Both these definitions are redundant and should be removed.
- The term “known samples” that is defined in clause 2(1)(s) is not used anywhere outside the definitions clause and should be removed for redundancy.
- The definition of “offender” in clause 2(1)(y) if vague because it does not specify the offences for which an “offender” need be convicted. It is also linked to an unclear definition of the term “undertrial”, which does not specify the nature of pending criminal proceedings and, therefore, could be used to describe simple offences such as, for example, failure to pay an electricity bill, which also attracts criminal penalties.
- The term “proficiency testing” that is defined in clause 2(1)(zb) is not used anywhere in the text of the DBT Bill and should be removed.
- The definitions of “quality assurance”, “quality manual” and “quality system” serve no enforceable purpose since they are used only in relation to the DNA Profiling Board’s rule-making powers under clauses 18 and 66. Their inclusion in the definitions clause is redundant. Accordingly, these definitions should be removed.
- The term “suspect” defined in clause 2(1)(zi) is vague and imprecise. The standard by which suspicion is to be measured, and by whom suspicion may be entertained – whether police or others, has not been specified. The term “suspect” is not defined in either the Code of Criminal Procedure, 1973 ("CrPC") or the Indian Penal Code, 1860 ("IPC").
The DNA Profiling Board - Clause 3 of the DBT Bill, which provides for the establishment of the DNA Profiling Board, contains a sub-clause (2) which vests the Board with corporate identity. This vesting of legal personality in the DNA Profiling Board – when other boards and authorities, even ministries and independent departments, and even the armed forces do not enjoy this function – is ill-advised and made without sufficient thought. Bodies corporate may be corporations sole – such the President of India, or corporations aggregate – such as companies. The intent of corporate identity is to create a fictional legal personality where none previously existed in order for the fictional legal personality to exist apart from its members, enjoy perpetual succession and to sue in its own legal name. Article 300 of the Constitution of India vests the Central Government with legal personality in the legal name of the Union of India and the State Governments with legal personality in the legal names of their respective states. Apart from this constitutional dispensation, some regulatory authorities, such as the Telecom Regulatory Authority of India ("TRAI") and the Securities and Exchange Board of India ("SEBI") have been individually vested with legal personalities as bodies corporate to enable their autonomous governance and independent functioning to secure their ability to free, fairly and impartially regulate the market free from governmental or private collusion. Similarly, some overarching national commissions, such as the Election Commission of India and the National Human Rights Commission ("NHRC") have been vested with the power to sue and be sued in their own names. In comparison, the DNA Profiling Board is neither an independent market regulator nor an overarching national commission with judicial powers. There is no legal reason for it to be vested with a legal personality on par with the Central Government or a company. Therefore, clause 3(2) should be removed.
- The size and composition of the Board that is staffed under clause 4 is extremely large. Creating unwieldy and top-heavy bureaucratic authorities and investing them with regulatory powers, including the powers of licensing, is avoidable. The DBT Bill proposes to create a Board of 16 members, most of them from a scientific background and including a few policemen and one legal administrator. In its present form, the Board is larger than many High Courts but does not have a single legal member able to conduct licensing. Drawing from the experiences of other administrative and regulatory bodies in India, the size of the Board should be drastically reduced to no more than five members, at least half of whom should be lawyers or ex-judges. The change in the legal composition of the Board is necessary because the DBT Bill contemplates that it will perform the legal function of licensing that must obey basic tenets of administrative law. The current membership may be viable only if the Board is divested of its administrative and regulatory powers and left with only scientific advice functions. Moreover, stacking the Board with scientists and policemen appears to ignore the perils that DNA collection and retention pose to the privacy of ordinary citizens and their criminal law rights. The Board should have adequate representation from the human rights community – both institutional (e.g NHRC and the State Human Rights Commissions) and non-institutional (well-regarded and experienced human rights activists). The Board should also have privacy advocates.
- Clauses 5(2) and 5(3) establish an unequal hierarchy within the Board by privileging some members with longer terms than others. There is no good reason for why the Vice-Chancellor of a National Law University, the Director General of Police of a State, the Director of a Central Forensic Science Laboratory and the Director of a State Forensic Science Laboratory should serve membership terms on the Board that are longer than those of molecular biologists, population geneticists and other scientists. Such artificial hierarchies should be removed at the outset. The Board should have one pre-eminent chairperson and other equal members with equal terms.
- The Chairperson of the Board, who is first mentioned in clause 5(1), has not been duly and properly appointed. Clause 4 should be modified to mention the appointment of the Chairperson and other Members.
- Clause 7 deals with the issue of conflict of interest in narrow cases. The clause requires members to react on a case-by-case basis to the business of the Board by recusing themselves from deliberations and voting where necessary. Instead, it may be more appropriate to require members to make a full and public disclosures of their real and potential conflicts of interest, and then granting the Chairperson the power to prevent such members from voting on interested matters. Failure to follow these anti-collusion and anti-corruption safeguards should attract criminal penalties.
- Clause 10 anticipates the appointment of a Chief Executive Officer of the Board who shall be a serving Joint Secretary to the Central Government. Clause 10(3) further requires this officer to be scientist. This may not be possible because the administrative hierarchy of the Central Government may not contain a genetic scientist.
- The functions of the Board specified in clause 12 are overbroad. Advising ministries, facilitating governments, recommending the size of funds and so on – these are administrative and governance functions best left to the executive. Once the Board is modified to have sufficient legal and human rights representation, then the functions of the Board can non-controversially include licensing, developing standards and norms, safeguarding privacy and other rights, ensuring public transparency, promoting information and debate and a few other limited functions necessary for a regulatory authority.
DNA Laboratories - The provisions of Chapters V and VI may be simplified and merged.
DNA Data Banks - The creation of multiple indices in clause 32(4) cannot be justified and must be removed. The collection of biological source material is an invasion of privacy that must be conducted only in strict conditions when the potential harm to individuals is outweighed by the public good. This balance may only be struck when dealing with the collection and profiling of samples from certain categories of offenders. The implications of collecting and profiling DNA samples from corpses, suspects, missing persons and others are vast and have either not been properly understood or deliberately ignored. At this moment, the forcible collection of biological source material should be restricted to the categories of offenders mentioned in the Identification of Prisoners Act, 1920 ("Prisoners Act") with a suitable addition for persons arrested in connection with certain specified terrorism-related offences. Therefore, databases should contain only an offenders’ index and a crime scene index.
- Clause 32(6), which requires the names of individuals to be connected to their profiles, and hence accessible to persons connected with the database, should be removed. DNA profiles, once developed, should be anonymised and retained separate from the names of their owners.
- Clause 36, which allows international disclosures of DNA profiles of Indians, should be removed immediately. Whereas an Indian may have legal remedies against the National DNA Data Bank, he/she certainly will not be able to enforce any rights against a foreign government or entity. This provision will be misused to rendition DNA profiles abroad for activities not permitted in India. Similarly, as in data protection regimes around the world, DNA profiles should remain within jurisdictions with high privacy and other legal standards.
Use - The only legitimate purpose for which DNA profiles may be used is for establishing the identity of individuals in criminal trials and confirming their presence or absence from a certain location. Accordingly, clauses 39 and 40 should be re-drafted to specify this sole forensic purpose and also specify the manner in which DNA profiles may be received in evidence. For more information on this point, see the relevant provisions of the CIS Note and the CIS Bill.
- The disclosure of DNA profiles should only take place to a law enforcement agency conducting a valid investigation into certain offences and to courts currently trying the individuals to whom the DNA profiles pertains. All other disclosures of DNA profiles should be made illegal. Non-consensual disclosure of DNA profiles for the study of population genetics is specifically illegal. The DBT Bill does not prescribe stringent criminal penalties and other mechanisms to affix individual liability on individual scientists and research institutions for improper use of DNA profiles; it is therefore open to the criticism that it seeks to sacrifice individual rights of persons, including the fundamental right to privacy, without parallel remedies and penalties. Clause 40 should be removed in entirety.
- Clause 43 should be removed in entirety. This note does not contemplate the retention of DNA profiles of suspects and victims, except as derived from a crime scene.
- Clause 45 sets out a post-conviction right related to criminal procedure and evidence. This would fundamentally alter the nature of India’s criminal justice system, which currently does not contain specific provisions for post-conviction testing rights. However, courts may re-try cases in certain narrow cases when fresh evidence is brought forth that has a nexus to the evidence upon which the person was convicted and if it can be proved that the fresh evidence was not earlier adduced due to bias. Any other fresh evidence that may be uncovered cannot prompt a new trial. Clause 45 is implicated by Article 20(2) of the Constitution of India and by section 300 of the CrPC. The principle of autrefois acquit that informs section 300 of the CrPC specifically deals with exceptions to the rule against double jeopardy that permit re-trials. [See, for instance, Sangeeta Mahendrabhai Patel (2012) 7 SCC 721].
Concerns Regarding DNA Law
Background
The Department of Biotechnology released, in 29 April 2012, a working draft of a proposed Human DNA Profiling Bill, 2012 ("DBT Bill") for public comments. The draft reveals an effort to (i) permit the collection of human blood, tissue and other samples for the purpose of creating DNA profiles, (ii) license private laboratories that create and store the profiles, (iii) store the DNA samples and profiles in various large databanks in a number of indices, and (iv) permit the use of the completed DNA profiles in scientific research and law enforcement. The regulation of human DNA profiling is of significant importance to the efficacy of law enforcement and the criminal justice system and correspondingly has a deep impact on the freedoms of ordinary citizens from profiling and monitoring. Below, we highlight five important concerns to bear in mind before drafting and implementing DNA legislation.
Primary Issues
Purpose of DNA Profiling
DNA profiling serves two broad purposes – (i) forensic – to establish unique identity of a person in the criminal justice system; and, (ii) research – to understand human genetics and its contribution to anthropology, biology and other sciences. These two purposes have very different approaches to DNA profiling and the issues and concerns attendant on them vary accordingly. Forensic DNA profiling is undertaken to afford either party in a criminal trial a better possibility of adducing corroborative evidence to prosecute, or to defend, an alleged offence. DNA, like fingerprints, is a biometric estimation of the individuality of a person. By itself, in the same manner that fingerprint evidence is only proof of the presence of a person at a particular place and not proof of the commission of a crime, DNA is merely corroborative evidence and cannot, on its own strength, result in a conviction or acquittal of an offence. Therefore, DNA and fingerprints, and the process by which they are collected and used as evidence, should be broadly similar.
Procedural Integrity
Forensic DNA profiling results from biological source material that is usually collected from crime scenes or forcibly from offenders and convicts. Biological source material found at a crime scene is very rarely non-contaminated and the procedure by which it is collected and its integrity ensured is of primary legislative importance. To avoid the danger of contaminated crime scene evidence being introduced in the criminal justice system to pervert the course of justice, it is crucial to ensure that DNA is collected only from intact human cells and not from compromised genetic material. Therefore, if the biological source material found at a crime scene does not contain at least one intact human cell, the whole of the biological source material should be destroyed to prevent the possibility of compromised genetic material being collected to yield inconclusive results. Adherence to this basic principle will obviate the possibility of partial matches of DNA profiles and the resulting controversy and confusion that ensues.
Conditions of Collection
In India, the taking of fingerprints is chiefly governed by the Identification of Prisoners Act, 1920 ("Prisoners Act") and section 73 of the Indian Evidence Act, 1872 ("Evidence Act"). The Prisoners Act permits the forcible taking of fingerprints from convicts and suspects in certain conditions. The Evidence Act, in addition, permits courts to require the taking of fingerprints for the forensic purpose of establishing unique identity in a criminal trial. No
provisions exist for consensual taking of fingerprints, presumably because of the danger of self-incrimination and general privacy concerns. Since, as discussed earlier, fingerprints and DNA are biometric measurements that should be treated equally to the extent possible, the conditions for the collection of DNA should be similar to those for the taking of fingerprints.Accordingly, there should be no legal provisions that enable other kinds of collection, including from volunteers and innocent people.
Retention of DNA
As a general rule applicable in India, the retention of biometric measurements must be supported by a clear purpose that is legitimate, judicially sanctioned and transparent. The Prisoners Act, which permits the forcible taking of fingerprints from convicts, also mandates the destruction of these fingerprints when the person is acquitted or discharged. The indefinite collection of biometric measurements of people is dangerous, susceptible to abuse and invasive of civil rights. Therefore, once lawfully collected from crime scenes and offenders, their DNA profiles must be retained in strictly controlled databases with highly restricted access for the forensic purpose of law enforcement only. DNA should not be held in databases that allow non-forensic use. Further, the indices within these databases should be watertight and exclusive of each other.
DNA Laboratories
The process by which DNA profiles are created from biological source material is of critical importance. Because of the evidentiary value of DNA profiles, the laboratories in which these profiles are created must be properly licensed, professionally managed and manned by competent and impartial personnel. Therefore, the process by which DNA laboratories are licensed and permitted to operate is significant.
Interview with Caspar Bowden - Privacy Advocate and former Chief Privacy Adviser at Microsoft
1. Do you think India needs privacy legislation? Why / Why not?
Well I think it's essential for any modern democracy based on a constitution to now recognise a universal human right to privacy. This isn't something that would necessarily have occurred to the draft of constitutions before the era of mass electronic communications, but this is now how everyone manages their lives and maintains social relationships at a distance, and therefore there needs to be an entrenched right to privacy – including communications privacy – as part of the core of any modern state.
2. The majority of India's population lives below the line of poverty and barely has any Internet access. Is surveillance an elitist issue or should it concern the entire population in the country? Why / Why not?
Although the majority of people in India are still living in conditions of poverty and don't have access to the Internet or, in some cases, to any electronic communications, that's changing very rapidly. India has some of the highest growth rates in take up with both mobile phones and mobile Internet and so this is spreading very rapidly through all strata of society. It's becoming an essential tool for transacting with business and government, so it's going to be increasingly important to have a privacy law which guarantees rights equally, no matter what anyone's social station or situation. There's also, I think, a sense in which having a right to privacy based on individual rights is much preferable to some sort of communitarian approach to privacy, which has a certain philosophical following; but that model of privacy - that somehow, because of a community benefit, there should also be a sort of community sacrifice in individual rights to privacy - has a number of serious philosophical flaws which we can talk about.
3. "I'm not a terrorist and I have nothing to hide...and thus surveillance can't affect me personally." Please comment.
Well, it's hard to know where to begin. Almost everybody in fact has “something to hide”, if you consider all of the social relationships and the way in which you are living your life. It's just not true that there's anybody who literally has nothing to hide and in fact I think that it's rather a dangerous idea, in political culture, to think about imposing that on leaders and politicians. There's an increasing growth of the idea – now, probably coming from America- that political leaders (and even their staff - to get hired in the current White House) should open up their lives, even to the extent of requiring officials to give up their passwords to their social network accounts (presumably so that they can be vetted for sources of potential political embarrassment in their private life). This is a very bad idea because if we only elect leaders, and if we only employ bureaucrats, who do not accord any subjective value to privacy, then it means we will almost literally be electing (philosophical) zombies. And we can't expect our political leaders to respect our privacy rights, if we don't recognise that they have a right to privacy in their own lives also. The main problem with the “nothing to hide, so nothing to fear” mantra is that this is used as a rhetorical tool by authoritarian forces in government and society, who simply wish to take a more paternalistic and protective attitude. This reflects a disillusionment within the “deep state” about how democratic states should function.
Essentially, those who govern us are given a license through elections to exercise power with consent, but this entails no abrogation of a citizen's duty to question authority. Instead, that should be seen as a civic duty - providing the objections are reasonable. People actually know that there are certain things in their lives that they don't wish other people to know, but by indoctrinating the “nothing to hide” ideology, it inculcates a general tendency towards more conformism in society, by inhibiting critical voices.
4. Should people have the right to give up their right to privacy? Why / Why not?
In European data protection law there is an obscure provision which is particularly relevant to medical privacy, but almost never used in the area of so-called sensitive personal data, like political views or philosophical views. It is possible currently for European governments to legislate to override the ability of the individual to consent. So this might arise, for example, if a foreign company sets up a service to get people to consent to have their DNA analysed and taken into foreign databases, or generally where people might consent to a big foreign company analysing and capturing their medical records. I think there is a legitimate view that, as a matter of national policy, a government could decide that these activities were threatening to data sovereignty, or that was just bad public policy. For example, if a country has a deeply-rooted social contract that guarantees the ability to access medical care through a national health service, private sector actors could try to undermine that social-solidarity basis for universal provision of health care. So for those sorts of reasons I do think it's defensible for governments to have the ability in those sectors to say: “Yes, there are areas where people should not be able to consent to give up their privacy!”
But then going back to the previous answer, more generally, commercial privacy policies are now so complicated – well, they've always been complicated, but now are mind-blowingly devious as well - people have no real possibility of knowing what they're consenting to. For example, the secondary uses of data flows in social networks are almost incomprehensible, even for technologists at the forefront of research. The French Data Protection authorities are trying to penalize Google for replacing several very complicated privacy policies by one so-called unified policy, which says almost nothing at all. There's no possible way for people to give informed consent to this over-simplified policy, because it doesn't even tell anything useful to an expert. So again in these circumstances, it's right for a regulator to intercede to prevent unfair exploitation of the deceptive kind of “tick-box” consent. Lastly, it is not possible for EU citizens to waive or trade away their basic right to access (or delete) their own data in future, because this seems a reckless act and it cannot be foreseen when this right might become essential in some future circumstances. So in these three senses, I believe it is proper for legislation to be able to prevent the abuse of the concept of consent.
5. Do you agree with India's UID scheme? Why / Why not?
There is a valid debate about whether it's useful for a country to have a national identity system of some kind - and there's about three different ways that can be engineered technically. The first way is to centralise all data storage in a massive repository, accessed through remote terminal devices. The second way is a more decentralised approach with a number of different identity databases or systems which can interoperate (or “federate” with eachother), with technical and procedural rules to enforce privacy and security safeguards. In general it's probably a better idea to decentralise identity information, because then if there is a big disaster (or cyber-attack) or data loss, you haven't lost everything. The third way is what's called “user-centric identity management”, where the devices (smartphones or computers) citizens use to interact with the system keep the identity information in a totally decentralised way.
Now the obvious objection to that is: “Well, if the data is decentralised and it's an official system, how can we trust that the information in people's possession is authentic?”. Well, you can solve that with cryptography. You can put digital signatures on the data, to show that the data hasn't been altered since it was originally verified. And that's a totally solved problem. However, unfortunately, not very many policy makers understand that and so are easily persuaded that centralization is the most efficient and secure design – but that hasn't been true technically for twenty years. Over that time, cryptographers have refined the techniques (the alogithms can now run comfortably on smartphones) so that user-centric identity management is totally achievable, but policy makers have not generally understood that. But there is no technical reason a totally user-centric vision of identity architecture should not be realized. But still the UID appears to be one of the most centralised large systems ever conceived.
There are still questions I don't understand about its technical architecture. For example, just creating an identity number by itself doesn't guarantee security and it's a classic mistake to treat an identifier as an authenticator. In other words, to use an identifier or knowledge of an identifier - which could become public information, like the American social security number – to treat knowledge of that number as if it were a key to open up a system to give people access to their own private information is very dangerous. So it's not clear to me how the UID system is designed in that way. It seems that by just quoting back a number, in some circumstances this will be the key to open up the system, to reveal private information, and that is an innately insecure approach. There may be details of the system I don't understand, but I think it's open to criticism on those systemic grounds.
And then more fundamentally, you have to ask what's the purpose of that system in society. You can define a system with a limited number of purposes – which is the better thing to do – and then quite closely specify the legal conditions under which that identity information can be used. It's much more problematic, I think, to try and just say that “we'll be the universal identity system”, and then you just try and find applications for it later. A number of countries tried this approach, for example Belgium around 2000, and they expected that having created a platform for identity, that many applications would follow and tie into the system. This really didn't happen, for a number of social and technical reasons which critics of the design had predicted. I suppose I would have to say that the UID system is almost the anithesis of the way I think identity systems should be designed, which should be based on quite strong technical privacy protection mechanisms - using cryptography - and where, as far as possible, you actually leave the custody of the data with the individual.
Another objection to this user-centric approach is “back-up”: what happens when you lose the primary information and/or your device? Well, you can anticipate that. You can arrange for this information to be backed-up and recovered, but in such a way that the back-up is encrypted, and the recovered copy can easily be checked for authenticity using cryptography.
6. Should Indian citizens be concerned about the Central Monitoring System (CMS)? Why / Why not?
Well, the Central Monitoring System does seem to be an example of very large scale “strategic surveillance”, as it is normally called. Many western countries have had these for a long time, but normally only for international communications. Normally surveillance of domestic communications is done under a particular warrant, which can only be applied one investigation at a time. And it's not clear to me that that is the case with the Central Monitoring System. It seems that this may also be applicable to mass surveillance of communications inside India. Now we're seeing a big controversy in the U.S - particularly at the moment - about the extent to which their international strategic surveillance systems are also able to be used internally. What has happened in the U.S. seems rather deceptive; although the “shell” of the framework of individual protection of rights was left in place, there are actually now so many exemptions when you look in the detail, that an awful lot of Americans' domestic communications are being subjected to this strategic mass surveillance. That is unacceptable in a democracy.
There are reasons why, arguably, it's necessary to have some sort of strategic surveillance in international communications, but what Edward Snowden revealed to us is that in the past few years many countries – the UK, the U.S, and probably also Germany, France and Sweden – have constructed mass surveillance systems which knowingly intrude on domestic communications also. We are living through a transformation in surveillance power, in which the State is becoming more able to monitor and control the population secretively than ever before in history. And it's very worrying that all of these systems appear to have been constructed without the knowledge of Parliaments and without precise legislation. Very few people in government even seem to have understood the true mind-boggling breadth of this new generation of strategic surveillance. And no elections were fought on a manifesto asking “Do people want this or not?”. It's being justified under a counter-terrorism mantra, without very much democratic scrutiny at all. The long term effects of these systems on democracies are really uncharted territory.
We know that we're not in an Orwellian state, but the model is becoming more Kafkaesque. If one knows that this level of intensive and automated surveillance exists, then it has a chilling effect on society. Even if not very much is publicly known about these systems, there is still a background effect that makes people more conformist and less politically active, less prepared to challenge authority. And that's going to be bad for democracy in the medium term – not just the long term.
7. Should surveillance technologies be treated as traditional arms / weapons? If so, should export controls be applied to surveillance technologies? Why / Why not?
Surveillance technologies probably do need to be treated as weapons, but not necessarily as traditional weapons. One probably is going to have to devise new forms of export control, because tangible bombs and guns are physical goods – well, they're not “goods”, they're “bads” - that you can trace by tagging and labelling them, but many of the “new generation” of surveillance weapons are software. It's very difficult to control the proliferation of bits – just as it is with copyrighted material. And I remember when I was working on some of these issues thirteen years ago in the UK – during the so-called crypto wars – that the export of cryptographic software from many countries was prohibited. And there were big test cases about whether the source code of these programs was protected under the US First Amendment, which would prohibit such controls on software code. It was intensely ironic that in order to control the proliferation of cryptography in software, governments seemed to be contemplating the introduction of strategic surveillance systems to detect (among other things) when cryptographic software was being exported. In other words, the kind of surveillance systems which motivated the “cypherpunks” to proselytise cryptography, were being introduced (partly) with the perverse justification of preventing such proliferation of such cryptography!
In the case of the new, very sophisticated software monitoring devices (“Trojans”) which are being implanted into people's computers – yes, this has to be subject to the same sort of human rights controls that we would have applied to the exports of weapon systems to oppressive regimes. But it's quite difficult to know how to do that. You have to tie responsibility to the companies that are producing them, but a simple system of end-user licensing might not work. So we might actually need governments to be much more proactive than they have been in the past with traditional arms export regimes and actually do much more actively to try and follow control after export – whether these systems are only being used by the intended countries. As for the law enforcement agencies of democratic countries which are buying these technologies: the big question is whether law enforcement agencies are actually applying effective legal and operational supervision over the use of those systems. So, it's a bit of a mess! And the attempts that have been made so far to legislate this area I don't think are sufficient.
8. How can individuals protect their data (and themselves) from spyware, such as FinFisher?
In democratic countries, with good system of the rule of law and supervision of law enforcement authorities, there have been cases – notably in Germany – where it's turned out that the police using techniques, like FinFisher, have actually disregarded legal requirements from court cases laying down the proper procedures. So I don't think it's good enough to assume that if one was doing ordinary lawful political campaigning, that one would not be targeted by these weapons. So it's wise for activists and advocates to think about protecting themselves – of course, other professions as well who look after confidential information – because these techniques may also get into the hands of industrial spies, private detectives and generally by people who are not subject to even the theoretical constraints of law enforcement agencies.
After Edward Snowden's revelations, we understand that all our computer infrastructure is much more vulnerable – particularly to foreign and domestic intelligence agencies – than we ever imagined. So for example, I don't use Microsoft software anymore – I think that there are techniques which are now being sold to governments and available to governments for penetrating Microsoft platforms and probably other major commercial platforms as well. So, I've made the choice, personally, to use free software – GNU/Linux, in particular – and it still requires more skill for most people to use, but it is much much easier than even a few years ago. So I think it's probably wise for most people to try and invest a little time getting rid of proprietary software if they care at all about societal freedom and privacy. I understand that using the latest, greatest smartphone is cool, and the entertainment and convenience of Cloud and tablets – but people should not imagine that they can keep those platforms secure.
It might sound a bit primitive, but I think people should have to go back to the idea that if they really want confidential communications with their friends, or if they are involved with political work, they have to think about setting aside one machine - which they keep offline and just use essentially for editing and encrypting/decrypting material. Once they've encrypted their work on their “air gap” machine, as it's called, then they can put their encrypted emails on a USB stick and transfer them to their second machine which they use to connect online (I notice Bruce Schneier is just now recommending the same approach). Once the “air gap” machine has been set up and configured, you should not connect that to the network – and preferably, don't connect it to the network, ever! So if you follow those sorts of protocols, that's probably the best that is achievable today.
9. How would you advise young people working in the surveillance industry?
Young people should try and read a little bit into the ethics of surveillance and to understand their own ethical limits in what they want to do, working in that industry. And in some sense, I think it's a bit like contemplating a career in the arms industry. There are defensible uses of military weapons, but the companies that build these weapons are, at the end of the day, just corporations maximizing value for shareholders. And so, you need to take a really hard look at the company that you're working for or the area you want to work in and satisfy your own standard of ethics, and that what you're doing is not violating other people's human rights. I think that in the fantastically explosive growth of surveillance industries that we've seen over the past few years – and it's accelerating – the sort of technologies particularly being developed for electronic mass surveillance are fundamentally and ethically problematic. And I think that for a talented engineer, there are probably better things that he/she can do with his/her career.
Mapping Digital Media: Broadcasting, Journalism and Activism in India: A Public Consultation
Respondents of various perspectives spoke for the public consultation regarding different sections of the Mapping Digital Media: India report.
On behalf of event organizers, we invite you to view the report, available online for free access here: "Mapping Digital Media: India.
Event organizers, Alternative Law Forum, The Centre for Internet & Society, and Maraa, held a public consultation at the Bangalore International Centre with the ultimate goals to inform and engage the public within key themes of the Mapping Digital Media: India report, as a new knowledge basis for better understanding India’s transitioning digital landscape. Many resulting ideas about moving forward with the report’s findings also came about, as prospective proceeding steps within the life cycle following the report’s release.
Respondents consisted of reputed media lawyers, researchers, journalists, activist and other media professionals. Each spoke before the meeting room within three panel discussions pertaining to different sections of the report: Policies, Laws and Regulators; Digital Activism; and Digital Journalism. Each speaker shed a new light on key challenges confronting our emergent digital media landscape with special focus given to broadcasting (radio and television), cable operations and newspapers (print & online) as each of these sectors undergo digitisation.
Opening
Vibodh Parthasarathi, who had anchored the country report, started off the consultation by underscoring the report's objective of mapping the different sectors and seemingly disparate aspects of India's complex media landscape. Following a brief introduction to the report was the setting of the stage by Alternative Law Forum Co-founder and Partner, Lawrence Liang, as he shared the ultimate aims of the event in speaking collectively to the report so that we may gain a better understanding of an area that is otherwise opaque by most. Lawrence also brings to the forefront the report’s debunking of the idea of the digital divide for India, and its account of a rich media landscape.
Policies, Laws and Regulators
The consultation’s first panel discussion was started by Lawrence, as he responded to the report from a perspective of legality. Lawrence examines the role of the state in India’s rich media landscape, specifically in terms of the four values at the centre of such: freedom of speech and expression, access to infrastructure, the question of development, and the question of market regulations—all of which are tied together within the country report. Lawrence argues that we must arrive at quantitative measures of accessing diversity and quantity of freedom of speech, but only after understanding the ecology in which freedom of speech operates, and attempts to do so in examining drafted policies, policing measures, and market regulatory measures taken within the context of India.
 Thirty attendees including journalists, activists, academics, and lawyers, all brought forth different perspectives on digital media in India. |
Following was Matthew John, Associate Professor and Executive Director of the Centre on Public law and Jurisprudence. Matthew shared his impressions on the report, while making reference to three issues the report asks us to rethink; these being: public reason, the regulatory state, and the question of distribution. Matthew gives rise to a democratic problem in the public sphere of communication and claims that how it is addressed and resolved must be paid attention to. He makes reference to the history of telecom cases in responding to the question of how we are going to think about freed up telecom, and contrasts different types of regulatory agencies in asking the question of whether or not we should separate regulation from politics. |
An engaging discussion following this panel’s speakers took place. Amongst points made by event attendees includes questions of how to scale up the citizen’s stake in media within a legal paradigm, as well as points made with reference to challenges to equity in media in terms of content and challenges to such.
Digital Media and Society (Digital Activism)
The discussion had begun with panelist, Arjun Venkatraman, Co-founder of the Mojolab Foundation as well as the digital activism platform, Swara. Arjun engages within the digital media debate in speaking on behalf of members of civil society that act from within the digital divide and exposes the gaps within new modes of activism that arise out of a lack of understanding on how to engage with these new medias. He also informed attendees of how to make cheap IVR based voice portals, linking voice users to the web for under USD200 as means of leveraging users’ voices via unlicensed spectrum.
Also contributing to the discussion on digital activism was Meera K, Cofounder of Bangalore News publication, Citizen Matters. In examining examples of new spaces that digital media has provided for the exchange of pluralistic views and alternative voices, Meera critiques different types of activism that have emerged, including social activism, political activism, and middle class activism. She questions whether new media can be seen as sufficient space for free speech with reference to various challenges, such as the polarization of debates, and also compares and contrasts the positive outcomes of new media campaigns—such as tangible capitalized solutions—with corresponding pitfalls.
A debate amongst attendees followed in response to the question of assessing the value of media in terms of impact or size of public outreach, along with how content is generated and controlled.
Digital Media and Journalism
Independent journalist and media analyst, Geeta Seshu, got the conversation started regarding digital media and journalism by comparing the pitfalls of journalism in traditional media with the possibilities offered by digital journalism. Geeta argues that journalists have become devalued and are losing their footing within traditional media. She discussed the new forms of journalism and how news can be generated in an interactive and non-hierarchical manner and examined the intersections of mainstream media and journalism. She questions the possibility of digital journalism existing on its own, without the influence of or incorporation of principles of traditional media, and grapples with possibilities for providing a new model for doing so.
The day’s last speaker was Subhash Rai, Associate Editor of New Indian Express. Subhash offers a mainstream perspective and argues that we must look at traditional and mainstream forms of media as a starting point for emerging forms of journalism before we can begin to understand these journalism models better. Just as well, traditional and mainstreams means of news dissemination can learn from digital media, however we should not be quick to look away from the core of the entire picture, as traditional forms of media are still very strong in comparison.
A discussion followed surrounded questions posed by speakers and attendees, such as what digital journalism should look like, and how such a transition to new forms of media should be imagined. How information has changed with respect to its creation and consumption was debated as well.
Moving Forward
Before the conclusion of the public consultation, attendees and speakers discussed future advancements for the country report. Many recommendations and ideas were generated, including suggestions for future public consultations, advocacy windows offered by the report, and ways to produce another iteration of the report. Prospective initiatives included online working groups to dive deeper into specific themes of the report, a Hackathon where attendees will pool ideas together, and follow-up public consultations.
|
|
|---|
| Participants brainstormed together on how to move forward the report’s findings. Many ideas were drafted, including a Hack-a-thon and online focus groups. |
The event's agenda went as follows:
| Time | Detail |
|---|---|
| 10.00 a.m. | Introductory Remarks by Vibodh Parthasarathi, CCMG, Jamia |
| 10.15 a.m. - 11.30 a.m. | Policies, Laws and Regulators Session Moderator – Ram Bhat Speakers – Lawrence Liang (ALF) and Mathew John (JGLS) |
| 11.30 a.m. - 11.45 a.m. |
Tea Break |
| 11.45 a.m. - 1.15 p.m. | Digital Media and Society (Digital Activism) Session Moderator – Lawrence Liang Speakers – Arjun Venkatraman (Mojolab) and Meera K (Citizen Matters) |
| 1.15 p.m. - 2.00 p.m. | Lunch Break |
| 2.00 p.m. - 3.15 p.m. | Digital Media and Journalism Session Moderator – Vibodh Parthasarathi Speakers – Geeta Seshu (Free Speech Hub) and Subhash Rai (newindianexpress.com) |
| 3.15 p.m. - 4.00 p.m. | The Way Ahead (Moving Forward) Moderated by Lawrence Liang |
Event Participants
- Rashmi Vallabhrajasyuva
- Meera K, Oorvani Foundation
- Samantha Cassar, CIS
- Sharath Chandra Ram, CIS
- Suresh Kumar, Artist
- Aruna Sekhar, Amnesty India
- Sriram Sharma, Part time Blogger
- Ammu Joseph, Independent Researcher
- Mathew John, Jindal Global Law School
- Swati Mehta, The Rules
- James North, The Rules
- Bhairav Acharya, Lawyer
- Deepa Kurup, The Hindu
- Abhilash N, Independent
- Deepu, Pedestrian Pictures
- Rashmi M, PhD Student at NIAS
- Jayanth S, LOCON Solutions Pvt Ltd.
- Nehaa Chaudhari, CIS
- Dinesh TB, Servelots
- Snehashish Ghosh, CIS
- Lawrence Liang, ALF
- Vibodh Parthasarathi, CCMG, Jamia
- Ram Bhat, Maraa
- Ashish Sen, AMARC
- Subhash Rai, New Indian Express
- Geeta Seshu, Free Speech Hub, The Hoot
- Arjun Venkatraman, Mojo Lab Foundation
- Raajen, Centre for Education and Documentation
- Ekta, Maraa
- Smarika Kumar, ALF
Press Coverage
- Need to increase diversity in online journalism (The New Indian Express, October 28, 2013).
- Experts moot holistic approach to media laws (The Hindu, October 28, 2013).
CIS Cybersecurity Series (Part 12) - Namita Malhotra
"In a strange mix of how both capitalism and state control work, what is happening is that more and more of these places that one could access, for various reasons, whether it is for ones own pleasure or for political conversations, are getting further and further away from us. And I think that that mix of both corporate interests and state control is particularly playing a role in this regard." - Namita Malhotra, researcher and lawyer, Alternative Law Forum
Centre for Internet and Society presents its twelfth installment of the CIS Cybersecurity Series.
The CIS Cybersecurity Series seeks to address hotly debated aspects of cybersecurity and hopes to encourage wider public discourse around the topic.
Namita Malhotra is a researcher and lawyer at Alternative Law Forum (ALF). She has a keen interest in working on law, technology and media through legal research, cultural studies, new media practices and film making.
ALF homepage: www.altlawforum.org
This work was carried out as part of the Cyber Stewards Network with aid of a grant from the International Development Research Centre, Ottawa, Canada.
First Look: CIS Cybersecurity documentary film
The Centre for Internet and Society is pleased to release the trailer of its first documentary film, on cybersecurity and civil society in India.
The documentary is part of the CIS Cybersecurity Series, a work in progress which may be found here.
DesiSec: Cybersecurity and Civil Society in India
The trailer of DesiSec: Cybersecurity and Civil Society in India was shown at the Internet Governance Forum in Bali on October 24. It was a featured presentation at the Citizen Lab workshop, Internet Governance For The Next Billion Users.
The transcript of the workshop is available here: http://www.intgovforum.org/cms/component/content/article/121-preparatory-process/1476-ws-344-internet-governance-for-the-next-billion-users
This work was carried out as part of the Cyber Stewards Network with aid of a grant from the International Development Research Centre, Ottawa, Canada.
Seventh Privacy Round-table
The Round-table was the last in a series of seven, beginning in April 2013, which were held across India.
Previous Privacy Round-tables were held in:
- New Delhi: (April 13, 2013) with 45 participants;
- Bangalore: (April 20, 2013) with 45 participants;
- Chennai: (May 18, 2013) with 25 participants;
- Mumbai, (June 15, 2013) with 20 participants;
- Kolkata: (July 13, 2013) with 25 participants; and
- New Delhi: (August 24, 2013) with 40 participants.
Chantal Bernier, Assistant Privacy Commissioner Canada, Jacob Kohnstamm, Dutch Data Protection Authority and Chairman of the Article 29 Working Party, and Christopher Graham, Information Commissioner UK were the featured speakers for this event.
The Privacy Round-tables were organised to ignite spark in public dialogues and gain feedback for a privacy framework for India. To achieve this, the Privacy Protection Bill, 2013, drafted by the Centre for Internet and Society, Strengthening Privacy through Co-regulation by the Data Security Council of India, and the Report of the Group of Experts on Privacy by the Justice A.P. Shah committee were used as background documents for the Round-tables. As a note, after each Round-table, CIS revised the text of the Privacy Protection Bill, 2013 based on feedback gathered from the general public.
The Seventh Privacy Round-table meeting began with an overview of the past round-tables and a description of the evolution of a privacy legislation in India till date, and an overview of the Indian interception regime. In 2011, the Department of Personnel and Training drafted a Privacy Bill that incorporated provisions regulating data protection, surveillance, interception of communications, and unsolicited messages. Since 2010, India has been seeking data secure status from the European Union, and in 2012 a report was issued noting that the Reasonable Security Practices and Procedures and Sensitive Personal Data or Information Rules found under section 43A of the Information Technology Act, were not sufficient to meet EU data secure adequacy. In 2012, the Report of the Group of Experts on Privacy was published recommending a privacy framework for India and was accepted by the government, and the Department of Personnel and Training is presently responsible for drafting of a privacy legislation for India.
Presentation: Jacob Kohnstamm, Dutch Data Protection Authority and Chairman of the Article 29 Working Group
Jacob Kohnstamm, made a presentation on the privacy framework in the European Union. In his presentation, Khonstamm shared how history, such as the Second World War, shaped the present understanding and legal framework for privacy in the European Union, where privacy is seen as a fundamental human right. Kohnstamm also explained how over the years technological developments have made data gold, and subsequently, companies who process this data and create services that allow for the generation of more data are becoming monopolies. This has created an unbalanced situation for the individual consumer, where his or her data is being routinely collected by companies, and once collected — the individual loses control over the data. Because of this asymmetric relationship, data protection regulations are critical to ensure that individual rights are safeguarded.
Kohnstamm recognized the tension between stringent data protection regulations and security for the government, and the provision of services for businesses was recognized. However, he argued that the use of technology without regulation — for commercial reason or security reasons, can lead to harm. Thus, it is key that any regulation incorporate proportionality as a cornerstone to the use of these technologies to ensure trust between the individual and the State, and the individual and the corporation. This will also ensure that individuals are given the right of equality, and the right to live free of discrimination. Kohnstamm went on to explain that any regulation needs to ensure that individuals are provided the necessary tools to control their data and that a robust supervisory authority is established with enough powers to enforce the provisions, and that checks and balances are put in place to safeguard against abuse.
In response to a question asked about how the EU addresses the tension of data protection and national security, Kohnstamm clarified that in the EU, national security is left as a matter for member states to address but the main principles found in the EU Data Protection Directive also apply to the handling of information for national security purposes. He emphasized the importance of the creation of checks and balances. As security agencies are given additional and broader powers, they must also be subjected to stronger safeguards.
Kohnstamm also discussed the history of the fair trade agreement with India, and India’s request for data secure status. It was noted that currently the fair trade agreement between India and the EU is stalled, as India has asked for data secure status. For the EU to grant this status, it must be satisfied that when European data is transferred and processed in India and that it is subject to the same level of protections as it would be if it were processed in the EU. Without a privacy legislation in place, India’s present regime does not reflect the same level of protections as the EU regime. To find a way out of this ‘dead lock’, the EU and India have agreed to set up an expert group — with experts from both the EU and India to find a way in which India’s regime can be modified to meet EU date secure adequacy. As of date, no experts from the Indian side have been nominated and communicated to the EU.
Key Points:
- Europe’s history has influenced the understanding and formulation of the right to privacy as a fundamental right.
- Any privacy regulation must have strong checks and balances in place and ensure that individuals are given the tools to control their data.
- India’s current regime does not meet EU data secure adequacy. Currently, the EU is waiting for India to nominate experts to work with the EU to find a way of the ‘dead lock’.
Discussion: National Security, Surveillance and Privacy
Opening the discussion up to the floor, it was discussed how in India, there is a tension between data protection and national security, as national security is always a blanket exception to the right to privacy. This tension has been discussed and debated by both democratic institutions in India and commercial entities. It was pointed out that though data protection is a new debate, national security is a debate that has existed in India for many years. It was also pointed out that currently there are not sufficient checks and balances for the powers given to Indian security agencies. One missing safeguard that the Indian regime has been heavily criticized for is the power of the Secretary of the Home Ministry to authorize interception requests, as having the authorization power vested in the executive leaves little space between interested parties seeking approval of interception orders, and could result in abuse or conflict of interest. With regards to the Indian interception regime, it was explained that currently there are five ways in which messages can be intercepted in India. Previously, the Law Commission of India had asked that amendments be made to both the Indian Post Office Act and the Indian Telegraph Act.
Moving the discussion to the Privacy Protection Bill, 2013 by CIS, in Chapter V “Surveillance and Interception of Communications” clause 34, the authorization of interception and surveillance orders is left to a magistrate. Previously, the authorization of interception orders rested with the Privacy Commissioner, but this model was heavily critiqued in previous round-tables, and the authorizing authority has been subsequently changed to a magistrate. Participants pointed out that the Bill should specify the level of the magistrate that will be responsible for the authorization of surveillance orders, and also raised the concern that the lower judiciary in India is not adequately functioning as the courts are overwhelmed, thus creating the possibility for abuse. Participants also suggested that perhaps data protection and surveillance should be de-linked from each other and placed in separate bills. This echoes public feedback from previous roundtables.
While discussing needed safeguards in an interception and surveillance regime for India, it was called out that transparency of surveillance, by both the government and the service providers as key safeguards to ensuring the protection of privacy, as it would enable individuals to make educated decisions about the services they choose to use and the extent of governmental surveillance. The need to bring in a provision that incorporated the idea of "nexus of surveillance" was also highlighted. It was also pointed out that in Canada, entities wanting to deploy surveillance in the name of public safety, must take steps to prove nexus. For example, the organization must empirically prove that there is a need for a security requirement, demonstrate that only data that is absolutely necessary will be collected, show how the technology will be effective, prove that there is not a less invasive way to collect the information, demonstrate security measures in place to ensure against loss and misuse, and the organizations must have in place both internal and external oversight mechanisms. It was also shared that in Canada, security agencies are regulated by the Office of the Canadian Privacy Commissioner, as privacy and security are not seen as separate matters. In the Canadian regime, because security agencies have more powers, they are also subjected to greater oversight.
Key Points:
- The Indian surveillance regime currently does not have strong enough safeguards.
- The concept of ‘nexus’ should be incorporated into the Privacy Protection Bill, 2013.
- A magistrate, through judicial oversight for interception and surveillance requests, might not be the most effective authority for this role in India.
Presentation: Chantal Bernier, Deputy Privacy Commissioner, Canada
In her presentation, Bernier made the note that in the Canadian model there are multiple legislative initiatives that are separate but connected, and all provide a legislative basis for the right to privacy. Furthermore, it was pointed out that there are two privacy legislations in Canada, one regulating the private sector and the other regulating the public sector. It has been structured this way as it is understood that the relationship between individuals and business is based on consent, while the relationship between individuals and the state is based on human rights. Furthermore, aspects of privacy, such as consent are different in the public sector and the private sector. In her presentation, Bernier pointed out that privacy is a global issue and because of this, it is critical that countries have privacy regimes that can speak to each other. This does not mean that the regimes must be identical, but they must at the least be inter-operable.
Bernier described three main characteristics of the Canadian privacy regime including:
- It is comprehensive and applies to both the public and the private sectors.
- The right to privacy in Canada is constitutionally based and is a fundamental right as it is attached to personal integrity. This means that privacy is above contractual fairness. That said, the right to privacy must be balanced collectively with other imperatives.
- The Canadian privacy regime is principle based and not rule based. This flexible model allows for quick adaption to changing technologies and societal norms. Furthermore, Bernier explained how Canada places responsibility and accountability on companies to respect, protect, and secure privacy in the way in which the company believes it can meet. Bernier also noted that all companies are responsible and accountable for any data that they outsource for processing.
Furthermore, any company that substantially deals with Canadians must ensure that the forum for which complaints etc., are heard is Canada. Furthermore, under the Canadian privacy regime, accountability for data protection rests with the original data holder who must ensure — through contractual clauses — that any information processed through a third party meets the Canadian level of protection. This means any company that deals with a Canadian company will be required to meet the Canadian standards for data protection.
Speaking to the governance structure of the Office of the Privacy Commissioner in Canada, Bernier explained that the OPC is a completely independent office and reports directly to the Parliament. The OPC hears complaints from both individuals and organizations. The OPC does not have any enforcement powers, such as finding a company, but does have the ability to "name" companies who are not in compliance with Canadian regulations, if it is in the public interest to do so. The OPC can perform audits upon discretion with respect to the public sector, and can perform audits on the private sector if they have reasonable grounds to investigate.
Bernier concluded her presentation with lessons that have been learned from the Canadian experience including:
- The importance of having strong regulators.
- Privacy regulators must work and cooperate together.
- Privacy has become a condition of trade.
- In today’s age, issues around surveillance cannot be underestimated.
- Companies that have strong privacy practices now have a competitive advantage in place in today’s global market.
- Privacy frameworks must be clear and flexible.
- Oversight must be powerful to ensure proper protection of citizens in a world of asymmetry between individuals, corporations, and governments.
Key Points:
- The Right to Privacy is a fundamental right in Canada.
- The Canadian privacy regime regulates the public sector and the private sector, but through two separate legislations.
- The OPC does not have the power to levy fines, but does have the power to conduct audits and investigations and ‘name’ companies who are not in compliance with Canadian regulations if it is in the public interest.
Discussion: The Data Protection Authority
Participants also discussed the composition of the Data Protection Authority as described in chapter IV of the Privacy Protection Bill. It was called out that the in the Bill, the Data Protection Authority might need to be made more independent. It was suggested that to avoid having the office of the Data Protection Authority be filled with bureaucrats, the Bill should specify that the office must be staffed by individuals with IT experience, lawyers, judges, etc. On the other hand it was cautioned, that though this might be useful to some extent, it might not be helpful to be overly prescriptive, as there is no set profile of what composition of employees makes for a strong and effective Data Protection Authority. Instead the Bill should ensure that the office of the Data Protection Authority is independent, accountable, and chosen by an independent selection board.
When discussing possible models for the framework of the Data Protection Authority, it was pointed out that there are many models that could be adopted. Currently in India the commission model is not flexible, and many commissions that are set up, are not effective due to funding and internal bureaucracy. Taking that into account, in the Privacy Protection Bill, 2013, the Data Protection Authority, could be established as a small regulator with an appellate body to hear complaints.
Key Points:
- The Data Protection Authority established in the Privacy Protection Bill must be adequately independent.
- The composition of the Data Protection Authority be diverse and it should have the competence to address the dynamic nature of privacy.
- The Data Protection Authority could be established as a small regulator with an appellate body attached.
Presentation: Christopher Graham, Information Commissioner, United Kingdom
Christopher Graham, the UK Information Commissioner, spoke about the privacy regime in the United Kingdom and his role as the UK Information Commissioner. As the UK Information Commissioner, his office is responsible for both the UK Data Protection Act and the Freedom of Information Act. In this way, the right to know is not in opposition to the right to privacy, but instead an integral part.
Graham said that his office also provides advice to data controllers on how to comply with the privacy principles found in the Data Protection Act, and his office has the power to fine up to half a million pounds on non-compliant data controllers. Despite having this power, it is rarely used, as a smaller fine is usually sufficient enough for the desired effect. Yet, at the end of the day, whatever penalty is levied, it must be proportionate and risk based i.e., selective to be effective. In this way the regulatory regime should not be heavy handed but instead should be subtle and effective. In fact, one of the strongest regulators is the reality of the market place where the price of not having strong standards is innovation and economic growth. To this extent, Graham also pointed out that self regulation and co-regulation are both workable models, if there is strong enforcement mechanisms. Graham emphasized the fact that any data protection must go beyond, and cannot be limited to, just security.
Graham also explained that he has found that currently there is a lack of confidence in Indian partners. This is problematic as the Indian industry tries to grow with European partners. For example, he has been told that customers are moving banks because their previous bank’s back offices were located in India. Citing other examples of cases of data breaches from Indian data controllers, such as a call center merging the accounts of two customers and another call centre selling customer information, he explained that the lack of confidence in the Indian regime has real economic implications. Graham further explained that one difficulty that the office of the UK ICO is faced with, is that India does not have the equivalent of the ICO. Thus, when a breach does happen, it is unclear who can be approached in India about the breach.
Touching upon the issue of data adequacy with the EU, Graham noted that if data adequacy is a goal of India, the privacy principles as defined in the Directive and reflected in the UK Data Protection Act, must be addressed in addition to security. In his presentation, Graham emphasized the importance of India amending their current regime, if they want data secure status and spoke about the economic benefits for both Europe and India, if India does in fact obtain data secure status. In response to a question about why it is so important that India amend its laws, if in effect the UK has the ability to enforce the provisions of UK Data Protection Act, Graham clarified that most important is the rule of law, and according to UK law and more broadly the EU Directive, companies cannot transfer information to jurisdictions that do not have recognized adequate levels of protection. Thus, if companies still wish to transfer information to India, this must be done through binding corporate rules.
Another question which was put forth was about how the right to privacy differs from other human rights, and why countries are requiring that other countries to uphold the right to privacy to the same level, when, for example this is not practiced for other human rights such as children’s rights. In response Graham explained that data belongs to the individual, and when it is transferred to another country — it still belongs to the individual. Although the UK would like all countries to uphold the rights of children to the standard that they do, the UK is not exporting UK citizen’s children to India. Thus, as the Information Commissioner he has a responsibility to protect his citizen’s data, even when it leaves the UK jurisdiction. Graham explained further that in the history of Europe, the misuse of data to do harm has been a common trend, which is why privacy is seen as a fundamental right, and why it is paramount that European data is subject to the same level of protection no matter what jurisdiction it is in. India needs to understand that privacy is a fundamental right and goes beyond security, and that when a company processes data it does not own the data, the individual owns the data and thus has rights attached to it to understand why Europe requires countries to be ‘data secure’ before transferring data to them.
Key Points:
- The UK Information Commissioners Office regulates both the right to information and privacy, and thus the two rights are seen as integral to each other.
- Penalties must be proportionate and scalable to the offense.
- Co-regulation and self-regulation can both be viable models to for privacy, but enforcement is key to them being effective.
Discussion: Collection of Data with Consent and Collection of Data without Consent
Participants also discussed the collection of data with consent and the collection of data without consent found in Chapter III of the Bill. When asked opinions about the circumstances when informed consent should not be required, it was pointed out that in the Canadian model, the option to collect information without consent only applies to the public sector if it is necessary for the delivery of a service by the government. In the private sector all collection of information requires informed and meaningful consent. Yet, collection of data without consent in the commercial context is an area that Canada is wrestling with, as there are instances, such as online advertising, where it is unreasonable to expect consent all the time. It was also pointed out that in the European Directive, consent is only one of the seven grounds under which data can be collected. As part of the conversation on consent, it was pointed out that the Bill currently does not take explicitly take into account the consent for transfer of information, and it does not address changing terms of service and if companies must re-take consent, or if providing notice to the individual was sufficient. The question about consent and additional collection of data that is generated through use of that service was also raised. For example, if an individual signs up for a mobile connection and initially provides information that the service provider stores in accordance to the privacy principles, does the service provider have an obligation to treat all data generated by the user while using the service of the same? The exception of disclosure without consent was also raised and it was pointed out that companies are required to disclose information to law enforcement when required. For example, telecom service providers must now store location data of all subscribers for up to 6 months and share the same when requested by law enforcement.
Key Points:
- There are instances where expecting companies to have informed consent for every collection of information is not reasonable. Alternative models, based on — for example transparency — must be explored to address these situations.
- The Privacy Protection Bill should explicitly address transfer of information to other countries.
- The Privacy Protection Bill should address consent in the context of changing terms of service.
Discussion: Penalties and Offences
The penalties and offenses prescribed in chapter VI of the Privacy Protection Bill were discussed by participants. While discussing the chapter, many different opinions were voiced. For example, some participants held the opinion that offences and penalties should not exist in the Privacy Protection Bill, because in reality they are more likely than not to be effective. For example, when litigating civil penalties, it takes a long time for the money to be realized. Others argued that in India, where enforcement of any law is often weak, strong, clear, and well defined criminal penalties are needed. Another comment raised the point that a distinction should be made between breaches of the law by data controllers and breaches by rogue individuals — as the type of violation. For example, a breach by a data controller is often a matter identifying the breach and putting in place strictures to ensure that it does not happen again by holding the company accountable through oversight. Where as a breach by a rogue agent entails identifying the breach and the rogue agent and creating a strong enough penalty to ensure that they will not repeat the violation. Adding to this discussion, it was pointed out that in the end, scalability is key in ensuring that penalties are proportional and effective. It was also noted that in the UK, any fine that is levied is appealable. This builds in a system of checks and balances, and ensures that companies and individuals are not subject to unfair or burdensome penalties.
The possibility of incentivizing compliance, through rewards and distinctions, was discussed by participants. Some felt that incentivizing compliance would be more effective as it would give companies distinct advantages to incorporating privacy protections, while others felt that incentives can be included but penalties cannot be excluded, otherwise the provisions of the Privacy Protection Bill 2013 will not be enforceable. It was also pointed out that in the context of India, ideally there should be a mechanism to address the ‘leakages’ that happen in the system i.e., corruption. Though this is difficult to achieve, regulations could take steps like specifically prohibiting the voluntary disclosure of information by companies to law enforcement. Taking a sectoral approach to penalties was also suggested as companies in different sectors face specific challenges and types of breaches. Another approach that could be implemented is the statement of a time limit for data controllers and commissioners to respond to complaints. This has worked for the implementation of the Right to Information Act in India, and it would be interesting to see how it plays out for the right to privacy. Throughout the discussion a number of different possible ways to structure offenses and penalties were suggested, but for all of them it was clear that it is important to be creative about the type of penalties and not rely only on financial penalty, as for many companies, a fine has less of an impact than perhaps having to publicly disclose what happened around a data breach.
Key Points:
- Penalties and offenses by companies vs. rogue agents should be separately addressed in the Bill.
- Instead of levying penalties, the Bill should include incentives to ensure compliance.
- Penalties for companies should go beyond fines and include mechanisms such as requiring the company to disclose to the public information about the breach.
Discussion: Cultural Aspects of Privacy
The cultural realities of India, and the subsequent impact on the perception of privacy in India were discussed. It was pointed out that India has a history of colonization, multiple religions and languages, ethnic tensions, a communal based society, and a large population. All of these factors impact understandings, perceptions, practices, and the effectiveness of different frameworks around privacy in India. For example, the point was raised that given India’s cultural and political diversity, having a principle based model might be too difficult to enforce as every judge, authority, and regulator will have a different perspective and agenda. Other participants pointed out that there is a lack of awareness around privacy in India, and this will impact the effectiveness of the regulation. It was also highlighted that anecdotal claims that cultural privacy in India is different, such as the fact that in India on a train everyone will ask you personal questions, and thus Indian’s do not have a concept of privacy, cannot influence how a privacy law is framed for India.
Key Points:
- India’s diverse culture will impact perceptions of privacy and the implementation of any privacy regulation.
- Given India’s diversity, a principle based model might not be adequate.
- Though culture is important to understand and incorporate into the framing of any privacy regulation in India, anecdotal stories and broad assumptions about India’s culture and societal norms around privacy cannot influence how a privacy law is framed for India.
Conclusion
The seventh privacy round-table concluded with a conversation on the NSA spying and the Snowden Revelations. It was asked if domestic servers could be an answer to protect Indian data. Participants agreed that domestic servers are just a band aid to the problem. With regards to the Privacy Protection Bill it was clarified that CIS is now in the process of collecting public statements to the Bill and will be submitting a revised version to the Department of Personnel and Training. Speaking to the privacy debate at large, it was emphasized that every stakeholder has an important voice and can impact the framing of a privacy law in India.
Why 'Facebook' is More Dangerous than the Government Spying on You
Do you have a profile on Facebook? Almost every time I ask this question, the answer is ‘yes’. In fact, I think the amount of people who have replied ‘no’ to this question can literally be counted on my right hand. But this is not an article about Facebook per se. It’s more about the ‘Facebooks’ of the world, and of people’s increasing “choice” to hand over their most personal data. More accurate questions are probably:
“Would you like the Government to go through your personal diary? If not, then why do you have a profile on Facebook?”
The Indian Surveillance State
Following Snowden’s revelations, there’s finally been more talk about surveillance. But what is surveillance?
David Lyon - who directs the Surveillance Studies Centre - defines surveillance as “any collection and processing of personal data, whether identifiable or not, for the purposes of influencing or managing those whose data have been garnered”. Surveillance can also be defined as the monitoring of the behaviour, activities or other changing information of individuals or groups of people. However, this definition implies that individuals and/or groups of people are being monitored in a top-down manner, without this being their “choice”. But is that actually the case? To answer this question, let’s have a look at how the Indian government and corporations operating in India spy on us.
State Surveillance
The first things that probably come to mind when thinking about India from a foreigner’s perspective are poverty and corruption. Surveillance appears to be a “Western, elitist issue”, which mainly concerns those who have already solved their main survival problems. In other words, the most mainstream argument I hear in India is that surveillance is not a real issue, especially since the majority of the population in the country lives below the line of poverty and does not even have any Internet access. Interestingly enough though, the other day when I was walking around a slum in Koramangala, I noticed that most people have Airtel satellites...even though they barely have any clean water!
The point though is that surveillance in India is a fact, and the state plays a rather large role in it. In particular, Indian law enforcement agencies follow three steps in ensuring that targeted and mass surveillance is carried out in the country:
1. They create surveillance schemes, such as the Central Monitoring System (CMS), which carry out targeted and/or mass surveillance
2. They create laws, guidelines and license agreements, such as the Information Technology (Amendment) Act 2008, which mandate targeted and mass surveillance and which require ISP and telecom operators to comply
3. They buy surveillance technologies from companies, such as CCTV cameras and spyware, and use them to carry out targeted and/or mass surveillance
While Indian law enforcement agencies don’t necessarily follow these steps in this precise order, they usually try to create surveillance schemes, legalise them and then buy the gear to carry them out.
In particular, surveillance in India is regulated under five laws: the Indian Telegraph Act 1885, the Indian Post Office Act 1898, the Indian Wireless Telegraphy Act 1933, section 91 of the 1973 Code of Criminal Procedure (CrPc) and the Information Technology (Amendment) Act 2008. These laws mandate targeted surveillance, but remain silent on the issue of mass surveillance which means that technically it is neither allowed nor prohibited, but remains a grey legal area.
While surveillance laws in India may not mandate mass surveillance, some of their sections are particularly concerning. Section 69 of the Information Technology (Amendment) Act 2008 allows for the interception of all information transmitted through a computer resource, while requiring that all users disclose their private encryption keys or face a jail sentence of up to seven years. This appears to be quite bizarre, as individuals can only keep their data private and protect themselves from surveillance through encryption.
Section 44 of the Information Technology (Amendment) Act 2008 imposes stiff penalties on anyone who fails to provide requested information to authorities - which kind of reminds us of Orwell’s totalitarian regime in “1984”. Furthermore, section 66A of the same law states that individuals will be punished for sending “offensive messages through communication services”. However, the vagueness of this section raises huge concerns, as it remains unclear what defines an “offensive message” and whether this will have grave implications on the freedom of expression. The arrest of two Indian women last November over a Facebook post reminds us of this.
Laws in India may not mandate mass surveillance, but guidelines and license agreements issued by the Department of Telecommunications do. In particular, the UAS License Agreement regarding the Central Monitoring System (CMS) not only mandates mass surveillance, but also attempts to legalise a mass surveillance scheme which aims to intercept all telecommunications and Internet communications in India. Furthermore, the Department of Telecommunications has issued numerous guidelines and license agreements for ISPs and telecom operators, which require them to not only be “surveillance-friendly”, but to also enable law enforcement agencies to tap into their servers on the grounds of national security. And then, of course, there’s the new National Cyber Security Policy, which mandates surveillance to tackle cyber-crime, cyber-terrorism, cyber-war and cyber-vandalism.
As both a result and prerequisite of these laws, the Indian government has created various surveillance schemes and teams to aid them. In particular, India’s Computer Emergency Response Team (CERT) is currently monitoring “any suspicious move on the Internet” in order to checkmate any potential cyber attacks from hackers. While this may be useful for the purpose of preventing and detecting cyber-criminals, it remains unclear how “any suspicious move” is defined and whether that inevitably enables mass surveillance, without individuals’ knowledge or consent.
The Crime and Criminal Tracking and Network & Systems (CCTNS) is the creation of a nationwide networking infrastructure for enhancing the efficiency and effectiveness of policing and sharing data among 14,000 police stations across the country. It has been estimated that Rs. 2000 crore has been allocated for the CCTNS project and while it may potentially increase the effectiveness of tackling crime and terrorism, it raises questions around the legality of data sharing and its potential implications on the right to privacy and other human rights - especially if such data sharing results in data being disclosed or shared with unauthorised third parties.
Similarly, the National Intelligence Grid (NATGRID) is an integrated intelligence grid that will link the databases of several departments and ministries of the Government of India so as to collect comprehensive patterns of intelligence that can be readily accessed by intelligence agencies. This was first proposed in the aftermath of the Mumbai 2008 terrorist attacks and while it may potentially aid intelligence agencies in countering crime and terrorism, enforced privacy legislation should be a prerequisite, which would safeguard our data from potential abuse.
However, the most controversial surveillance scheme being implemented in India is probably the Central Monitoring System (CMS). While several states, such as Assam, already have Internet Monitoring Systems in place, the Central Monitoring System appears to raise even graver concerns. In particular, the CMS is a system through which all telecommunications and Internet communications in India will be monitored by Indian authorities. In other words, the CMS will be capable of intercepting our calls and of analyzing our data on social networking sites, while all such data would be retained in a centralised database. Given that India currently lacks privacy legislation, such a system would mostly be unregulated and would pose major threats to our right to privacy and other human rights. Given that data would be centrally stored, the system would create a type of “honeypot” for centralised cyber attacks. Given that the centralised database would have massive volumes of data for literally a billion people, the probability of error in pattern and profile matching would be high - which could potentially result in innocent people being convicted for crimes they did not commit. Nonetheless, mass surveillance through the CMS is currently a reality in India.
And the even bigger question: How can law enforcement agencies mine the data of 1.2 billion people? How do they even carry out surveillance in practice? Well, that’s where surveillance technology companies come in. In fact, the surveillance industry in India is massively expanding - especially in light of its new surveillance schemes which require advanced and sophisticated technology. According to CIS’ India Privacy Monitor Map - which is part of ongoing research - Indian law enforcement agencies use CCTV cameras in pretty much every single state in India. The map also shows that Unmanned Aerial Vehicles (UAVs), otherwise known as drones, are being used in most states in India and the DRDO’s “Netra” - which is a lightweight drone, not much bigger than a bird - is particularly noteworthy.
But Indian law enforcement agencies also buy surveillance software and hardware which is aimed at intercepting telecommunications and Internet communications. In particular, ClearTrail Technologies is an Indian company - based in Indore - which equips law enforcement agencies in India and around the world with surveillance software which can probably be compared with the “notorious” FinFisher. So in short, there appears to be a tight collaboration between Indian law enforcement agencies and the surveillance industry, which can be clearly depicted in the ISS surveillance trade shows, otherwise known as “the wiretappers’ ball”.
Corporate Surveillance
When I ask people about corporate surveillance, the answer I usually get is: “Corporations only care about their profit - they don’t do surveillance per se”. And while that may be true, David Lyon’s definition of surveillance - as “any collection and processing of personal data, whether identifiable or not, for the purposes of influencing or managing those whose data have been garnered” - may indicate otherwise.
Corporations, like Google, Amazon and Facebook, may not have an agenda for spying per se, but they do collect massive volumes of personal data and, in cases such as PRISM, allow law enforcement to tap into their servers. Once law enforcement agencies get hold of data collected by companies, such as Facebook, they then use data mining software - equipped by various surveillance technology companies - to process and mine the data. And how do companies, like Google and Facebook, make money off our personal data? By selling it to big buyers, such as law enforcement agencies.
So while Facebook and all the ‘Facebooks’ of the world may not profit from surveillance per se, they do profit from collecting our personal data and selling it to third parties, which include law enforcement agencies. And David Lyon argues that surveillance involves the collection of personal data - which corporations, like Facebook, do - for the purpose of influencing and managing individuals. While this last point can probably be widely debated on, it is clear that corporations share their collected data with third parties, which ultimately leads to the influence or managing of individuals - directly or indirectly. In other words, the collection of personal data, in combination with its disclosure to third parties, is surveillance. So when we think about companies, like Google or Facebook, we should not just think of businesses interested in their profit - but also of spying agencies. After all, “if the product is free, you are the product”.
Now if we look at online corporations more closely, we can probably identify three categories:
1. Websites through which we buy products and hand over our personal details - e.g. Amazon
2. Websites through which we use services and hand over our personal details - e.g. flight ticket
3. Websites through which we communicate and hand over our personal details - e.g. Facebook
And why could the above be considered “spying” at all? Because such corporations collect massive volumes of personal data and subsequently:
- Disclose such data to law enforcement agencies
- Allow law enforcement agencies to tap into their servers
- Sell such data to “third parties”
What’s notable about so-called corporate surveillance is that, in all cases, there is a mutual, key element: we consent to the handing over of our personal information. We are not forced to hand over our personal data when buying a book online, booking a flight ticket or using Facebook. Instead, we “choose” to hand over our personal data in exchange for a product or service. Now what significantly differentiates state surveillance to corporate surveillance is the factor of “choice”. While we may choose to hand over our most personal details to large online corporations, such as Google and Facebook, we do not have a choice when the government monitors our communications, collects and stores our personal data.
State Surveillance vs. Corporate Surveillance
Both Indian law enforcement agencies and corporations collect massive volumes of personal data. In fact, it is probably noteworthy to mention that Facebook, in particular, collects 20 times more data per day than the NSA in total. In addition, Facebook has claimed that it has received more demands from the US government for information about its users than from all other countries combined. In this sense, the corporate collection of personal data can potentially be more harmful than government surveillance, especially when law enforcement agencies are tapping into the servers of companies like Facebook. After all, the Indian government and all other governments would have very little data to analyse if it weren’t for such corporations.
Surveillance is not just about “spying” or about “watching people” - it’s about much much more. Observing people’s behaviour only really becomes harmful when the data observed is collected, retained, analysed, shared and disclosed to unauthorised third parties. In other words, surveillance is meaningful to examine because it involves the analysis of data, which in turn involves pattern matching and profiling, which can potentially have actual, real-world implications - good or bad. But such analysis cannot be possible without having access to large volumes of data - most of which belong to large corporations, like Facebook. The question, though, is: How do corporations collect such large volumes of personal data, which they subsequently share with law enforcement agencies? Simple: Because we “choose” to hand over our data!
Three years ago, when I was doing research on young people’s perspective of Facebook, all of the interviewees replied that they feel that they are in control of their personal data, because they “choose” what they share online. While this may appear to be a valid point, the “choice” factor can widely be debated on. There are many reasons why people “choose” to hand over their personal data, whether to buy a product, use a service, to communicate with peers or because they feel socially pressured into using social networking sites. Nonetheless, it all really comes down to one main reason: convenience. Today, in most cases, the reason why we hand over our personal data online in exchange for products or services is because it is simply more convenient to do so. And while that is understandable, at the same time we are exposing our data (and ultimately our lives) in the name of convenience.
The irony in all of this is that, while many people reacted to Snowden’s revelations on NSA dragnet surveillance, most of these people probably have profiles on Facebook. Secret, warrantless government surveillance is undeniably intrusive, but in the end of the day, our profiles on Facebook - and on all the ‘Facebooks’ of the world - is what enabled it to begin with. In other words, if we didn’t choose to give up our personal data - especially without really knowing how it would be handled - large databases would not exist and the NSA - and all the ‘NSAs’ of the world - would have had a harder time gathering and analysing data.
In short, the main difference between state and corporate surveillance is that the first is imposed in a top-down manner by authorities, while the second is a result of our “choice” to give up our data. While many may argue that it’s worse to have control imposed on you, I strongly disagree. When control and surveillance are imposed on us in a top-down manner, it’s likely that we will perceive this - sooner or later - as a direct threat to our human rights, which means that it’s likely that we will resist to it at some point. People usually react to what they perceive as a direct threat, whereas they rarely react to what does not directly affect them. For example, one may perceive murder or suicide as a direct threat due the immediateness of its effect, whereas smoking may not be seen as an equally direct threat, because its consequences are indirect and can usually be seen in the long term. It’s somehow like that with surveillance.
University students have protested on the streets against the installation of CCTV cameras, but how many of them have profiles on social networking sites, such as Facebook? People may react to the installation of CCTV cameras, because it may appear as a direct threat to their right to privacy. However, the irony is that the real danger does not necessarily lie within some CCTV cameras, but rather within the profile of each person on a major commercial social networking site. At very best, a CCTV camera will capture some images of us and through that, track our location and possibly our acquaintances. What type of data is captured through a simple, “harmless” Facebook profile? The following probably only includes a tiny percentage of what is actually captured:
- Personal photos
- Biometrics (possibly through photos)
- Family members
- Friends and acquaintances
- Habits, hobbies and interests
- Location (through IP address)
- Places visited
- Economic standing (based on pictures, comments, etc.)
- Educational background
- Ideas and opinions (which may be political, religious, etc.)
- Activities
- Affiliations
The above list could potentially go on and on, probably depending on how much - or what type - of data is disclosed by the individual. The interesting element to this is that we can never really know how much data we are disclosing, even if we think we control it. While an individual may argue that he/she chooses to disclose an x amount of data, while retaining the rest, that individual may actually be disclosing a 10x amount of data. This may be the case because usually every bit of data hides lots of other bits of data, that we may not be aware of. It all really comes down to who is looking at our data, when and why.
For example, (fictional) Priya may choose to share on her Facebook profile (through photos, comments, or any other type of data) that she is female, Indian, a Harvard graduate and that her favourite book is “Anarchism and other Essays” by Emma Goldman. At first glance, nothing appears to be “wrong” with what Priya is revealing and in fact, she appears to care about her privacy by not revealing “the most intimate details” of her life. Moreover, one could argue that there is absolutely nothing “incriminating” about her data and that, on the contrary, it just reflects that she is a “shiny star” from Harvard. However, I am not sure if a data analyst would be restricted to this data and if data analysis would show the same “sparkly” image.
In theory, the fact that Priya is an Indian who attended Harvard reveals another bit of information, that Priya did not choose to share: her economic standing. Given that the majority of Indians live below the line of poverty, there is a big probability that Priya belongs to India’s middle class - if not elite. Priya may not have intentionally shared this information, but it was indirectly revealed through the bits of data that she did reveal: female Indian and Harvard graduate. And while there may not be anything “incriminating” about the fact that she has a good economic standing, in India this usually means that there’s also some strong political affiliation. That brings us to her other bit of information, that her favourite author is a feminist, anarchist. While that may be viewed as indifferent information, it may be crucial depending on the specific political actors in the country she’s in and on the general political situation. If a data analyst were to map the data that Priya chose to share, along with all her friends and acquaintances that she inevitably has through Facebook, that data analyst could probably tell a story about her. And the concerning part is that that story may or may not be true. But that doesn’t really matter.
Today, governments don’t judge us and take decisions based on our version of our data, but based on what our data says about us. And perhaps, under certain political, social and economic circumstances, our “harmless” data could be more incriminating than what we think. While an individual may express strong political views within a democratic regime, if that political system were to change in the future and to become authoritarian, that individual would possibly be suspicious in the eyes of the government - to say the least. This is where data retention plays a significant role.
Most companies retain data indefinitely or for a long period of time, which means that future, potentially less-democratic governments may have access to it. And the worst part is that we can never really know what data is being held about us, because within data analysis, every bit of data may potentially entails various other bits of data that we are not even aware of. So, when we “choose” to hand over our data, we don’t necessarily know what or how much we are choosing to disclose. Thus, this is why I agree with Bruce Schneier’s argument that people have an illusionary sense of control over their personal data.
Social network analysis software is specifically designed to mine huge volumes of data that is collected through social networking sites, such as Facebook. Such software is specifically designed to profile individuals, to create “trees of communication” around them and to match patterns. In other words, this software tells a story about each and every one of us, based on our activities, interests, acquaintances, and all other data. And as mentioned before, such a story may or may not be true.
In data mining, behavioural statistics are being used to analyse our data and to predict how we are likely to behave. When applied to national databases, this may potentially amount to predicting how masses or groups within the public are likely to behave and to subsequently control them. If a data analyst can predict an individual’s future behaviour - with some probability - based on that individuals’ data, the same could potentially occur on a mass, public level. As such, the danger within surveillance - especially corporate surveillance through which we voluntarily disclose massive amounts of data about ourselves - is that it appears to come down to public control.
According to security expert Bruce Schneier, data today is a byproduct of the Information Society. Unlike an Orwellian totalitarian state where surveillance is imposed in a top-down manner, surveillance today appears to widely exist because we indirectly choose and enable it (by handing over our data to online companies), rather than it being imposed on us in a solely top-down manner. However, contemporary surveillance may potentially be far worse than that described in Orwell’s “1984”, because surveillance is publicly perceived to be an indirect threat - if considered to be a threat at all. It is more likely that people will resist a direct threat, than an indirect threat, which means that the possibility of mass violations of human rights as a result of surveillance is real.
Hannah Arendt argued that a main prerequisite and component of totalitarian power is support by the masses. Today, surveillance appears to be socially integrated within societies which indicates that contemporary power fueled by surveillance has mass support. While the argument that surveillance is being socially integrated can potentially be widely debated on and requires an entire in depth research of its own, few simple facts might be adequate to prove it at this stage. Firstly, CCTV cameras are installed in most countries, yet there has been very little resistance - on the contrary, there appears to be a type of universal acceptance on the grounds of security. Secondly, different types of spy products exist in the market - such as Spy Coca Cola cans - which can be purchased by anyone online. Thirdly, countries all over the world carry out controversial surveillance schemes - such as the Central Monitoring System in India - yet public resistance to such projects is limited. And while one may argue that the above cases don’t necessarily prove that surveillance is being socially integrated, it would be interesting to look at a fourth fact: most people who have Internet access choose to share their personal data through the use of social networking sites.
Reality shows, such as Big Brother, which broadcast the surveillance of people’s lives and present it as a form of entertainment - when actually, I think it should be worrisome - appear to enable the social integration of surveillance. The very fact that we all probably - or, hopefully - know that Facebook can share our personal data with unauthorised third parties and - now, after the Snowden revelations - that governments can tap into Facebook’s servers, should be enough to convince us to delete our profiles. Yet, why do we still all have Facebook profiles? Perhaps because surveillance is socially integrated and perhaps because it is just convenient to be on Facebook. But that doesn’t change the fact that surveillance can potentially be a threat to our human rights. It just means that we perceive surveillance as an indirect threat and that we are unlikely to react to it.
In the long term, what does this mean? Well, it seems like we will probably be more acceptive towards more authoritarian power, that we will be used to the idea of censoring our own thoughts and actions (in the fear of getting caught by the CCTV camera on the street or the spyware which may or may not be implanted in our laptop) and that ultimately, we will be less politically active and more reluctant to challenge the authority.
What’s particularly interesting though about surveillance today is that it is fueled and enabled through our freedom of speech and general Internet freedom. If we didn’t have any Internet freedom - or as much as we do - we would have disclosed less personal data and thus surveillance would probably have been more restricted. The more Internet freedom we have, the more personal data we will disclose on Facebook - and on all the ‘Facebooks’ of the world - and the more data will potentially be available to mine, analyse, share and generally incorporate in the surveillance regime. So in this sense, Internet freedom appears to be a type of prerequisite of surveillance, as contradictory and ironic as it may seem. No wonder why the Chinese government has gone the extra mile in creating the Chinese versions of Facebook and Twitter - it’s probably no coincidence.
While we may blame governments for establishing surveillance schemes, ISP and TSP operators for complying with governments’ license agreements which often mandate that they create backdoors for spying on us and security companies for creating the surveillance gear in the first place, in the end of the day, we are all equally a part of this mess. If we didn’t choose to hand over our personal data to begin with, none of the above would have been possible.
The real danger in the Digital Age is not necessarily surveillance per se, but our choice to voluntarily disclose our personal data.
Programme Booklet
 Programme Booklet_small res-1.pdf
—
PDF document,
1473 kB (1508988 bytes)
Programme Booklet_small res-1.pdf
—
PDF document,
1473 kB (1508988 bytes)
CV Booklet
 CV Booklet_small res-1.pdf
—
PDF document,
1796 kB (1840125 bytes)
CV Booklet_small res-1.pdf
—
PDF document,
1796 kB (1840125 bytes)
Consilience 2013 Report
 Consilience 2013- Recommendatory Report and Conference Proceedings.pdf
—
PDF document,
915 kB (937019 bytes)
Consilience 2013- Recommendatory Report and Conference Proceedings.pdf
—
PDF document,
915 kB (937019 bytes)
CIS Supports the UN Resolution on “The Right to Privacy in the Digital age”.
On November 26, 2013, the United Nations adopted a non-binding resolution on The Right to Privacy in the Digital Age. The resolution was drafted by Brazil and Germany and expressed concern over the negative impact of surveillance and interception on the exercise of human rights. The resolution was controversial as countries such as the US, the UK, and Canada opposed language that spoke to the right to privacy extending equally to citizens and non-citizens of a country. The resolution welcomed the report of the Special Rapporteur on the Promotion and Protection of the Right to Freedom of Opinion and Expression that examined the implications of surveillance of communications on the human rights of privacy and freedom of expression.
The resolution made a number of important statements that India, as a member of the United Nations, and as a country in the process of implementing a number of surveillance projects, like the Central Monitoring System, should take cognizance of, including in short:
- Privacy is a human right: Privacy is a human right according to which no one should be subjected to arbitrary or unlawful interference with his or her privacy, family, home, or correspondence.
- Privacy is integral to the right to free expression: an integral component in recognizing the right to freedom of expression.
- Unlawful and arbitrary surveillance violates the right to privacy and freedom of expression: Unlawful and/or arbitrary surveillance, interception, and collection of personal data are intrusive acts that violate the right to privacy and freedom of expression.
- Exceptions to privacy and freedom of expression should be in compliance with human rights law: Public security is a potential exception justifying collection and protection of information, but States must ensure that this is done fully in compliance with international human rights law.
- Mass surveillance may have negative implications for human rights: Domestic and extraterritorial surveillance, interception, and the collection of personal data on a mass scale may have a negative impact on individual human rights.
- Equal protection for online and offline privacy: The right to privacy must be equally protected online and offline.
The resolution further called upon states to:
- Respect and protect the right to privacy, particularly in the context of digital communications.
- To ensure that relevant legislation is in compliance with international human rights law
- To review national procedures and practices around surveillance to ensure full and effective implementation of obligations under international human rights law.
- To establish and maintain effective domestic oversight mechanisms around domestic surveillance capable of ensuring transparency and accountability.
The resolution finally calls upon the UN High Commissioner for Human Rights to present a report with views and recommendations on the protection and promotion of the right to privacy in the context of surveillance to the Human Rights Council at its twenty-seventh session and to the General Assembly at its sixty-ninth session and decides to examine “Human rights questions, including alternative approaches for improving the effective enjoyment of human rights and fundamental freedoms”.
The UN Resolution on the Right to Privacy in the Digital Age is a welcome step towards an international recognition of privacy as a human right in the context of communications and extra territorial surveillance. The Centre for Internet and Society encourages the Government of India to, as called upon in the Resolution, to review national procedures and practices around surveillance to ensure full and effective implementation of obligations under international human rights law.
Prior to the UN Resolution on “The Right to Privacy in the Digital Age”, a group of international NGO’s developed the Necessary and Proportionate principles that seek to form a backbone for a response to mass surveillance and provide a framework for governments to assess if domestic surveillance regimes are in compliance with international Human Rights Law. CIS has contributed to the process of developing these principles. The principles include legality, legitimate aim, necessity, adequacy, proportionality, competent judicial authority, due process, user notification, transparency, public oversight, integrity of communications and systems, safeguards for international cooperation, and safeguards against illegitimate access. A petition to sign onto the principles and demand an end to mass surveillance is currently underway.
Both the Government of India and public of India should take into consideration the UN Resolution and the necessary and proportionate principles to reflect on how India’s surveillance regime and practices can be brought in line with international human rights law and understand where the balance is drawn for necessary and proportionate surveillance, specific to the Indian context.
Open Secrets
Dr. Nishant Shah's article was originally published in the Indian Express on October 27.
If you are a part of any social networking site, then you know that privacy is something to be concerned about. We put out an incredible amount of personal data on our social networks. Pictures with family and friends, intimate details about our ongoing drama with the people around us, medical histories, and our spur-of-the-moment thoughts of what inspires, peeves or aggravates us. In all this, the more savvy use filters and group settings which give them some semblance of control about who has access to this information and what can be done with it.
But it is now a given that in the world of the worldwide web, privacy is more or less a thing of the past. Data transmits. Information flows. What you share with one person immediately gets shared with thousands. Even though you might make your stuff accessible to a handful of people, the social networks work through a "friend-of-a-friend effect", where others in your networks use, like, share and spread your information around so that there is an almost unimaginable audience to the private drama of our lives. Which is why there is a need for a growing conversation about what being private in the world of big data means.
Privacy is about having control over the data and some ownership about who can use it and for what purpose. Interface designs and filters that allow limited access help this process. The legal structures are catching up with regulations that control what individuals, entities, governments and corporations can do with the data we provide. However, most people think of privacy as a private matter. Just look at last month's conversations around Facebook's new privacy policies, which no longer allow you to hide. If you are on Facebook, people can find you using all kinds of parameters — meta data — other than just your name. They might find you through hobbies, pages you like, schools you have studied in, etc. This can be scary because it means that based on particular activities, people can profile and follow you. Especially for people in precarious communities — the young adults, queer people who might not be ready to be out of the closet, women who already face increased misogyny and hostility online. This means they are officially entering a stalkers' paradise.
While those concerns need to be addressed, there is something that seems to be missing from the debate. Almost all of these privacy alarms are about what people can do to people. That we need to protect ourselves from people, when we are in public — digital or otherwise. We are reminded that the world is filled with predators, crackers and scamsters, who can prey on our personal data and create physical, emotional, social and financial havoc. But this is the world we already know. We live in a universe filled with perils and we have learned and coped with the fact that we navigate through dangerous spaces, times and people all the time. The digital is no different than the physical when it comes to the possible perils that we live in, though digital might facilitate some kinds of behaviour and make data-stalking easier.
What is different with the individualised, just-for-you crafted world of the social web is that there are things which are not human, which are interacting with you in unprecedented ways. Make a list of the top five people you interact with on Facebook. And you will be wrong. Because the thing that you interact with the most on Facebook, is Facebook. Look at the amount of chatter it creates — How are you feeling today?; Your friend has updated their status; Somebody liked your comment… the list goes on. In fact, much as we would like to imagine a world that revolves around us, we know that there are a very few people who have the energy and resources to keep track of everything we do. However, no matter how boring your status message or how pedestrian your activity, deep down in a server somewhere, an artificial algorithm is keeping track of everything that you do. Facebook is always listening, and watching, and creating a profile of you. People might forget, skip, miss or move on, but Facebook will listen, and remember long after you have forgotten.
If this is indeed the case, we need to think of privacy in different ways — not only as something that happens between people, but between people and other entities like corporations. The next time there is a change in the policy that makes us more accessible to others, we should pay attention. But what we need to be more concerned about are the private corporations, data miners and information gatherers, who make themselves invisible and collect our personal data as we get into the habit of talking to platforms, gadgets and technologies.
I Just Pinged to Say Hello
Dr. Nishant Shah's article was published in the Indian Express on November 24, 2013.
I am making a list of all the platforms that I use to connect with the large networks that I belong to. Here goes: I use Yahoo! Messenger to talk to my friends in east Asia. Most of my work meetings happen on Skype and Google Hangout. A lot of friendly chatter fills up my Facebook Messenger. Twitter is always available for a little back-chat and bitching. On the phone, I use Viber to make VoIP calls and WhatsApp is the space for unending conversations spread across days. And these are just the spaces for real-time conversation. Across all these platforms, something strange is happening. As I stay connected all the time, I am facing a phenomenon where we have run out of things to say, but not the desire to talk.
I had these three conversations today on three different instant-messaging platforms:
Person 1 (on WhatsApp): Hi.
Me: Hey, good to hear from you. How are you doing?
Person 1: Good.
Me (after considerable silence): So what's up?
Person 1: Nothing.
End of conversation.
Person 2 (On an incoming video call on Skype): Hey, you there?
Me: Yeah. What time is it for you right now?
Person 2: It is 10 at night.
Me: Oh! That is late. How come you are calling me so late?
Person 2: Oh, I saw you online.
Me: Ok….. *eyes raised in question mark*
Person 2: So, that's it. I am going to sleep soon.
Me: Ok…. Er…goodnight.
Person2: Goodnight.
We hang up.
Person 3 (pinging me on Facebook): Hey, you are in the US right now?
Me: Yes. I am attending a conference here.
Person 3: Cool!
Me: Umm… yeah, it is.
Person 3: emoticon of a Facebook 'like'. Have fun. Bye.
Initially I was irritated at the futility of these pings that are bewildering in their lack of content. I dismissed it as one of those things, but I realise that there is a pattern here. Our lives are so particularly open and documented, such minute details of what we do, where we are and who we are with, is now available for the rest of the world to consume, making most of the conversations seeking information, redundant. If you know me on my social media networks, you already know most of the basic things that you would want to know about me. And it goes without saying that no matter how close and connected we are, we are not necessarily in a state where we want to talk all the time. The more distributed our lives are, the more diminished is the need for personal communication.
And yet, the habit or the urge to ping, buzz, DM or chat has not caught up with this interaction deficit. So, we still seem to reach out, using a variety of platforms just to say hello, even when there is nothing to say. I call this the 'Always On' syndrome. We live in a world where being online all the time has become a ubiquitous reality. Even when we are asleep, or busy in a meeting, or just mentally disconnected from the online spaces, our avatars are still awake. They interact with others. And when they feel too lonely, they reach out and send that empty ping — just to confirm that they are not alone. That on the other side of the glowing screen is somebody else who is going to connect back, and to reassure you that we are all together in this state of being alone.
This empty ping has now become a signifier, loaded with meaning. The need for human connection has been distributed, but it does not compensate our need for one-on-one contact. In the early days of the cell phone, when incoming calls were still being charged, the missed call, without any content, was a code between friends and lovers. It had messages about where to meet, when to meet, or sometimes, just that you were missing somebody. The empty ping is the latest avatar of the missed call — in a world where we are always online but not always connected, when we are constantly together, but also spatially and emotionally alone, the ping remains that human touch in the digital space that reassures us that on the other side of that seductive interface and the buzzing gadget, is somebody we can say hello to.
Chances and Risks of Social Participation
 programme_participation_woOSHWuNaMiuRBGHMPwNSHIIG2.pdf
—
PDF document,
75 kB (77702 bytes)
programme_participation_woOSHWuNaMiuRBGHMPwNSHIIG2.pdf
—
PDF document,
75 kB (77702 bytes)
Misuse of Surveillance Powers in India (Case 1)
Case 1: Unlawful Phone-tapping in Himachal Pradesh
In December 2012, the government changed in Himachal Pradesh. The Bharatiya Janata Party (BJP) went out of power, and the Indian National Congress (INC) came into power. One of the first things that Chief Minister Virbhadra Singh did, within hours of taking his oath as Chief Minister on December 25, 2012, was to get a Special Investigation Team (SIT) to investigate phone tapping during the BJP government’s tenure.
On December 25th and 26th, 12 hard disk drives were seized from the offices of the Crime Investigation Department (CID) and the Vigilance Department (which is supposed to be an oversight mechanism over the rest of the police). These hard disks showed that 13711 phone numbers were targetted and hundreds of thousands of phone conversations were recorded. These included conversations of prominent leaders “mainly of” the INC but also from the BJP, including three former cabinet ministers and close relatives of multiple chief ministers, a journalist, and many senior police officials, including the Director General of Police.
Violations of the Law
While the law required the state’s Home Secretary to grant permission for each person that was being tapped, the Home Secretary had legitimately only granted permission in 342 cases. This leaves over a thousand cases where phones were tapped illegally, in direct violation of the law. The oversight mechanism provided in the law, namely the Review Committee under Rule 419A of the Indian Telegraph Rules, was utterly powerless to check this. Indeed, the internal checks for the police, namely the Vigilance Department, also seems to have failed spectacularly.
Every private telecom company cooperated in this unlawful surveillance, even though the people who were conducting it did so without proper legal authority. Clearly we need to revise our interception rules to ensure that these telecom companies do not cooperate unless they are served with an order digitally signed by the Home Secretary.
While all interception recordings are required to be destroyed within 6 months as per Rule 419A of the Indian Telegraph Rules, that rule was also evidently ignored and conversations going back to 2009 were being stored.
Concluding Concerns
What should concern us is not merely that such a large number of politicians/police officers were tapped, but that no criminal charges were brought about on the basis of these phone taps, indicating that much of it was being used for political purposes.
What should concern us is that the requirement under Section 5 of the Indian Telegraph Act, which covers phone taps, of the existence of a “public emergency” or endangerment of “public safety”, which is a prerequisite of phone taps as per the law and as emphasised by the Supreme Court in 1996 in the PUCL judgment, were blatantly ignored.
What should concern us is that it took a change in government to actually uncover this sordid tale.
1385 according to a Hindustan Times report [1]: http://indiatoday.intoday.in/story/himachal-pradesh-police-registers-first-fir-in-phone-tapping-scandal/1/285698.html↩
A Zee News report states 34 while it’s 171 according to a Mail Today report↩
Sub Tracks
 Sub Tracks for Discussion-1.pdf
—
PDF document,
327 kB (334958 bytes)
Sub Tracks for Discussion-1.pdf
—
PDF document,
327 kB (334958 bytes)
Consilience Speakers Profile
 Consilience 2013-14 Speakers Profiles-1.pdf
—
PDF document,
451 kB (462811 bytes)
Consilience 2013-14 Speakers Profiles-1.pdf
—
PDF document,
451 kB (462811 bytes)
Brochures from Expos on Smart Cards, e-Security, RFID & Biometrics in India
In Pragati Maidan, New Delhi, many companies from India and abroad gathered to exhibit their products at the following expos which were organised by Electronics Today (India's first electronic exhibition organiser) on 16-18 October 2013:
- SmartCards Expo 2013
- e-Security Expo 2013
- RFID Expo 2013
- Biometrics Expo 2013
The Centre for Internet and Society (CIS) attended these exhibitions for research purposes and is sharing the publicly available brochures it gathered through the attached zip file. The use of these brochures constitutes Fair Use.
 Brochures.zip
—
ZIP archive,
78400 kB (80282581 bytes)
Brochures.zip
—
ZIP archive,
78400 kB (80282581 bytes)
Big Brother is watching you
The article by Chinmayi Arun was published in the Hindu on January 3, 2014.
The Gujarat telephone tapping controversy is just one of many kinds of abuse that surveillance systems enable. If a relatively primitive surveillance system can be misused so flagrantly despite safeguards that the government claims are adequate, imagine what is to come with the Central Monitoring System (CMS) and Netra in place.
News reports indicate Netra — a “NEtwork TRaffic Analysis system” — will intercept and examine communication over the Internet for keywords like “attack,” “bomb,” “blast” or “kill.” While phone tapping and the CMS monitor specific targets, Netra is vast and indiscriminate. It appears to be the Indian government’s first attempt at mass surveillance rather than surveillance of predetermined targets. It will scan tweets, status updates, emails, chat transcripts and even voice traffic over the Internet (including from platforms like Skype and Google Talk) in addition to scanning blogs and more public parts of the Internet. Whistle-blower Edward Snowden said of mass-surveillance dragnets that “they were never about terrorism: they’re about economic spying, social control, and diplomatic manipulation. They’re about power.”
So far, our jurisprudence has dealt with only targeted surveillance; and even that in a woefully inadequate manner. This article discusses the slow evolution of the right to privacy in India, highlighting the context and manner in which it is protected. It then discusses international jurisprudence to demonstrate how the right to privacy might be protected more effectively.
Privacy and the Constitution
A proposal to include the right to privacy in the Constitution was rejected by the Constituent Assembly with very little debate. Separately, a proposal to give citizens an explicit fundamental right against unreasonable governmental search and seizure was also put before the Constituent Assembly. This proposal was supported by Dr. B.R. Ambedkar. If accepted, it would have included within our Constitution the principles from which the United States derives its protection against state surveillance. However, the proposed amendment was rejected by the Constituent Assembly.
Fortunately, the Supreme Court has gradually been reading the right to privacy into the fundamental rights explicitly listed in the Constitution. After its initial reluctance to affirm the right to privacy in the 1954 case of M.P. Sharma vs. Satish Chandra, the court came around to the view that other rights and liberties guaranteed in the Constitution would be seriously affected if the right to privacy was not protected. In Kharak Singh vs. The State of U.P., the court recognised “the right of the people to be secure in their persons, houses, papers, and effects” and declared that their right against unreasonable searches and seizures was not to be violated. The right to privacy here was conceived around the home, and unauthorised intrusions into homes were seen as interference with the right to personal liberty.
If the Kharak Singh judgment was progressive in its recognition of the right to privacy, it was conservative about the circumstances in which the right applies. The majority of judges held that shadowing a person could not be seen to interfere with that person’s liberty. Dissenting with the majority, Justice Subba Rao maintained that broad surveillance powers put innocent citizens at risk, and that the right to privacy is an integral part of personal liberty. He recognised that when a person is shadowed, her movements will be constricted, and will certainly not be free movements. His dissenting judgment showed remarkable foresight and his reasoning is consistent with what is now a universally acknowledged principle that there is a “chilling effect” on expression and action when people think that they are being watched.
The right to privacy as defined by the Supreme Court now extends beyond government intrusion into private homes. After Govind vs. State of M.P., and Dist. Registrar and Collector of Hyderabad vs. Canara Bank, this right is seen to protect persons and not places. Any inroads into this right for surveillance of communication must be for permissible reasons and according to just, fair and reasonable procedure. State action in violation of this procedure is open to a constitutional challenge.
Our meagre procedural safeguards against phone tapping were introduced in PUCL vs. Union of India (1997) after the Supreme Court was confronted with extensive, undocumented phone tapping by the government. The apex court found itself compelled to lay down what it saw as bare minimum safeguards, consisting mostly of proper record-keeping and internal executive oversight by senior officers such as the home secretary, the cabinet secretary, the law secretary and the telecommunications secretary. These safeguards are of little use since they are opaque and rely solely on members of the executive to review surveillance requests.
Right and safeguards
There is a difference between targeted surveillance in which reasons have to be given for surveillance of particular people, and the mass-surveillance which Netra sets up. The question of mass surveillance and its attendant safeguards has been considered by the European Court of Human Rights in Liberty and Others vs. the United Kingdom. Drawing upon its own past jurisprudence, the European Court insisted on reasonable procedural safeguards. It stated quite clearly that there are significant risks of arbitrariness when executive power is exercised in secret and that the law should be sufficiently clear to give citizens an adequate indication of the circumstances in which interception might take place. Additionally, the extent of discretion conferred and the manner of its exercise must be clear enough to protect individuals from arbitrary interference. The principles laid down by the European Court in relation to phone-tapping also require that the nature of the offences which may give rise to an interception order, the procedure to be followed for examining, using and storing the data obtained, the precautions to be taken when communicating the data to other parties, and the circumstances in which recordings may or must be erased or the tapes destroyed be made clear.
Opaque and ineffective
Our safeguards apply only to targeted surveillance, and require written requests to be provided and reviewed before telephone tapping or Internet interception is carried out. CMS makes the process of tapping more prone to misuse by the state, by making it even more opaque: if the state can intercept communication directly, without making requests to a private telecommunication service provider, then it is one less layer of scrutiny through which the abuse of power can reach the public. There is no one to ask whether the requisite paperwork is in place or to notice a dramatic increase in interception requests.
India has no requirements of transparency whether in the form of disclosing the quantum of interception taking place each year, or in the form of subsequent notification to people whose communication was intercepted. It does not even have external oversight in the form of an independent regulatory body or the judiciary to ensure that no abuse of surveillance systems takes place. Given these structural flaws, the Amit Shah controversy is just the beginning of what is to come. Unfettered mass surveillance does not bode well for democracy.
(Chinmayi Arun is research director, Centre for Communication Governance, National Law University, Delhi, and fellow, Centre for Internet and Society, Bangalore.)
Letter requesting public consultation on position of GoI at WGEC
January 3, 2014
Shri Kapil Sibal,
Honourable Minister for Communication and Information Technology
Ministry of Communication and Information Technology,
Government of India
Subject: Public consultation at the domestic level on the position of Government of India at WGEC
Dear Sir,
We at the Centre for Internet and Society, Bangalore (“CIS”) commend, Government of India’s participation at the Working Group on Enhanced Cooperation (WGEC), working under the aegis of United Nations Commission on Science and Technology and Development (CSTD). The Working Group was set up in pursuance of General Assembly Resolution A/Res/67/195, to identify a shared understanding of enhanced cooperation on public policy issues pertaining to the internet. The WGEC after its first meeting circulated a questionnaire to collect the views and positions of the stakeholders on various aspects of enhanced cooperation. The Government of India responded to the questionnaire and also represented its position at the second meeting of WGEC held in Geneva from November 6-8, 2013. We would like the Government to take cognizance of representations from concerned stakeholders before finalizing its position.
In this regard, we would like to note, Government of India’s commitment towards multi-stakeholder approach in formulation of public policy pertaining to the internet. At the Internet Governance Forum, 2012 held in Baku, the Honourable Minister for Communications and Information Technology noted that the “issues of public policy related to the internet have to be dealt with, by adopting a multi-stakeholder, democratic and transparent approach”. Furthermore, the Government of India’s stand at the World Conference on International Telecommunications, 2012 in Dubai supported and recognized the multi-stakeholder nature of the internet.
However, it seems that the Government has digressed from its previous stand on internet governance whereas it fell short of having a multi-stakeholder public consultation on India’s position on enhanced cooperation at the WGEC. We earnestly urge you to hold domestic public consultation before the next WGEC meeting.
Thank you.
Sincerely,
Snehashish Ghosh,
Policy Associate,
Centre for Internet and Society, Bangalore
Copied to: Dr. Ajay Kumar, Joint Secretary, DietY, MOCIT and Shri. J. Satyanarayana, Secretary, DietY, MOCIT
Letter on WGEC
 Letter on WGEC.pdf
—
PDF document,
315 kB (323404 bytes)
Letter on WGEC.pdf
—
PDF document,
315 kB (323404 bytes)
Internet Monitor
 SSRN-id2366840.pdf
—
PDF document,
7223 kB (7396414 bytes)
SSRN-id2366840.pdf
—
PDF document,
7223 kB (7396414 bytes)
India's Identity Crisis
India’s Unique Identity (UID) project is already the world’s largest biometrics identity program, and it is still growing. Almost 530 million people have been registered in the project database, which collects all ten fingerprints, iris scans of both eyes, a photograph, and demographic information for each registrant. Supporters of the project tout the UID as a societal game changer. The extensive biometric information collected, they argue, will establish the uniqueness of each individual, eliminate fraud, and provide the identity infrastructure needed to develop solutions for a range of problems. Despite these potential benefits, however, critical concerns remain about the UID’s legal and physical architecture as well as about unforeseen risks associated with the linking and analysis of personal data.
The most basic concerns regarding the UID project stem from the fact that biometric technologies have never been tested on such a large population. As a result, well-founded concerns exist around scalability, false acceptance and rejection rates, and the project’s core premise that biometrics can uniquely and unambiguously identify people in a foolproof manner. Some of these concerns are based on technical issues—collecting fingerprints and iris scans “in the field,” for instance, can be complicated when a registrant’s fingerprints are eroded by manual labor or her irises are affected by malnutrition and cataracts. Other concerns relate to the project’s federated implementation architecture, which, by outsourcing collection to a massive group of private and public registrars and operators, increases the chance for data breaches, error, and fraud.
Perhaps even more vexing are concerns regarding how the UID, which promises financial inclusion (by reducing the identification barriers to opening bank accounts, for example), might in fact lead to new types of exclusion for already marginalized groups. Members of the LGBT community, for instance, question whether the inclusion of the transgender category within the UID scheme is a laudable attempt at inclusion, or a new means of listing and targeting members of their community for exclusion. More fundamentally, as more and more services and benefits are linked to the UID, the project threatens to exclude all those who cannot or will not participate in the scheme due to logistical failures or philosophical objections.
It is worth noting that the UID is not the only large data project in India. A slew of “Big Brother” projects exist: the Centralised Monitoring System (CMS), the Telephone Call Interception System (TCIS), the National Population Register (NPR), the Crime and Criminal Tracking Network and Systems (CCTNS), and the National Intelligence Grid (NATGRID), which is working to aggregate up to 21 different databases relating to tax, rail and air travel, credit card transactions, immigration, and other domains. The UID is intended to serve as a common identifier across these databases, creating a massive surveillance state. It also facilitates an ecosystem where access to goods and services, from government subsidies to drivers’ licenses to mobile phones to cooking gas, increasingly requires biometric authentication.
The UID project was originally vaunted as voluntary, but the inexorable slippery slope toward compulsory participation has triggered a series of lawsuits challenging the legality of forced enrollment and the constitutionality of the entire project. Most recently, in September 2013, India’s federal Supreme Court affirmed by way of an interim decision that the UID was not mandatory, that not possessing a UID should not disadvantage anybody, and that citizenship should be ascertained as a criteria for registering in order to ensure that UIDs are not issued to illegal immigrants. This last stipulation is particularly thorny given that the Unique Identification Authority of India (UIDAI, the body in charge of the UID project) has consistently distanced the UID from questions of citizenship under the justification that it is a matter beyond their remit (i.e., the UID is open to residents, and is not linked to citizenship). The government moved quickly to urge a modification of the order, but the Supreme Court declined to do so and will instead release its final decision after it reviews a batch of petitions from activists and others. The UIDAI approached the court, arguing that not making the UID mandatory has serious consequences for welfare schemes, but the court recently ordered the federal government, the Reserve Bank of India, and the Election Commission to delink the LPG cooking gas scheme from the UID. This is a considerable setback for the project, given that this was one of the most hyped linkages for the UID. It remains to be seen whether the court will similarly halt other attempts to make the UID mandatory.
In the meantime, the UID project is effectively being implemented in a legal vacuum without support from the Supreme Court or Parliament. The Cabinet is seeking to rectify this and has cleared a bill that would finally provide legal backing for the UID program—its previous attempt was rejected by the Standing Committee on Finance in 2010. This bill is scheduled to come up for debate during the winter session of Parliament. The bill’s progress, along with the final decision of the Supreme Court, will have far reaching consequences for the UID project’s implementation and longevity, as well as for the relationship between India’s citizens and the state.
If fully implemented, the UID system will fundamentally alter the way in which citizens interact with the government by creating a centrally controlled, technology-based standard that mediates access to social services and benefits, financial systems, telecommunications, and governance. It will undoubtedly also have implications for how citizens relate to private sector entities, on which the UID rests and which have their own vested interests in the data. The success or failure of the UID represents a critical moment for India. Whatever course the country takes, its decision to travel further toward or turn away from becoming a “database nation” will have implications for democracy, free speech, and economic justice within its own borders and also in the many neighboring countries that look to it as a technological standard bearer.
The Indian government seems to envision “big data” as a panacea for fraud, corruption, and abuse, but it has given little attention to understanding and addressing the fraud, corruption, and abuse that massive databases can themselves engender. The government’s actions have yet to demonstrate an appreciation for the fact that the matrix of identity and surveillance schemes it has implemented can create a privacy-invading technology layer that is not only a barrier to online activity but also to social participation writ large.
The lack of identification documents for a large portion of the Indian population does need to be addressed. Whether the UID project is the best means to do this—whether it has the right architecture and design, whether it can succeed without an overhaul of several other failures of governmental institutions, and whether fixing the identity piece alone causes more harm than good—should be the subject of intense debate and scrutiny. Only through rigorous threat modeling and analysis of the risks arising out of this burgeoning “data industrial complex” can steps be taken to stem the potential repercussions of the project not just for identity management, fraud, corruption, distributive justice, and welfare generally, but also for autonomy, openness, and democracy.
Click to download the article published in the annual report of Berkman's Center for Internet and Society (PDF 7223 Kb)
Surveillance and the Indian Constitution - Part 1: Foundations
Note: This was originally posted on the Indian Constitutional Law and Philosophy blog.
On previous occasions, we have discussed the ongoing litigation in ACLU v. Clapper in the United States, a challenge to the constitutionality of the National Security Agency’s (NSA) bulk surveillance program. Recall that a short while after the initial Edward Snowden disclosures, The Hindu revealed the extent of domestic surveillance in India, under the aegis of the Central Monitoring System (CMS). The CMS (and what it does) is excellently summarized here. To put thing starkly and briefly:
“With the C.M.S., the government will get centralized access to all communications metadata and content traversing through all telecom networks in India. This means that the government can listen to all your calls, track a mobile phone and its user’s location, read all your text messages, personal e-mails and chat conversations. It can also see all your Google searches, Web site visits, usernames and passwords if your communications aren’t encrypted.”
The CMS is not sanctioned by parliamentary legislation. It also raises serious privacy concerns. In order to understand the constitutional implications, therefore, we need to investigate Indian privacy jurisprudence. In a series of posts, we plan to discuss that.
Privacy is not mentioned in the Constitution. It plays no part in the Constituent Assembly Debates. The place of the right – if it exists – must therefore be located within the structure of the Constitution, as fleshed out by judicial decisions. The first case to address the issue was M. P. Sharma v. Satish Chandra, in 1954. In that case, the Court upheld search and seizure in the following terms:
"A power of search and seizure is in any system of jurisprudence an overriding power of the State for the protection of social security and that power is necessarily regulated by law. When the Constitution makers have thought fit not to subject such regulation to Constitutional limitations by recognition of a fundamental right to privacy, analogous to the American Fourth Amendment, we have no justification to import it, into a totally different fundamental right. by some process of strained construction."
The right in question was 19(1)(f) – the right to property. Notice here that the Court did not reject a right to privacy altogether – it only rejected it in the context of searches and seizures for documents, the specific prohibition of the American Fourth Amendment (that has no analogue in India). This specific position, however, would not last too long, and was undermined by the very next case to consider this question, Kharak Singh.
In Kharak Singh v. State of UP, the UP Police Regulations conferred surveillance power upon certain “history sheeters” – that is, those charged (though not necessarily convicted) of a crime. These surveillance powers included secret picketing of the suspect’s house, domiciliary visits at night, enquiries into his habits and associations, and reporting and verifying his movements. These were challenged on Article 19(1)(d) (freedom of movement) and Article 21 (personal liberty) grounds. It is the second ground that particularly concerns us.
As a preliminary matter, we may observe that the Regulations in question were administrative – that is, they did not constitute a “law”, passed by the legislature. This automatically ruled out a 19(2) – 19(6) defence, and a 21 “procedure established by law” defence – which were only applicable when the State made a law. The reason for this is obvious: fundamental rights are extremely important. If one is to limit them, then that judgment must be made by a competent legislature, acting through the proper, deliberative channels of lawmaking – and not by mere administrative or executive action. Consequently – and this is quite apart from the question of administrative/executive competence - if the Police Regulations were found to violate Article 19 or Article 21, that made them ipso facto void, without the exceptions kicking in. (Paragraph 5)
It is also important to note one other thing: as a defence, it was expressly argued by the State that the police action was reasonable and in the interests of maintaining public order precisely because it was “directed only against those who were on proper grounds suspected to be of proved anti-social habits and tendencies and on whom it was necessary to impose some restraints for the protection of society.” The Court agreed, observing that this would have “an overwhelming and even decisive weight in establishing that the classification was rational and that the restrictions were reasonable and designed to preserve public order by suitable preventive action” – if there had been a law in the first place, which there wasn’t. Thus, this issue itself was hypothetical, but what is crucial to note is that the State argued – and the Court endorsed – the basic idea that what makes surveillance reasonable under Article 19 is the very fact that it is targeted – targeted at individuals who are specifically suspected of being a threat to society because of a history of criminality.
Let us now move to the merits. The Court upheld secret picketing on the ground that it could not affect the petitioner’s freedom of movement since it was, well secret – and what you don’t know, apparently, cannot hurt you. What the Court found fault with was the intrusion into the petitioner’s dwelling, and knocking at his door late at night to wake him up. The finding required the Court to interpret the meaning of the term “personal liberty” in Article 21. By contrasting the very specific rights listed in Article 21, the Court held that:
“Is then the word “personal liberty” to be construed as excluding from its purview an invasion on the part of the police of the sanctity of a man’s home and an intrusion into his personal security and his right to sleep which is the normal comfort and a dire necessity for human existence even as an animal? It might not be inappropriate to refer here to the words of the preamble to the Constitution that it is designed to “assure the dignity of the individual” and therefore of those cherished human value as the means of ensuring his full development and evolution. We are referring to these objectives of the framers merely to draw attention to the concepts underlying the constitution which would point to such vital words as “personal liberty” having to be construed in a reasonable manner and to be attributed that these which would promote and achieve those objectives and by no means to stretch the meaning of the phrase to square with any preconceived notions or doctrinaire constitutional theories.” (Paragraph 16)
A few important observations need to be made about this paragraph. The first is that it immediately follows the Court’s examination of the American Fifth and Fourteenth Amendments, with their guarantees of “life, liberty and property…” and is, in turn, followed by the Court’s examination of the American Fourth Amendment, which guarantees the protection of a person’s houses, papers, effects etc from unreasonable searches and seizures. The Court’s engagement with the Fourth Amendment is ambiguous. It admits that “our Constitution contains no like guarantee…”, but holds that nonetheless “these extracts [from the 1949 case, Wolf v Colorado] would show that an unauthorised intrusion into a person’s home and the disturbance caused to him thereby, is as it were the violation of a common law right of a man – an ultimate essential of ordered liberty”, thus tying its own holding in some way to the American Fourth Amendment jurisprudence. But here’s the crucial thing: at this point, American Fourth Amendment jurisprudence was propertarian based – that is, the Fourth Amendment was understood to codify – with added protection – the common law of trespass, whereby a man’s property was held sacrosanct, and not open to be trespassed against. Four years later, in 1967, in Katz, the Supreme Court would shift its own jurisprudence, to holding that the Fourth Amendment protected zones where persons had a “reasonable expectation of privacy”, as opposed to simply protecting listed items of property (homes, papers, effects etc). Kharak Singh was handed down before Katz. Yet the quoted paragraph expressly shows that the Court anticipated Katz, and in expressly grounding the Article 21 personal liberty right within the meaning of dignity, utterly rejected the propertarian-tresspass foundations that it might have had. To use a phrase invoked by later Courts – in this proto-privacy case, the Court already set the tone by holding it to attach to persons, not places.
While effectively finding a right to privacy in the Constitution, the Court expressly declined to frame it that way. In examining police action which involved tracking a person’s location, association and movements, the Court upheld it, holding that “the right of privacy is not a guaranteed right under our Constitution and therefore the attempt to ascertain the movements of an individual which is merely a manner in which privacy is invaded is not an infringement of a fundamental right guaranteed by Part III.”
The “therefore” is crucial. Although not expressly, the Court virtually holds, in terms, that tracking location, association and movements does violate privacy, and only finds that constitutional because there is no guaranteed right to privacy within the Constitution. Yet.
In his partly concurring and partly dissenting opinion, Subba Rao J. went one further, by holding that the idea of privacy was, in fact, contained within the meaning of Article 21: “it is true our Constitution does not expressly declare a right to privacy as a fundamental right, but the said right is an essential ingredient of personal liberty.” Privacy he defined as the right to “be free from restrictions or encroachments on his person, whether those restrictions or encroachments are directly imposed or indirectly brought about by calculated measures.” On this ground, he held all the surveillance measures unconstitutional.
Justice Subba Rao’s opinion also explored a proto-version of the chilling effect. Placing specific attention upon the word “freely” contained within 19(1)(d)’s guarantee of free movment, Justice Subba Rao went specifically against the majority, and observed:
“The freedom of movement in clause (d) therefore must be a movement in a free country, i.e., in a country where he can do whatever he likes, speak to whomsoever he wants, meet people of his own choice without any apprehension, subject of course to the law of social control. The petitioner under the shadow of surveillance is certainly deprived of this freedom. He can move physically, but he cannot do so freely, for all his activities are watched and noted. The shroud of surveillance cast upon him perforce engender inhibitions in him and he cannot act freely as he would like to do. We would, therefore, hold that the entire Regulation 236 offends also Art. 19(1)(d) of the Constitution.”
This early case, therefore, has all the aspects that plague the CMS today. What to do with administrative action that does not have the sanction of law? What role does targeting play in reasonableness – assuming there is a law? What is the philosophical basis for the implicit right to privacy within the meaning of Article 21’s guarantee of personal liberty? And is the chilling effect a valid constitutional concern?
We shall continue with the development of the jurisprudence in the next post.
You can follow Gautam Bhatia on Twitter
Electoral Databases – Privacy and Security Concerns
The recent move by the Election Commission of India (ECI) to tie-up with Google for providing electoral look-up services for citizens and electoral information services has faced heavy criticism on the grounds of data security and privacy.[i] After due consideration, the ECI has decided to drop the plan.[ii]
The plan to partner with Google has led to much apprehension regarding Google gaining access to the database of 790 million voters including, personal information such as age, place of birth and residence. It could have also gained access to cell phone numbers and email addresses had the voter chosen to enroll via the online portal on the ECI website. Although, the plan has been cancelled, it does not necessarily mean that the largest database of citizens of India is safe from any kind of security breach or abuse. In fact, the personal information of each voter in a constituency can be accessed by anyone through the ECI website and the publication of electoral rolls is mandated by the law.
Publication of Electoral Rolls
The electoral roll essentially contains the name of the voter, name of the relationship (son of/wife of, etc.), age, sex, address and the photo identity card number. The main objective of creation and maintenance of electoral rolls and the issue of Electoral Photo Identity Card (EPIC) was to ensure a free and fair election where the voter would have been able to cast his own vote as per his own choice. In other words, the main purpose of the exercise was to curtail bogus voting. This is achieved by cross referencing the EPIC with the electoral roll.
The process of creation and maintenance of electoral rolls is governed by the Registration of Electors Rules, 1960. Rule 22 requires the registration officer to publish the roll with list of amendments at his office for inspection and public information. Furthermore, ECI may direct the registration officer to send two copies of the electoral roll to every political party for which a symbol has exclusively been reserved by the ECI. It can be safely concluded that the electoral roll of a constituency is a public document[iii] given that the roll is published and can be circulated on the direction of the ECI.
With the computational turn, in 1998 the ECI took the decision to digitize the electoral databases. Furthermore, printed electoral rolls and compact discs containing the rolls are available for sale to general public.[iv] In addition to that, the electoral rolls for the entire country are available on the ECI website.[v] However, the current database is not uniform and standardized, and entries in some constituencies are available only in the local language. The ECI has taken steps to make the database uniform, standardized and centralized.[vi]
Security Concerns
The Registration of Electoral Rules, 1960 is an archaic piece of delegated legislation which is still in force and casts a statutory duty on the ECI to publish the electoral rolls. The publication of electoral rolls is not a threat to security when it is distributed in hard copies and the availability of electoral rolls is limited. The security risks emerge only after the digitization of electoral database, which allows for uniformity, standardization and centralization of the database which in turn makes it vulnerable and subject to abuse. The law has failed to evolve with the change in technology.
In a recent article, Bill Davidow analyzes "the dark side of Moore’s Law" and argues that with the growth processing power there has been a growth in surveillance capabilities and on this note the article is titled, “With Great Computing Power Comes Great Surveillance”[vii] Drawing from Davidow’s argument, with the exponential growth in computing power, search has become convenient, faster and cheap. A uniform, standardized and centralized database bearing the personal information of 790 million voters can be searched and categorized in accordance with the search terms. The personal information of the voters can be used for good, but it can be equally abused if it falls into the wrong hands. Big data analysis or the computing power makes it easier to target voters, as bits and pieces of personal information give a bigger picture of an individual, a community, etc. This can be considered intrusive on individual’s privacy since the personal information of every voter is made available in the public domain
For example, the availability of a centralized, searchable database of voters along with their age would allow the appropriate authorities to identify wards or constituencies, which has a high population of voters above the age of 65. This would help the authority to set up polling booths at closer location with special amenities. However, the same database can be used to search for density of members of a particular community in a ward or constituency based on the name, age, sex of the voters. This information can be used to disrupt elections, target vulnerable communities during an election and rig elections.
Current IT Laws does not mandate the protection of the electoral database
A centralized electoral database of the entire country can be considered as a critical information infrastructure (CII) given the impact it may have on the election which is the cornerstone of any democracy. Under Section 70 of the Information Technology Act, 2000 (IT Act) CII means “the computer resource, incapacitation or destruction of which, shall have debilitating impact on national security, economy.”[viii] However, the appropriate Government has not notified the electoral database as a protected system[ix]. Therefore, information security practices and procedures for a protected system are not applicable to the electoral database.
The Information Technology Rules (IT Rules) are also not applicable to electoral databases, per se. Since, ECI is not a body corporate, the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information), Rules, 2011 (hereinafter Reasonable Security Practices Rules) do not apply to electoral databases. Ignoring that Reasonable Security Practices Rules only apply to a body corporate, the electoral database does fall within the ambit of definition of “personal information”[x] and should arguably be made subject to the Rules.
The intent of the ECI for hosting the entire country’s electoral database online inter alia is to provide electronic service delivery to the citizens. It seeks to provide “electoral look up services for citizens ... for better electoral information services.”[xi] However, the Information Technology (Electronic Service Delivery) Rules, 2011 are not applicable to the electoral database given that it is not notified by the appropriate Government as a service to be delivered electronically. Hence, the encryption and security standards for electronic service delivery are not applicable to electoral rolls.
The IT Act and the IT Rules provide a reasonable scope for the appropriate Government to include electoral databases within the ambit of protected system and electronic service delivery. However, the appropriate government has not taken any steps to notify electoral database as protected system or a mode of electronic service delivery under the existing laws.
Conclusion
Publication of electoral rolls is a necessary part of an election process. It ensures free and fair election and promotes transparency and accountability. But unfettered access to electronic electoral databases may have an adverse effect and would endanger the very goal it seeks to achieve because the electronic database may pose threat to privacy of the voters and also lead to security breach. It may be argued that the ECI is mandated by the law to publish the electoral database and hence, it is beyond the operation of the IT Act. But Section 81 of the IT Act has an overriding effect on any law inconsistent, therewith. The appropriate Government should take necessary steps under the IT Act and notify electoral databases as a protected system.
It is recommended that the Electors Registration Rules, 1960 should be amended, taking into account the advancement in technology. Therefore, the Rules should aim at restricting the unfettered electronic access to the electoral database and also introduce purposive limitation on the use of the electoral database. It should also be noted that more adequate and robust data protection and privacy laws should be put in place, which would regulate the collection, use, storage and processing of databases which are critical to national security.
[i] Pratap Vikram Singh, Post-uproar, EC’s Google tie-up plan may go for a toss, Governance Now, January 7, 2014 available at http://www.governancenow.com/news/regular-story/post-uproar-ecs-google-tie-plan-may-go-toss
[ii] Press Note No.ECI/PN/1/2014, Election Commission of India , January 9, 2014 available at http://eci.nic.in/eci_main1/current/PN09012014.pdf
[iii] Section 74, Indian Evidence Act, 1872
[vi] “At present, in most States and UTs the Electoral Database is kept at the district level. In some cases it is kept even with the vendors. In most States/UTs it is maintained in MS Access, while in some cases it is on a primitive technology like FoxPro and in some other cases on advanced RDBMS like Oracle or Sql Server. The database is not kept in bilingual form in some of the States/UTs, despite instructions of the Commission. In most cases Unicode fonts are not used. The database structure not being uniform in the country, makes it almost impossible for the different databases to talk to each other” – Election Commission of India, Revision of Electoral Rolls with reference to 01-01-2010 as the qualifying date – Integration and Standardization of the database- reg., No. 23/2009-ERS, January 6, 2010 available at eci.nic.in/eci_main/eroll&epic/ins06012010.pdf
[vii] http://www.theatlantic.com/technology/archive/2014/01/with-great-computing-power-comes-great-surveillance/282933/
[viii] Section 70, Information Technology Act, 2000
[ix] Computer resource which directly or indirectly affects the facility of Critical Information Infrastructure
[x] Rule 2(1)(i), Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011
[xi] Press Note No.ECI/PN/1/2014, Election Commission of India , January 9, 2014 available at http://eci.nic.in/eci_main1/current/PN09012014.pdf
GNI Assessment Finds ICT Companies Protect User Privacy and Freedom of Expression
Introduction
In January 2014, the Global Network Initiative (GNI) published the Public Report on the Independent Assessment Process for Google, Microsoft, and Yahoo. GNI is an industry consortium that was started in 2008 with the objective of protecting user’s right to privacy and freedom of expression globally. The main objectives of GNI are to provide a framework for companies that is based on international standards, ensure accountability of ICT companies through independent assessments, create opportunities for policy engagement, and create opportunities for stakeholders from multiple jurisdictions to engage in dialogue with each other. The Centre for Internet and Society, Bangalore, is a member of GNI. Companies based in India have yet to join as members to the GNI network.
Overview of the Public Report
The Public Report provides an overview of assessments completed on the practices and policies of Google, Yahoo, and Microsoft from 2011 - 2013 to measure company compliance with the GNI principles on freedom of expression and privacy. The principles lay out broad guidelines that member companies should seek to incorporate in their internal and external practices and speak to freedom of expression, privacy, responsible company decision making, multi – stakeholder collaboration, and organizational governance, accountability, and transparency. The GNI principles have also been developed with Implementation Guidelines to provide companies with a framework for companies to respond to government requests. The assessment carried out by GNI reviewed cases in each company pertaining to governmental: blocking and filtering, takedown requests, criminalization of speech, intermediary liability, selective enforcement, content surveillance, and requests for user information.
Importantly, the assessment undertaken by GNI finds Yahoo, Microsoft, and Google to be in compliance with the GNI principles on freedom of expression and privacy. The Report highlights practices by the companies that work to protect freedom of expression and privacy such as conducting human rights impact assessments, issuing transparency reports, and notifying affected users when content is removed, have been, adopted by these companies. For example, Google conducts Human Rights Impact Assessments to assess potential threats to freedom of expression and privacy. Google also has in place internal processes to review governmental requests impacting freedom of expression and privacy, and the legal team at Google prepares a “global removal report” to provide a bird’s eye view of trends emerging from content removal requests. If Google has the email address of a user who’s posted content is removed, Google will often notify the user and directs the user to the Chilling Effects website. Google has also published a transparency report since 2010. Like Google, Microsoft conducts Human Rights Impact Assessments before making decisions on whether to incorporate certain features into its platforms when operating in high risk markets. Microsoft has also issued two global law enforcement requests reports in 2013. Yahoo has established a Business and Human Rights Program to ensure responsible actions are taken by the company with regards to freedom of expression and privacy, and now issues transparency reports about government requests. Yahoo’s Public Policy team also engages in dialogue with governments on an international level about existing and proposed legislation impacting and implicating privacy and freedom of expression.
The Report highlights challenges to compliance with the GNI principles that companies face – namely legal restraints and mandates that they are faced with. On the issue of transparency, the assessment found that companies do not disclose information when there are legal prohibitions on such disclosure, when users privacy would be implicated, when companies choose to assert attorney client privilege, and when trade secrets are involved. Despite this, the assessment found that companies do deny and push back on governmental requests impacting freedom of expression and privacy for reasons such as the request needed clarification and modification, or that the request needed to follow established procedure.
A number of findings came out of the assessments undertaken for the Report including:
- As demonstrated by the lack of ability to access information about secret national security requests, and the lack of ability for companies to disclose information on this topic there is a dire need for governments to reform surveillance policy and law impacting freedom of expression and privacy.
- The implementation of the GNI Principles is challenging when a company is undergoing an acquisition. In this scenario, contractual provisions limiting third party disclosure are critical in ensuring protection of privacy and free expression rights.
- Companies need to pro-actively and on an ongoing basis internally review governmental restrictions on content to determine if it is in compliance with the commitment made by that company to the GNI Principles.
The assessment resulted in GNI defining a number of actionable (non-binding) recommendations for companies such as:
- Improving the integration of human rights considerations in the due diligence process with respect to the acquiring and selling companies.
- Consider the impact of hardware on freedom of expression and privacy.
- Improve external and internal reporting.
- Review employee access to user data to ensure that employee access rights are restricted by both policy and technical measures on a ‘need to know’ basis across global operations.
- Review executive management training.
- Improve stakeholder engagement.
- Improve communication with users.
- Increase sharing of best practices.
- The GNI principles are focused on freedom of expression and privacy and are based on internationally recognized laws and standards for human rights.
NSA leaks, global push for governmental surveillance reform, and the Public Report
With special attention given to the various companies responses to the NSA leaks, the Report notes that in response to the NSA leaks the assessed companies have issued public statements and filed legal challenges with the US government and filed suit with the FISA Court seeking the right to disclose data relating to the number of FISA requests received with the public. All three companies have also supported legislation and policy that would allow for such transparency. Furthermore in December 2014, the companies , along with other internet companies, developed and issued the five Principles on Global Government Surveillance Reform. Similar to other efforts to end mass and disproportionate surveillance, such as the Necessary and Proportionate principles, the Principles on Global Government Surveillance Reform address: Limiting Governments’ Authority to Collect Users’ Information, Oversight and Accountability, Transparency about Government Demands, Respecting the Free Flow of Information, Avoiding Conflicts Among Governments. Other companies that signed these principles include AOL, Facebook, LinkedIn, and Twitter.
Along these lines, on January 14th, GNI released the statement “Surveillance Reforms to Protect Rights and Restore Trust”, urging the U.S Government to review and enact surveillance legislation that incorporate a ‘rights based’ approach to issues involving national security. In the statement, GNI specifically recommends the Government to action and: end mass collection of communications metadata, protect and uphold the rights of non-Americans, continue to increase transparency of surveillance practices, support the use of strong encryption standards.
Conclusion and way forward
Looking ahead, GNI is planning on developing and implementing a mechanism to address effectively address consumer engagement and complaints issued by individuals who feel that GNI member companies have not acted consistently with the commitments made as a GNI member. GNI is also looking to expand work around public policy and surveillance.
The Public Report on the Independent Assessment Process for Google, Microsoft, and Yahoo is an important step towards ensuring ICT sector companies are accountable to the public in their practices impacting freedom of expression and privacy. The assessment comes at a time when ICT companies often find themselves stuck between a rock and a hard place – with Governments issuing surveillance and censorship demands with mandates for non-disclosure, and the public demanding transparency, company resistance to such demands from the Government, and a strong commitment to users freedom of expression and privacy. Hopefully, the GNI assessment is and will evolve into a middle ground for ICT companies – where they can be accountable to the public and their customers and compliant with Governmental mandates in all jurisdictions that they operate in. It will be interesting to see if in the future Indian companies join GNI as members and being to adopt the GNI principles and undergo GNI assessments.
Interview with Mathew Thomas from the Say No to UID campaign - UID Court Cases
Hi Mathew! We've heard that you've been in court a lot over the last few years with regards to the UID scheme. Could you please tell us about the UID case you have filed?
In early 2012, I filed a civil suit at the Bangalore Court to declare the UID scheme illegal and to stop further biometric enrollments. I alleged that foreign agencies are involved in the process of biometric enrollment, and that cases of corruption have occurred with regards to the companies contracted by the UID Authority of India (UIDAI). Many dubious companies have been empanelled for biometric enrollments by the UIDAI and many cases of corruption have been noted, especially with regards to the preparation of biometric databases for below poverty line (BPL) ration cards in Karnataka.
In 2010, according to a government audit report, COMAT Technologies Private Limited had a contract with the Karnataka Government and was required to undertake a door-to-door survey and to set up biometric devices. COMAT Technologies Private Limited was paid ₹ 542.3 million for this purpose, but it turns out that the company did not comply with the terms of the contract and did not fullfill its obligations under the contract. Even though COMAT Technologies Private Limited had been contracted and had been paid ₹ 542.3 million, the company did not hand over any biometric device to the Karnataka Government. Instead, when the company got questioned, it walked away from the contract in 2010, even though it had been paid for a service it did not deliver.
In the same year, 2010, COMAT Technologies was empanelled as an Enrolling Agency of the UIDAI. COMAT Technologies also carries out enrollments in Mysore and a TV channel sting operation revealed that fake IDs were being issued in the Mysore enrollment center. After much persuasion, the e-Government department of Karnataka informed me that they have filed an FIR. And this is just one case of a corrupt company empanelled as an enrollement agency with the UIDAI. Many similar cases with other companies have occurred in other cities in India, such as Mumbai, where the empanelled agencies have committed fraud and police complaints have been filed. But unfortunately, there is no publicly available information on the state of the investigations.
As such, I filed a case at the Bangalore Court and stated that the whole UID system is insecure, that it will not achieve the objective of preventing leakages of welfare subsidies and that, therefore, it is a waste of public funds, which also affects individuals' right to privacy and right to life. In my complaint in the civil court I made allegations of corruption and dangers to national security backed by documentary evidence. According to Order 8 of the Civil Procedure Code (CPC), defendants are required to specifically deny each of the allegations against them and if they don't, the court is required to accept the allegations as accurate. According to law, vague, bald denials are not acceptable in courts. Interestingly enough, the defendants in this court case did not deny any of the allegations, but instead stated that they (allegations) are “trivial” and requested the judge to dismiss the case without a trial. The judge requested the defendants to file a written application, asking for the suit to be dismissed under Order 7, Rule 11, of the Civil Procedure Code. Nonetheless, in May 2012, the judge observed that this is a serious case which should not be dismissed and that he would like to have a daily hearing of the case, especially since the case was grounded on the allegation that thousands of crores of rupees of public money are spent every day.
However, one month later in June 2012, the judge dismissed the case by stating that I did not have a “cause of action” and that the case is not of civil nature under Section 9 of the Code of Civil Procedure. I argued that tax payers have a right to know where their money is going and that we all have a right to privacy and that therefore, I did have a cause for action. I quoted the Supreme Court case setting out the law relating to the meaning of “civil nature”. The Apex court said, “Anything which is not of criminal nature is of civil nature”. I also quoted several court precedents which explained conditions under which complaints could be dismissed under Order VII Rule 11. Unfortunately though, the judge dismissed all of this and suggested that I should take this case to the High Court or to the Supreme Court, since the Bangalore Court did not have the authority to address the violation of fundamental human rights. In my opinion, the fallacy in this judgement was that, on the one hand, the judge stated in his order that there was “no cause for action”, but on the other hand, he said that I should take the case to the High Court or to the Supreme Court! And on top of that, the judge stated that my case was frivolous and levied on me a Rs. 25, 000 fine, because apparently I was “wasting the court's time” !
In addition to all of this, the judge made a very intriguing statement in his order: he claimed that the biometric enrollment with the UIDAI is voluntary and that therefore I need not enrol. I argued that although the UID is voluntary in theory, it is actually mandatory on many levels, especially since access to many governmental services require enrollment with the UIDAI. Nonetheless, the judge insisted that the UID is purely voluntary and that if I am not happy with the UID, then I should just “stay at home”.
And how did the case continue thereafter?
In October 2012 I appealed against this to the High Court by stating that there was a misapplication of Order 7, Rule 11, of the Civil Procedure Code and requested the High Court to send the suit back for trial at the Bangalore Court.
Now, when you appeal in India, the Court has to issue notices to the opposite party, which are usually sent by registered post. However, nothing was happening, so I filed a number of applications to hear the case. The registrar’s office filed a number of trivial “objections” with which I needed to comply and this took three months, until January 2013. For example, one “objection” was that the lower court order stated the date of the order as "03-07-12", whereas I had mentioned the date as 3 July 2012. Then they would argue that the acknowledgement of the receipt of the notice from the respondents was not received. The High Court is located next to the head post office (GPO) in Bangalore and normally it would be sent there, then directly to the GPO in Delhi and from there to the Planning Commission or to the UIDAI. Yet, the procedure was delayed because apparently the notices weren't sent. In one hearing, the court clerk said that the address of the defendant was wrong and that the address of the Planning Commission should also be included. All in all, it seemed to me like there was some deliberate attempt to delay the procedure and the dismissal of the case by the Bangalore Court seemed very questionable. As a result, in January 2013, I asked the High Court to permit me to personally hand over my appeal to the Government Council. And finally, on 17th December 2013, my appeal was heard by the Bangalore High Court!
Over the last three months, the defendants have not filed any counter affidavit. Instead, the Government Council came to the High Court and stated that I have not filed a “paper book” (which includes depositions and evidence, among other things). However, the judge stated that this is not a case which requires a “paper book”, since my appeal was about the misapplication of Order 7, Rule 11, of the Civil Procedure Code. Then the Government Council asked for more time to review the appeal and it is has been postponed.
Have there been any other recent court cases against the UID?
Yes. While all of this was going on, retired judge, Justice Puttaswamy, filed a petition in the Supreme Court, stating that the UID scheme is illegal, since it violates article 73 of the Constitution. Aruna Roy, who is an activist at the National Council for People’s Right to Information, has also filed a petition where she has questioned the UID because it violates privacy rights and the rights of the poor.
Furthermore, petitions have been filed in the Madras High Court and in the Mumbai High Court. In 2012, it was argued in the Madras High Court that the only legal provision for taking fingerprints exists under the Prisoners Act, whereas the UIDAI is taking the fingerprints of people who are not prisoners and therefore it is illegal. In 2013, Vikram Crishna, Kamayani Bahl and a few others argued in the Mumbai High Court that the right to privacy is being violated through the UID scheme. It is noteworthy that in most of these cases, the defendants have not filed any counter-arguments. The only exceptions were in the Aruna Roy and Puttaswamy cases, where the defendants claimed that the UID is secure and supported it in general. In the end, the Supreme Court directed that the cases in Mumbai and Madras should be clubbed together and addressed by it. As such, the cases filed in the Madras and Mumbai High Courts have been sent to the Supreme Court of India.
Major General Vombathakere also filed a petition in the Supreme Court, arguing that the UID scheme violates individuals' right to privacy. When the counsel for the General commenced his arguments the judge pointed to the possibility of the Government passing the NIA Bill soon, which will contain provisions for privacy, as stated by the Government. As such, the judge implied that if the Government passes such a law the argument, that the Government is implementing the scheme in a legal vacuum, may not be valid.
So what is the status of your pending court cases?
Well, I impleaded myself in Aruna Roy's petition and brought my arguments with regards to corruption in the case of companies contracted with the UIDAI and the danger to national security through the involvement of persons linked to US intelligence agencies. The last hearing in the Supreme Court was on 10th December 2013, but it was postponed to 28 January 2014. So in short, in the Supreme Court I am currently filing a case for investigation with regards to corruption and links with foreign intelligence agencies by companies contracted with the UIDAI, while in the Bangalore High Court, I have appealed a civil trial with regards to the misplacement of Order 7, Rule 11, of the Civil Procedure Code.
Surveillance and the Indian Constitution - Part 2: Gobind and the Compelling State Interest Test
After its judgment in Kharak Singh, the Court was not concerned with the privacy question for a while. The next case that dealt – peripherally – with the issue came eleven years later. In R.M. Malkani v State of Maharashtra, the Court held that attaching a recording device to a person’s telephone did not violate S. 25 of the Telegraph Act, because
"where a person talking on the telephone allows another person to record it or to hear it, it can-not be said that the other person who is allowed to do so is damaging, removing, tampering, touching machinery battery line or post for intercepting or acquainting himself with the contents of any message. There was no element of coercion or compulsion in attaching the tape recorder to the telephone."
Although this case was primarily about the admissibility of evidence, the Court also took time out to consider – and reject – a privacy-based Article 21 argument, holding that:
"Article 21 was invoked by submitting that the privacy of the appellant’s conversation was invaded. Article 21 contemplates procedure established by law with regard to deprivation of life or personal liberty. The telephonic conversation of an innocent citizen will be protected by Courts against wrongful or high handed interference by tapping the conversation. The protection is not for the guilty citizen against the efforts of the police to vindicate the law and prevent corruption of public servants. It must not be understood that the Courts will tolerate safeguards for the protection of the citizen to be imperiled by permitting the police to proceed by unlawful or irregular methods."
Apart from the fact that it joined Kharak Singh in refusing to expressly find a privacy right within the contours of Article 21, there is something else that unites Kharak Singh and R.M. Malkani: they hypothetical in Kharak Singh became a reality in Malkani – what saved the telephone tapping precisely because it was directed at "… a guilty person", with the Court specifically holding that the laws were not for targeting innocent people. Once again, then, the targeted and specific nature of interception became a crucial – and in this case, a decisive – factor. One year later, in another search and seizure case, Pooran Mal v Inspector, the Court cited M.P. Sharma and stuck to its guns, refusing to incorporate the Fourth Amendment into Indian Constitutional law.
It is Gobind v State of MP, decided in 1975, that marks the watershed moment for Indian privacy law in the Constitution. Like Kharak Singh, Gobind also involved domiciliary visits to the house of a history-sheeter. Unlike Kharak Singh, however, in Gobind the Court found that the Regulations did have statutory backing – S. 46(2)(c) of the Police Act, which allowed State Government to make notifications giving effect to the provisions of the Act, one of which was the prevention of commission of offences. The surveillance provisions in the impugned regulations, according to the Court, were indeed for the purpose of preventing offences, since they were specifically aimed at repeat offenders. To that extent, then, the Court found that there existed a valid “law” for the purposes of Articles 19 and 21.
By this time, of course, American constitutional law had moved forward significantly from eleven years ago, when Kharak Singh had been decided. The Court was able to invoke Griswold v Connecticut and Roe v Wade, both of which had found a "privacy" as an "interstitial" or "penumbral" right in the American Constitution – that is, not reducible to any one provision, but implicit in a number of separate provisions taken together. The Court ran together a number of American authorities, referred to Locke and Kant, to dignity, to liberty and to autonomy, and ended by holding, somewhat confusingly:
“the right to privacy must encompass and protect the personal intimacies of the home, the family marriage, motherhood, procreation and child rearing. This catalogue approach to the question is obviously not as instructive as it does not give analytical picture of that distinctive characteristics of the right of privacy. Perhaps, the only suggestion that can be offered as unifying principle underlying the concept has been the assertion that a claimed right must be a fundamental right implicit in the concept of ordered liberty… there are two possible theories for protecting privacy of home. The first is that activities in the home harm others only to the extent that they cause offence resulting from the mere thought that individuals might he engaging in such activities and that such ‘harm’ is not Constitutionally protective by the state. The second is that individuals need a place of sanctuary where they can be free from societal control. The importance of such a sanctuary is that individuals can drop the mask, desist for a while from projecting on the world the image they want to be accepted as themselves, an image that may reflect the values of their peers rather than the realities of their natures… the right to privacy in any event will necessarily have to go through a process of case-by-case development."
But if no clear principle emerges out of the Court’s elucidation of the right, it was fairly unambiguous in stressing the importance of the right itself. Interestingly, it grounded the right within the context of the freedom struggle. "Our founding fathers," it observed, "were thoroughly opposed to a Police Raj even as our history of the struggle for freedom has borne eloquent testimony to it." (Para 30) The parallels to the American Fourth Amendment are striking here: in his historical analysis Akhil Amar tells us that the Fourth Amendment was meant precisely to avoid the various abuses of unreasonable searches and seizures that were common in England at the time.
The parallels with the United States become even more pronounced, however, when the Court examined the grounds for limiting the right to privacy. "Assuming that the fundamental rights explicitly guaranteed to a citizen have penumbral zones and that the right to privacy is itself a fundamental right, that fundamental right must be subject to restriction on the basis of compelling public interest." "Compelling public interest" is an interesting phrase, for two reasons. First, “public interest” is a ground for fundamental rights restrictions under Article 19 (see, e.g., Article 19(6)), but the text of the Article 19 restrictions do not use – and the Court, in interpreting them, has not held – that the public interest must be “compelling”. This suggests a stricter standard of review for an Article 21 privacy right violation than Article 19 violations. This is buttressed by the fact that in the same paragraph, the Court ended by observing: “even if it be assumed that Article 19(5) [restrictions upon the freedom of movement] does not apply in terms, as the right to privacy of movement cannot be absolute, a law imposing reasonable restriction upon it for compelling interest of State must be upheld as valid.” The Court echoes the language of 19(5), and adds the word “compelling”. This surely cannot be an oversight.
More importantly – the compelling State interest is an American test, used often in equal protection cases and cases of discrimination, where “suspect classes” (such as race) are at issue. Because of the importance of the right at issue, the compelling state interest test goes hand-in-hand with another test: narrow tailoring. Narrow tailoring places a burden upon the State to demonstrate that its restriction is tailored in a manner that infringes the right as narrowest manner that is possible to achieve its goals. The statement of the rule may be found in the American Supreme Court case of Grutter v Bollinger:
"Even in the limited circumstance when drawing racial distinctions is permissible to further a compelling state interest, government is still constrained under equal protection clause in how it may pursue that end: the means chosen to accomplish the government’s asserted purpose must be specifically and narrowly framed to accomplish that purpose."
To take an extremely trivial example that will illustrate the point: the State wants to ban hate speech against Dalits. It passes legislation that bans “all speech that disrespects Dalits.” This is not narrowly tailored, because while all hate speech against Dalits necessarily disrespects them, all speech that disrespects Dalits is not necessarily hate speech. It was possible for the government to pass legislation banning only hate speech against Dalits, one that would have infringed upon free speech more narrowly than the “disrespect law”, and still achieved its goals. The law is not narrowly tailored.
Crucially, then, the Court in Gobind seemed to implicitly accept the narrow-tailoring flip side of the compelling state interest coin. On the constitutionality of the Police Regulations itself, it upheld their constitutionality by reading them narrowly. Here is what the Court said:
“Regulation 855, in our view, empowers surveillance only of persons against whom reasonable materials exist to induce the opinion that they show a determination, to lead a life of crime – crime in this context being confined to such as involve public peace or security only and if they are dangerous security risks. Mere convictions in criminal cases where nothing gravely imperiling safety of society cannot be regarded as warranting surveillance under this Regulation. Similarly, domiciliary visits and picketing by the police should be reduced to the clearest cases of danger to community security and not routine follow-up at the end of a conviction or release from prison or at the whim of a police officer.”
But Regulation 855 did not refer to the gravity of the crime at all. Thus, the Court was able to uphold its constitutionality only by narrowing its scope in a manner that the State’s objective of securing public safety was met in a way that minimally infringed the right to privacy.
Therefore, whether the Gobind bench was aware of it or not, its holding incorporates into Indian constitutional law and the right to privacy, not just the compelling State interest test, but narrow tailoring as well. The implications for the CMS are obvious. Because with narrow tailoring, the State must demonstrate that bulk surveillance of all individuals, whether guilty or innocent, suspected of crimes or not suspected of crimes (whether reasonably or otherwise), possessing a past criminal record or not, speaking to each other of breaking up the government or breaking up a relationship – every bit of data must be collected to achieve the goal of maintaining public security, and that nothing narrower will suffice. Can the State demonstrate this? I do not think it can, but at the very least, it should be made to do so in open Court.
Making the Powerful Accountable
CANDID CAMERA: Media coverage is often critical to whether someone relatively powerless is able to assert her rights against a very powerful person. Photo: Monica Tiwari
Chinmayi Arun's Op-ed was published in the Hindu on January 29, 2014.
It is odd indeed that the Delhi High Court seems to believe that sensational media coverage can sway the Supreme Court into prejudice against one of its own retired judges. Justice Manmohan Singh of the Delhi High Court has said in Swatanter Kumar v. Indian Express and others that the pervasive sensational media coverage of the sexual harassment allegations against the retired Supreme Court judge 'may also result in creating an atmosphere in the form of public opinion wherein a person may not be able to put forward his defence properly and his likelihood of getting fair trial would be seriously impaired.' This Delhi High court judgment has drawn upon the controversial 2011 Supreme Court judgment in Sahara India Real Estate Corp. Ltd v. SEBI (referred to as the Gag Order case here) to prohibit the media from publishing headlines connecting retired Justice Swatanter Kumar with the intern's allegations, and from publishing his photograph in connection with the allegations.
Although the Gag Order judgment was criticised at the time that it was delivered Swatanter Kumar v. Indian Express illustrates its detractors' argument more vividly that anyone could have imagined.
Sukumar Muralidharan wrote of Gag Order case that the postponement (of media coverage) order remedy that it created, could become an "instrument in the hands of wealthy and influential litigants, to subvert the course of open justice".
Here we find that although a former Supreme Court judge is pitted against a very young former intern within a system over which he once presided, Justice Manmohan Singh seems to think that it is the judge who is danger of being victimised.
The Swatanter Kumar judgment was enabled by both the Gag Order case as well as the 1966 Supreme Court judgment in Naresh Sridhar Mirajkar v. State of Maharashtra, which in combination created a process for veiling court proceedings. Naresh Mirajkar stated that courts' inherent powers extend to barring media reports and comments on ongoing trials in the interests of justice, and that such powers do not violate the right to freedom of speech; and the Gag Order case created an instrument - the 'postponement order' - for litigants, such that they can have media reports of a pending case restricted. The manner in which this is used in the Swatanter Kumar judgment raises very worrying questions about how the judiciary views the boundaries of the right to freedom of expression, particularly in the context of reporting court proceedings.
Broad power to restrict reporting
The Gag Order case was problematic: it used arguments for legitimate restraints on media reporting in exceptional circumstances, to permit restrictions on media reporting of court proceedings under circumstances 'where there is a real and substantial risk of prejudice to fairness of the trial or to proper administration of justice'. The Supreme Court refused to narrow this or clarify what publications would fall within this category. It merely stated that this would depend on the content and context of the offending publication, and that no 'straightjacket formula' could be created to enumerate these categories. This leaves higher judiciary with a broad discretionary power to decide what amounts to
legitimate restraints on media reporting, using an ambiguous standard. Exercise of this power to veil proceedings involving powerful public figures whose actions have public implications, imperils openness and transparency when they are most critical.
Court proceedings are usually open to the public. This openness serves as a check on the judiciary, and ensures public faith in the judiciary. In countries as large as ours, media coverage of important cases ensures actual openness of court proceedings - we are able to follow the arguments made by petitioners who ask that homosexuality be decriminalised, the trial of suspected terrorists and alleged murderers, and the manner in which our legal system handles sexual harassment complaints filed by young women.
When court proceedings are closed to the public (known as 'in-camera' trials) or when media dissemination of information about them is restricted, the openness and transparency of court proceedings is compromised. Such compromise of transparency does take place in many countries, to protect the rights of the parties involved, or prevent miscarriage of justice. For example, child-participants are protected by holding trials in-camera; names of parties to court proceedings are withheld to protect their privacy sometimes; and in countries where juries determine guilt, news coverage that may prejudice the jury is also restricted.
The damage done
Although the Supreme Court stated in principle that the openness of court proceedings should only be restricted where strictly necessary, this appears to lend itself to very varied interpretation. For example, it is very difficult for some of us to understand why it was strictly necessary to restrict media coverage of sexual harassment proceedings in the Swatanter Kumar case. J. Manmohan Singh on the other hand seems to believe that the adverse public opinion will affect the retired judge's chance of getting a fair trial. His judgment also seems to indicate his concern that the sensational headlines will impact the public confidence in the Supreme Court.
The Delhi High Court's apprehension about the effects of the newspaper coverage on the reputation of the judge did not need to translate into a prior restraint on media coverage. They may better have been addressed later, by evaluating a defamation claim pertaining to published material. The larger concerns about the reputation of the judiciary are better addressed by openness: if powerful public figures, especially those with as much influence as a former Supreme Court judge are not subjected to transparent court proceedings, the opacity in the face of such a critical issue is likely to undermine public faith in the judiciary as an institution.Such opacity undermines the purpose of open courts. It is much worse for the reputation of the judiciary than publicised complaints about individual judges.
Since the Delhi High Court ruling, there has been little media coverage of the sexual harassment case. Suppression of media coverage leaves the young woman comparatively isolated. Wide coverage of the harassment complaint involving Justice Ganguly, helped the intern in that case find support. The circulation of information enabled other former interns as well as a larger network of lawyers and activists, reach out to her. This is apart from the general pressure to be fair that arises when a case is being followed closely by the public. Media coverage is often critical to whether someone relatively powerless is able to assert her rights against a very powerful person. This is why media freedom is sacred to democracies.
If the Supreme Court was confident that the high courts in India would use their broad discretionary power under the Gag Order case sparingly and only in the interests of justice, the Swatanter Kumar case should offer it grounds to reconsider. Openness and freedom of expression are not meant to be diluted to protect the powerful - they exist precisely to ensure that even the powerful are held accountable by state systems that they might otherwise be able to sway.
(Chinmayi Arun is research director, Centre for Communication Governance, National Law University, Delhi, and fellow, Centre for Internet and Society, Bangalore.)
India's Central Monitoring System (CMS): Something to Worry About?
The idea of a Panoptikon, of monitoring all communications in India and centrally storing such data is not new. It was first envisioned in 2009, following the 2008 Mumbai terrorist attacks. As such, the Central Monitoring System (CMS) started off as a project run by the Centre for Communication Security Research and Monitoring (CCSRM), along with the Telecom Testing and Security Certification (TTSC) project.
The Central Monitoring System (CMS), which was largely covered by the media in 2013, was actually approved by the Cabinet Committee on Security (CCS) on 16th June 2011 and the pilot project was completed by 30th September 2011. Ever since, the CMS has been operated by India's Telecom Enforcement Resource and Monitoring (TERM) cells, and has been implemented by the Centre for Development of Telematics (C-DOT), which is an Indian Government owned telecommunications technology development centre. The CMS has been implemented in three phases, each one taking about 13-14 months. As of June 2013, government funding of the CMS has reached at least Rs. 450 crore (around $72 million).
In order to require Telecom Service Providers (TSPs) to intercept all telecommunications in India as part of the CMS, clause 41.10 of the Unified Access Services (UAS) License Agreement was amended in June 2013. In particular, the amended clause includes the following:
“But, in case of Centralized Monitoring System (CMS), Licensee shall provide the connectivity upto the nearest point of presence of MPLS (Multi Protocol Label Switching) network of the CMS at its own cost in the form of dark fibre with redundancy. If dark fibre connectivity is not readily available, the connectivity may be extended in the form of 10 Mbps bandwidth upgradeable upto 45 Mbps or higher as conveyed by the Governemnt, till such time the dark fibre connectivity is established. However, LICENSEE shall endeavor to establish connectivity by dark optical fibre at the earilest. From the point of presence of MPLS network of CMS onwards traffic will be handled by the Government at its own cost.”
Furthermore, draft Rule 419B under Section 5(2) of the Indian Telegraph Act, 1885, allows for the disclosure of “message related information” / Call Data Records (CDR) to Indian authorities. Call Data Records, otherwise known as Call Detail Records, contain metadata (data about data) that describe a telecomunication transaction, but not the content of that transaction. In other words, Call Data Records include data such as the phone numbers of the calling and called parties, the duration of the call, the time and date of the call, and other such information, while excluding the content of what was said during such calls. According to draft Rule 419B, directions for the disclosure of Call Data Records can only be issued on a national level through orders by the Secretary to the Government of India in the Ministry of Home Affairs, while on the state level, orders can only be issued by the Secretary to the State Government in charge of the Home Department.
Other than this draft Rule and the amendment to clause 41.10 of the UAS License Agreement, no law exists which mandates or regulates the Central Monitoring System (CMS). This mass surveillance system is merely regulated under Section 5(2) of the Indian Telegraph Act, 1885, which empowers the Indian Government to intercept communications on the occurence of any “public emergency” or in the interest of “public safety”, when it is deemed “necessary or expedient” to do so in the following instances:
-
the interests of the sovereignty and integrity of India
-
the security of the State
-
friendly relations with foreign states
-
public order
-
for preventing incitement to the commission of an offense
However, Section 5(2) of the Indian Telegraph Act, 1885, appears to be rather broad and vague, and fails to explicitly regulate the details of how the Central Monitoring System (CMS) should function. As such, the CMS appears to be inadequately regulated, which raises many questions with regards to its potential misuse and subsequent violation of Indian's right to privacy and other human rights.
So how does the Central Monitoring System (CMS) actually work?
We have known for quite a while now that the Central Monitoring System (CMS) gives India's security agencies and income tax officials centralized access to the country's telecommunications network. The question, though, is how.
Well, prior to the CMS, all service providers in India were required to have Lawful Interception Systems installed at their premises in order to carry out targeted surveillance of individuals by monitoring communications running through their networks. Now, in the CMS era, all TSPs in India are required to integrate Interception Store & Forward (ISF) servers with their pre-existing Lawful Interception Systems. Once ISF servers are installed in the premises of TSPs in India and integrated with Lawful Interception Systems, they are then connected to the Regional Monitoring Centres (RMC) of the CMS. Each Regional Monitoring Centre (RMC) in India is connected to the Central Monitoring System (CMS). In short, the CMS involves the collection and storage of data intercepted by TSPs in central and regional databases.
In other words, all data intercepted by TSPs is automatically transmitted to Regional Monitoring Centres, and subsequently automatically transmitted to the Central Monitoring System. This means that not only can the CMS authority have centralized access to all data intercepted by TSPs all over India, but that the authority can also bypass service providers in gaining such access. This is due to the fact that, unlike in the case of so-called “lawful interception” where the nodal officers of TSPs are notified about interception requests, the CMS allows for data to be automatically transmitted to its datacentre, without the involvement of TSPs.
The above is illustrated in the following chart:
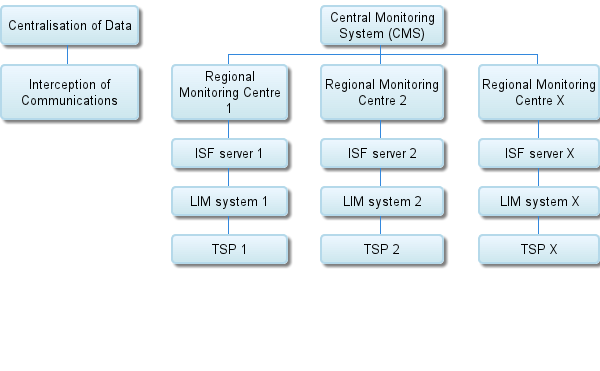
The interface testing of TSPs and their Lawful Interception Systems has already been completed and, as of June 2013, 70 ISF servers have been purchased for six License Service Areas and are being integrated with the Lawful Interception Systems of TSPs. The Centre for Development of Telematics has already fully installed and integrated two ISF servers in the premises of two of India's largest service providers: MTNL and Tata Communications Limited. In Delhi, ISF servers which connect with the CMS have been installed for all TSPs and testing has been completed. In Haryana, three ISF servers have already been installed in the premises of TSPs and the rest of currently being installed. In Chennai, five ISF servers have been installed so far, while in Karnataka, ISF servers are currently being integrated with the Lawful Interception Systems of the TSPs in the region.
The Centre for Development of Telematics plans to integrate ISF servers which connect with the CMS in the premises of service providers in the following regions:
-
Delhi
-
Maharashtra
-
Kolkata
-
Uttar Pradesh (West)
-
Andhra Pradesh
-
Uttar Pradesh (East)
-
Kerala
-
Gujarat
-
Madhya Pradesh
-
Punjab
-
Haryana
With regards to the UAS License Agreement that TSPs are required to comply with, amended clause 41.10 specifies certain details about how the CMS functions. In particular, the amended clause mandates that TSPs in India will provide connectivity upto the nearest point of presence of MPLS (Multi Protocol Label Switching) network of the CMS at their own cost and in the form of dark optical fibre. From the MPLS network of the CMS onwards, traffic will be handled by the Government at its own cost. It is noteworthy that a Memorandum of Understanding (MoU) for MPLS connectivity has been signed with one of India's largest ISPs/TSPs: BSNL. In fact, Rs. 4.8 crore have been given to BSNL for interconnecting 81 CMS locations of the following License Service Areas:
-
Delhi
-
Mumbai
-
Haryana
-
Rajasthan
-
Kolkata
-
Karnataka
-
Chennai
-
Punjab
Clause 41.10 of the UAS License Agreement also mandates that the hardware and software required for monitoring calls will be engineered, provided, installed and maintained by the TSPs at their own cost. This implies that TSP customers in India will likely have to pay for more expensive services, supposedly to “increase their safety”. Moreover, this clause mandates that TSPs are required to monitor at least 30 simultaneous calls for each of the nine designated law enforcement agencies. In addition to monitored calls, clause 41.10 of the UAS License Agreement also requires service providers to make the following records available to Indian law enforcement agencies:
-
Called/calling party mobile/PSTN numbers
-
Time/date and duration of interception
-
Location of target subscribers (Cell ID & GPS)
-
Data records for failed call attempts
-
CDR (Call Data Records) of Roaming Subscriber
-
Forwarded telephone numbers by target subscriber
Interception requests from law enforcement agencies are provisioned by the CMS authority, which has access to the intercepted data by all TSPs in India and which is stored in a central database. As of June 2013, 80% of the CMS Physical Data Centre has been built so far.
In short, the CMS replaces the existing manual system of interception and monitoring to an automated system, which is operated by TERM cells and implemented by the Centre for Development of Telematics. Training has been imparted to the following law enforcement agencies:
-
Intelligence Bureau (IB)
-
Central Bureau of Investigation (CBI)
-
Directorate of Revenue Intelligence (DRI)
-
Research & Analysis Wing (RAW)
-
National Investigation Agency (NIA)
-
Delhi Police
And should we even be worried about the Central Monitoring System?
Well, according to the brief material for the Honourable MOC and IT Press Briefing on 16th July 2013, we should not be worried about the Central Monitoring System. Over the last year, media reports have expressed fear that the Central Monitoring System will infringe upon citizen's right to privacy and other human rights. However, Indian authorities have argued that the Central Monitoring System will better protect the privacy of individuals and maintain their security due to the following reasons:
-
The CMS will just automate the existing process of interception and monitoring, and all the existing safeguards will continue to exist
-
The interception and monitoring of communications will continue to be in accordance with Section 5(2) of the Indian Telegraph Act, 1885, read with Rule 419A
-
The CMS will enhance the privacy of citizens, because it will no longer be necessary to take authorisation from the nodal officer of the Telecom Service Providers (TSPs) – who comes to know whose and which phone is being intercepted
-
The CMS authority will provision the interception requests from law enforcement agencies and hence, a complete check and balance will be ensured, since the provisioning entity and the requesting entity will be different and the CMS authority will not have access to content data
-
A non-erasable command log of all provisioning activities will be maintained by the system, which can be examined anytime for misuse and which provides an additional safeguard
While some of these arguments may potentially allow for better protections, I personally fundamentally disagree with the notion that a centralised monitoring system is something not to worry about. But let's start-off by having a look at the above arguments.
The first argument appears to imply that the pre-existing process of interception and monitoring was privacy-friendly or at least “a good thing” and that existing safeguards are adequate. As such, it is emphasised that the process of interception and monitoring will “just” be automated, while posing no real threat. I fundamentally disagree with this argument due to several reasons. First of all, the pre-existing regime of interception and monitoring appears to be rather problematic because India lacks privacy legislation which could safeguard citizens from potential abuse. Secondly, the very interception which is enabled through various sections of the Information Technology (Amendment) Act, 2008, and the Indian Telegraph Act, 1885, potentially infringe upon individual's right to privacy and other human rights.
May I remind you of Section 69 of the Information Technology (Amendment) Act, 2008, which allows for the interception of all information transmitted through a computer resource and which requires users to assist authorities with the decryption of their data, if they are asked to do so, or face a jail sentence of up to seven years. The debate on the constitutionality of the various sections of the law which allow for the interception of communications in India is still unsettled, which means that the pre-existing interception and monitoring of communications remains an ambiguous matter. And so, while the interception of communications in general is rather concerning due to dracodian sections of the law and due to the absence of privacy legislation, automating the process of interception does not appear reassuring at all. On the contrary, it seems like something in the lines of: “We have already been spying on you. Now we will just be doing it quicker and more efficiently.”
The second argument appears inadequate too. Section 5(2) of the Indian Telegraph Act, 1885, states that the interception of communications can be carried out on the occurence of a “public emergency” or in the interest of “public safety” when it is deemed “necessary or expedient” to do so under certain conditions which were previously mentioned. However, this section of the law does not mandate the establishment of the Central Monitoring System, nor does it regulate how and under what conditions this surveillance system will function. On the contrary, Section 5(2) of the Indian Telegraph Act, 1885, clearly mandates targeted surveillance, while the Central Monitoring System could potentially undertake mass surveillance. Since the process of interception is automated and, under clause 41.16 of the Unified License (Access Services) Agreement, service providers are required to provision at least 3,000 calls for monitoring to nine law enforcement agencies, it is likely that the CMS undertakes mass surveillance. Thus, it is unclear if the very nature of the CMS falls under Section 5(2) of the Indian Telegraph Act, 1885, which mandates targeted surveillance, nor is it clear that such surveillance is being carried out on the occurence of a specific “public emergency” or in the interest of “public safety”. As such, the vagueness revolving around the question of whether the CMS undertakes targeted or mass surveillance means that its legality remains an equivocal matter.
As for the third argument, it is not clear how bypassing the nodal officers of TSPs will enhance citizen's right to privacy. While it may potentially be a good thing that nodal officers will not always be aware of whose information is being intercepted, that does not guarantee that those who do have access to such data will not abuse it. After all, the CMS appears to be largely unregulated and India lacks privacy legislation and all other adequate legal safeguards. Moreover, by bypassing the nodal officers of TSPs, the opportunity for unauthorised requests to be rejected will seize to exist. It also implies an increased centralisation of intercepted data which can potentially create a centralised point for cyber attacks. Thus, the argument that the CMS authority will monopolise the control over intercepted data does not appear reassuring at all. After all, who will watch the watchmen?
While the fourth argument makes a point about differentiating the provisioning and requesting entities with regards to interception requests, it does not necessarily ensure a complete check and balance, nor does it completely eliminate the potential for abuse. The CMS lacks adequate legal backing, as well as a framework which would ensure that unauthorised requests are not provisioned. Thus, the recommended chain of custody of issuing interception requests does not necessarily guarantee privacy protections, especially since a legal mechanism for ensuring checks and balances is not in place.
Furthermore, this argument states that the CMS authority will not have access to content data, but does not specify if it will have access to metadata. What's concerning is that metadata can potentially be more useful for tracking individuals than content data, since it is ideally suited to automated analysis by a computer and, unlike content data which shows what an individuals says (which may or may not be true), metadata shows what an individual does. As such, metadata can potentially be more “harmful” than content data, since it can potentially provide concrete patterns of an individual's interests, behaviour and interactions. Thus, the fact that the CMS authority might potentially have access to metadata appears to tackle the argument that the provisioning and requesting entities will be seperate and therefore protect individual's privacy.
The final argument appears to provide some promise, since the maintenance of a command log of all provisioning activities could potentially ensure some transparency. However, it remains unclear who will maintain such a log, who will have access to it, who will be responsible for ensuring that unlawful requests have not been provisioned and what penalties will be enforced in cases of breaches. Without an independent body to oversee the process and without laws which predefine strict penalties for instances of misuse, maintaining a command log does not necessarily safeguard anything at all. In short, the above arguments in favour of the CMS and which support the notion that it enhances individual's right to privacy appear to be inadequate, to say the least.
In contemporary democracies, most people would agree that freedom is a fundamental human right. The right to privacy should be equally fundamental, since it protects individuals from abuse by those in power and is integral in ensuring individual liberty. India may literally be the largest democracy in the world, but it lacks privacy legislation which establishes the right to privacy, which guarantees data protection and which safeguards individuals from the potentially unlawful interception of their communications. And as if that is not enough, India is also carrying out a surveillance scheme which is largely unregulated. As such, it is highly recommended that India establishes a privacy law now.
If we do the math, here is what we have: a country with extremely high levels of corruption, no privacy law and an unregulated surveillance scheme which lacks public and parliamentary debate prior to its implementation. All of this makes it almost impossible to believe that we are talking about a democracy, let alone the world's largest (by population) democracy! Therefore, if Indian authorities are interested in preserving the democratic regime they claim to be a part of, I think it would be highly necessary to halt the Central Monitoring System and to engage the public and the parliament in a debate about it.
After all, along with our right to privacy, freedom of expression and other human rights...our right to freedom from suspicion appears to be at stake.
How can we not be worried about the Central Monitoring System?
The Centre for Internet and Society (CIS) is in possession of the documents which include the information on the Central Monitoring System (CMS) as analysed in this article, as well as of the draft Rule 419B under the Indian Telegraph Act, 1885.
Bhutan's Google Apps
 Jan25 Vol5 Issue04_2014.pdf
—
PDF document,
4744 kB (4858629 bytes)
Jan25 Vol5 Issue04_2014.pdf
—
PDF document,
4744 kB (4858629 bytes)
New Document on India's Central Monitoring System (CMS) - 2
 Brief material about CMS etc
—
PDF document,
1116 kB (1143370 bytes)
Brief material about CMS etc
—
PDF document,
1116 kB (1143370 bytes)
UAS License Agreement Amendment regarding the Central Monitoring System (CMS)
 UAS License Agreement amendment regarding the CMS
—
PDF document,
1415 kB (1449307 bytes)
UAS License Agreement amendment regarding the CMS
—
PDF document,
1415 kB (1449307 bytes)
Video Games: A Case Study of a Cross-cultural Video Collaboration
This was published in a book on Palestinian art.
The rise of mobile media is heralding new forms of networked visualities. These visualities see place, politics and images entangled in new ways: what can be called ‘emplaced visuality’. In the images disseminated globally of citizen uprising such as the Arab Spring, it was mobile phones that provided the frame and context for new forms of networked visual politics. In the growth in networked photo apps such as Instagram and Hipstamic, how, when and why we are representing a relationship between place and co-presence is changing. No longer the poorer cousin to professional cameras, camera phones have lead the rise of do-it-yourself (DIY) aesthetics flooding mainstream and subcultural media cultures. In networked visuality contexts such as YouTube and Flickr, the aesthetic of what Burgess has called ‘vernacular creativity’[1] has become all-pervasive—so much so that even mainstream media borrows the DIY style.
Now, with locative media added into the equation, these visualities are not only networked but also emplaced—that is, entangled within the temporal and spatial movements of everyday life.[2]
Emplaced visualities represent a new relationship between place (as a series of what Doreen Massey calls ‘stories so far’)[3] co-presence, subjectivity and visuality. This phenomenon is impacting upon video art. In this chapter we reflect upon how mobile media visualities are impacting upon a sense of place and displacement. With the added dimension of Big Data and location-based services (like Google Maps and Facebook Places) now becoming part of the everyday informational circuits, how a sense of place and privacy is experienced and represented is changing. This phenomenon is apparent in the Palestinian cross-cultural video project called Al Jaar Qabla al Daar (The Neighbour before the House) as we will discuss in detail later in this chapter.
With its history of displacement and disapora, Palestinine’s role in contemporary art is increasingly becoming pivotal. This is especially the case with video art as a key medium for reflecting upon representations of place and movement. When we think of Palestinan video art the first artist we think of is Mona Hatoum. Hatoum was a poineer in so many ways. In particular, she gave voice to Arab women. Her work unsetttled the poetics of the everyday by evoking a sense of displacement and entanglement. While born in Beirut of Palestinan parents and then moving to London, she never identified as Lebanese. Despite never living in Palestinian, Hatoum was like a number of Palestinian refugees in Lebanon post 1948 who were never able to gain Lebanese identity cards. Unsurprisingly, Hatoum’s experiences of exile permulate her work. In particular, exile, politics and the body have played a key role. This is epitomised in her iconic Measures of Distance (1988) whereby Hatoum superimposes images of her mother having a shower with letters by her mum written in Arabian.
However, Hatoum is not the only artist representing the oevre of Palestinian video art. Over the last two decades—with the rise of mobile media affording easy accessibility to new media tools and networked contexts like YouTube—a new breed of video artists has arisen. An example is Navigations: Palestinian Video Art, 1988 to 2011 (curated as part of the Palestine Film Festival) that explored artists working in Palestine and the diaspora over nearly a quarter of a century. Unsurprisingly, motifs of diaspora and displacement feature throughout the fifteen works by Hatoum, Taysir Batniji, Manar Zoabi, Larissa Sansour and Khaled Jarrar to name a few. In Navigations: Palestinian Video Art key themes include ‘mobility and fluidity: the virtual and the real, the past and the future, the spectacular and the quotidian, the near and the far’.
Another example of an event promoting Palestinian video art is the /si:n/ Festival of Video Art & Performance. Consisting of performances, video installations, lectures, talks, and workshops in various venues all over the West Bank and includes artists from all over the world. The name /si:n/ is meant to linked the words ‘scene’ with ‘seen’ and has been seen as making an innovative context for video artists to share and collaborate in public venue. With themes such as ‘poetical revolution comes before political revolution’, the /si:n/ Festival provides a context that reflects upon exile and place in one of the most contested and politucal spaces, the West Bank. Beginning in 2009, the /si:n/ Festival became the first festival of video art in Palestine.
Given this rich tapestry of video art emerging in Palestine, in this chapter we explore the relationship between emergent mobile visualities, diaspora and place through a specific project called The Neighbour before the House. A cross-cultural video collaboration between Indian artists Shaina Anand, Ashok Sukumaran and Nida Ghouse, with Palestinian and Israeli artists Mahmoud Jiddah, Shereen Brakat and Mahasen Nasser-Eldin, The Neighbour before the House is a video art project that explores quotidian practices of life in a ‘post-surveillance society’. The Neighbour before the House is set in the context of the much contested territories and the relentless re-occupation and re-appropriation of East Jerusalem. Working with cheap surveillance technologies which have become such a ubiquitous part of the landscape of East Jerusalem, the artists use a PTZ (pan-tilt-zoom) security camera to inquire into the affective dimensions of ‘mobile’ life in the time of turbulent politics. The images that they capture look at jest, memory, desire and doubt, as fragile conditions of trust and life shape the everyday experiences of the region. The camera is given to the residents of a neighbourhood torn asunder by political strife and conflicts, asking them to search for the nugget of truth or morsel of thickness in the otherwise familiar flatness of walls and closed doors, which have been completely depleted of all depth because of the increased distance in the social relations.
The images eschew the tropes of traditional documentary making by and adopting the grainy, lo-res, digital non-frame, DIY aesthetics constantly in search of an image that might become the site of meaning making, but increasingly only capturing the mundane, the inane, the opaque and the evanescent. The image leads the commentary. The live camera operator’s interest and experience shape the image, rendering the familiar or the insignificant as hugely affective and evocative. The project further initiates a dialogue between the neighbours—both from across the contested zones, but also from across picket fences and walls of surveillance—by introducing the images to them, by inviting them to capture the images, and instil in them, the narratives of hope, despair, nostalgia, memory, loss, love, and longing.
The Neighbour before the House reflects upon the relationship between between art, technologies of visual reproduction and political strife. Moving away from the documentary style that has been popular in capturing the ‘real’, The Neighbour before the House refigures the temporality and spatiality through new affective and metaphorical tropes, playing with the tension between the presence of surveillance technologies and the familiarity of these images that breeds new conditions of life and living, trust and belonging, safety and threat, for people in Palestine. In the process, it introduces key questions to the role of the artist, the function of art, the form of video art practice, and the new negotiations that digital video apparatus introduce to the art worlds, beyond the now main-stream ideas of morphing, digitization, remixing etc.
Moreover, The Neighbour before the House reflects upon a shift away from the dominant network society paradigm and towards more contingent and ambivalent mirconarratives of camera phone practices. It toys with the DIY ‘banality’ aesthetics of camera phones in order to consider the ways in which place is overlaid with different types of information—electronic, geographic, psychological and metaphoric. On the one hand, The Neighbour before the House evokes network society metaphors. On the other hand, it suggests a move away from this paradigm and towards a politics of both ‘emplaced’ and displaced visuality. In order to discuss this transformation of the relationship between image, place and information from network society metaphors towards ‘emplaced’ visualities we firstly describe The Neighbour before the House before then reflecting upon a few key themes the project explores: that is, the movement of the networked society to emplaced visualities and the rise of the politics of the phoneur.
The Neighbour before the House 2012): A case study
As aforementioned, The Neighbor before the House is a collaborative video project between Indian, Israeli and Palestenian artists that appropriates, critically responds and insightfully rearranges the notion of art, politics and digital video technologies in its exploration of everyday practices of life in critical times in a networked post-surveillance society. The Neighbor before the House equips eight Palestenian families from East Jerusalem to be in control of PTZ (Pan Tilt Zoom) surveillance cameras mounted at strategic locations in the city, to observe the live feed on their TV sets, recording their reactions and live commentaries at what they see. Here the Big Brother, and its contemporary Big Data, is inverted through everyday citizens being given the omnipresent eye. It plays on the idea of the neighbour being both a friendly eye and when this watching shifts from being benevolent to malevolent.
As the artists write, ‘this footage shot with a security camera, takes us beyond the instrumental aspects of surveillance imaging, introducing us to the architecture of a deliberate and accelerated occupation of a city.’ Here the city is rendered into a cartography of informational circuits. Exploiting the conditions of networked spectacle, the project attempts to remap the real and the everyday through ‘inquisitiveness, jest, memory, fear, desire and doubt’. They use the surveillance cameras—symbols of suspicion and fear—to catalyse stories from Palestenians in different neighbourhoods about what can be seen: ‘messianic archeological digs; Israeli settlement activities; takeovers of Palestenian properties; the Old City, the Wall and the West Bank,’ among other mundane and marvellous details of living life in those precarious conditions.
Through the inversion of the politics of survellience from the Big Brother to the ubiquitous neighbour, The Neighbor before the House provides a rich, evocative and non-representational history of living in East Jerusalem. The networked media spectacles which have come to stand-in for the complex geo-political struggles of the region are displaced. As the low-res cameras reduce the deep geography into an alien flatness on the TV screens, as the camera captures glimpses of what could have been, records traces of blurred movements which require discussions and debates about their possible meaning, and engages the families to communicate their hopes, fears, desires and doubts, the art project also signals us to the new forms, functions and role of video art. Rather than the media event or spectacle,
The Neighbor before the House provides the micronarrative gestures of the everyday. The ways in which the place is a tapestery of subjectivities and experiences, not just a media spectacle.
As artist Shaina Anand mentions in an interview with Shah, this is a new kind of storytelling, where,
… a lot of the practice actually removes the filmmaker, the director, the auteur, and also therefore the cameraman, and also the lens... and offers these possibilities and privileges— of this look and gaze and all—to the subjects themselves[4]
And as the lens makes itself invisible, it also gives new importance to the apparatus of surveillance, seeing and its incorporation in our lives. As Florian Schenider mentions in the introduction to the project, the house upon which the camera is mounted, itself becomes a tripod made of stones. Instead of thinking of the video apparatus as out there, the private conditions of the home, the histories of the family, their relationships with neighbours and communities that they have lost, and strangers that they have inherited, all become the defining circumstances of this new crisis.
Borrowing from a Quranic saying, Al Jaar Qabla Al Daar, which is close to the idea of ‘loving they neighbour’ it explores how the presence of new digital video technologies establishes difference, distance, alienation, proximity, curiosity and surveillance which is not merely a function of governmental structures but also a condition of gamification and everyday engagement for the families in East Jerusalem. For the artists, this also takes up another connotation of ‘checking out your neighbour before you buy the house’ suggesting establishing bounded similarities to seek comfort. The edited footage of the video shows how and when the users got in control of the keyboard and a joy-stick, panning, tilting and zooming the camera, watching the live feeds on their Television sets as they speak live over the footage. These commentaries are personal as they are affective. Sometimes the commentary leads the person to probe the image, deeper, trying to find a meaning that can no longer be supported by the hyper-pixelated image on their screen, but becoming a site through which memories and interpretations
get generated. What begins as a playful probe soon takes up sinister shades, as some generate narratives of loss and death. Others take the opportunity to spy on the new settlers who have sometimes taken over their older houses, wondering what changes they are making to what was their own. There is a sense of rawness and urgency, as they look back, with fear, and anger, but also with resignation at the houses that they were evicted from, and the semblance of life that they can spot from their remote presence.
The final 5 cuts that the artist produce, give us a deep and evocative insight into geography, temporality, and the ways in which we can re-appropriate the network spectacle to look at things that are often forgotten, dropped out of, or rendered invisible in the neat and clean lines of network models and diagrams. The ‘footage’ quality of the probes, the long dwellings on insignificant images, and the panoptican nature of video as witness, video as spy, and video as affective engagement with territories and times that are lost, all give a new idea of what the future of video art would be like. Instead of looking at a tired old Foucauldian critique of surveillance, The Neighbor before the House posits the question of ‘Who watches the watchman?’ in ways that are both startling and assuring.
Visualising the Politics of the Network
One of the key themes of The Neighbour before the House is the changing role of the network society—especially in an age of Big Data and locative-based services (LBS)—whereby privacy and surveillance come to the forefront. The network society has often been cited as one of the defining frameworks of our heavily mediated times. From theorists such as Barry Wellman and Manuel Castells, the network metaphor has burgeoned in parallel with the all-pervasive rise of Information and Communication Technologies (ICTs) globally. According to Lee Raine and Wellman in Networked, the ‘new social operating systems of networked individualism liberates us from the restrictions of tightly knit groups.’[5]
Raine and Wellman argue that there has been a ‘triple revolution’: the rise of social networking, the capacity of the internet to empower individuals, and the always-on connectivity of mobile devices’.[6]
The ability of networks to explain a range of human personal and social relationships has afforded it great explanatory power, where everything (and hence, by association, everybody) can be understood and explained by the indexicalities and visual cartographies that networks produce. The network is simultaneously, and without any sense of irony, committed to both, examining sketchiness and producing clarity of any phenomena or relationality. The network presumes an externality which can be rich, chaotic and complex and proposes tools and models through which that diverse and discrete reality can be rendered intelligible by producing visualisations.
These visualisations are artefacts—in as much as all mapping exercises produce artefacts—and operate under the presumption of a benignity devoid of political interventions or intentions. The visualisations are non-representational, in terms that they do not seek to reproduce reality but actually understand it, and thereby shaping the lenses and tools to unravel the real nature of the Real. In this function, the network visualisations are akin to art, attaining symbolic value and attempting to decode a depth that the network itself defies and disowns, simulating conditions of knowing and exploring, emerging as surrogate structures that stand in for the real. Thus the rich set of actions, emotions, impulses, traces, inspirations, catalysts, memories, etc. get reified as transactions which can be sorted in indices, arranged in databases, and presented as an abstract, symbolic and hyper-visual reality which can now be consumed, accessed and archived within the network, thus obfuscating the reality that it was premised upon.
This phenomenon is what Shah calls the spectacle imperative of the network. Especially with the proliferation of ubiquitous image and video recording digital devices, this ability to create subjective, multiple, fractured spectacles that feed into the network’s own understanding of itself (rather than an engagement with a reality outside) has become the dominant aesthetic that travels from Reality TV programming to user generated content production on video distribution channels on the internet. This networked spectacle, without a single auteur or a concentrated intention—so the videos from the Arab Spring on YouTube, for example, range from small babies in prams to women forming barricades against a marching army, and from people giving out free food and water to acts of vandalism and petty thefts—has become the new aesthetic of video interaction, consumption and circulation. It invites an engagement, divesting our energies and attentions from the physical and the political, to the aesthetic and the discursive. Which is to say that when we consume these spectacles (or indeed, produce them, not necessarily only through the images but also through texts), we produce a parallel universe that demands that we understand the world ‘out there’ through these cultural artefacts which require an immense amount of decoding and meaning making. The network, in its turn, offers us better and more exhaustive tools of mining and sifting through this information, sorting and arranging it, curating and managing it, so that we build more efficient networks without essentially contributing to the on-the-ground action.
This peculiar self-sustaining selfish nature of the network, to become the only reality, under the guise of attempting to explain reality, is perhaps the most evident in times and geographies of crises. Where (and when) the conditions of politics, circumstances of everyday survival, and the algebra of quotidian life becomes too precarious, too wearisome, too unimaginable to cope with, the network spectacle appears as both the tool for governance as well as the site of protest. Hence, the same technologies are often used by people on different sides of the crises, to form negotiations and get a sense of control, on a reality that is quickly eluding their lived experiences. Surveillance cameras storing an incredible amount of visual data, forming banal narratives of the everyday, appear in critical times and geographies as symbols of control and containment, by authorities that seek to establish their sovereignty over unpredictable zones of public life and dwelling. The gaze of the authority is often criss-crossed by the cell-phone, the webcam, the tiny recording devices of everyday life that people on the streets and in their houses use, to record the nothingness of the crisis, the assurance of normalcy and the need to look over the shoulder and beyond the house, to know that whether or not god is in the heavens, all is well with the world.
The Place of the Visual: Towards a theory of emplaced visuality
However, with the rise of mobile media and its micronarrative capacity, the politics of network, and its relationship to a sense of place changes. Far from eroding a sense of place in the growing unboundness of home, mobile technologies reinforce the significance locality.[7] Mobile media also signal a move away from earlier depictions of the network society. Through the growth in camera phone practices overlaid with location-based services, we see new forms of visuality that reflect changing relations between place and information. With the rise of technologies in an increasingly mobile—physically and technologically—place has become progressively more contested. As Rowan Wilken and Gerard Goggin note in Mobile Technologies and Place, place is one of the most contested, ambiguous and complex terms today.[8] Viewing it as unbounded and relational, Wilken and Goggin observe, ‘place can be understood as all-pervasive in the way that it informs and shapes everyday lived experience—including how it is filtered and experienced via the use of mobile technologies’.[9] As social geographer Doreen Massey notes, maps provide little understanding into the complex elusiveness of place as a collection of ‘stories-so-far’:
One way of seeing ‘places’ is as on the surface of maps… But to escape from an imagination of space as surface is to abandon also that view of place. If space is rather a simultaneity of stories-so-far, then places are collections of those stories, articulations within the wider power-geometries of space. Their character will be a product of these intersections within that wider setting, and of what is made of them… And, too, of the non-meetings-up, the disconnections and the relations not established, the exclusions. All this contributes to the specificity of place.[10]
For anthropologist Sarah Pink, place is increasingly being mapped by practices of emplacement.[11] With location based media like Google Maps and geotagging becoming progressively part of everyday media practice, how place is imagined and experienced across geographic, psychological, online and offline spaces is changing. This impacts upon the role of ethnography and its relationship to geography and place. As Anne Beaulieu notes, ethnography has moved from co-location to co-presence.[12] In this shift, we see the role of ethnography to address the complex negotiations between online and offline spaces growing.
In The Neighbour before the House, we are made to consider the changing role of visuality in how place is experienced and practiced. By deploying a surveillant and multivalent gaze, The Neighbour before the House asks us to reconsider privacy and surviellance in an age of locative media. The rise of the network society has witnessed numerous tensions and ambivalence, especially around the the relationship between agency, information and place. This is epitomised by the second generation camera phones practices whereby with the added layer of LBS—where and when images were taken—becomes automatic by default. Whereas first generation of camera phone practices noted gendered differences.[13] through LBS, these differences take on new dimensions—particularly in terms of its potential ‘stalker’ elements.[14] While notions of privacy differ subject to socio-cultural context, LBS do provide more details about users and thus allow them to be victims of stalking (Cincotta, Ashford, & Michael 2011).
The shift towards second generation camera phone images sees a movement away from networked towards emplaced visualities (Pink & Hjorth 2012; Hjorth 2013; Hjorth & Arnold 2013). On the one hand, this overlaying of the geographic with the social highlights that place has always mattered to mobile media (Ito 2002; Hjorth 2005). Far from eroding place, mobile media amplify the complexities of place as something lived and imagined, geographic and yet psychological. LBS enable mobile media users to create and convey more complex details about a locality. On the other hand, LBS create new motivations for narrating a sense of place and the role of amateur and vernacular photography.
Shifts in contemporary amateur photography highlight the changes in how place, co-presence and information is navigated, performed and represented. This issues are particularly prevalent in contested location like Palestine. Last century it was the Kodak camera that epitomized amateur photography and played an important role in normalizing notions of the family as well as ritualizing events such as holidays.[15]
As Lisa Gye notes, personal photography is central to the process of identity formation and memorialization.[16] The shift towards camera phones not only changes how we capture, store, and disseminate images but also has ‘important repercussions for how we understand who we are and how we remember the past’.[17]
Moreover, with the rise in possibilities for sharing via social media like microblogs and Twitter, camera phone photography not only magnifies UCC, but also provides filters and lenses to enhance the “professional” and “artistic” dimensions of the photographic experience.[18]
For Daniel Palmer, smartphone photography is distinctive in various ways, with one key feature being the relationship between touch and the image in what he calls an ”embodied visual intimacy” (2012: 88). With the rise of high quality camera phones, along with the growth in distribution services via social and locative media, new forms of visuality are emerging (Pink & Hjorth 2012). The added dimensions of movement and touch becoming important features of the camera phone with the emphasis on networked is shifting to “emplaced” visuality. Images as emplaced in relation to what human geographer Tim Ingold has called a “meshwork” and entanglement of lines (2008). Images themselves are part of such lines as they are inextricable from the camera and person who took them. In this sense camera phone images are not simply about what they represent (although they are also about that) but are additionally about what is behind, above, below, and to either side.
By using different smartphone photo apps, respondents tried to inscribe a sense of place with emotion. This practice is what anthropologist Sarah Pink identifies as the “multisensorality of images.” That is, they are located in “the production and consumption of images as happening in movement, and consider them as components of configurations of place” (Pink 2011: 4). Drawing on Tim Ingold’s conceptualization of place as “entanglement” (Ingold 2008), Pink notes, “Thus, the ‘event’ where photographs are produced and consumed becomes not a meeting point in a network of connections but an intensity of entangled lines in movement… a meshwork of moving things” (Pink 2011: 8).
While the surveillant eye of Big Brother now takes the form of Big Data, the emplaced nature of camera phone images can help to contribute to a changing relationship between performativity, memory and place that is user-orientated. Rather than operating to memorialize place, camera phone practices, especially through LBS networks, are creating playful performances around the movement of co-presence, place and placing (Richardson & Wilken 2012). As noted elsewhere, Pink and Hjorth argue that camera phone practices are highlighting a move away from the network society towards emplaced visualities and socialities (2012). Emplaced visuality means understanding camera phone practices and the socialities that create and emerge through them in ways corresponding with non-representational (Thrift, 2008) or ‘more-than-representational’ approaches in geography which according to Hayden Lorimer encompass:
… how life takes shape and gains expression in shared experiences, everyday routines, fleeting encounters, embodied movements, precognitive triggers, affective intensities, enduring urges, unexceptional interactions and sensuous dispositions (Lorimer, 2005: 84).
Thus we see camera phone photography as a part of the flow of everyday life, an increasingly habitual way of being that is sensed and felt (emotionally and physically). Yet, because camera phone photography involves the production and sharing of images, it also compels us to engage with the relationship between the representational and the non-representational. Emplaced visualities see images as embedded with the movements of everyday life. Tim Cresswell has suggested that we consider ‘three aspects of mobility: the fact of physical movement—getting from one place to another; the representations of movement that give it shared meaning; and, finally, the experienced and embodied practice of movement’ (Cresswell, 2010: 19). These three aspects of mobility are deeply interwoven and entangled. In camera phone photography the experience and representation of camera phone photography is enacted in the ‘flow’ of everyday life at the interface where digital and material realities come together. These emplaced visualities are often abstracted through the mechanics of Big Data mega surveillance. But as The Neighbour before the House demonstrates, the perpetual movement of emplaced visualities is in sharp contrast with the unmoving, omipresent Big Data eye.
This contrast between the moving and unmoving, micro and macro information overlaid onto place can also be reflected as part of the shift from the flâneur to the phoneur. The notion of mobility—as a technology, cultural practice, geography and metaphor—has impacted upon the ways in which twenty-first century cartographies of the urban play out. Through the trope of mobility, and immobility, rather than overcoming all difference and distance, the significance of local is reinforced. While nineteenth-century narrations of the urban were symbolised by the visual economics of the flâneur, the twenty-first century wanderer of the informational city has been rendered what Robert Luke calls the phoneur. [19] The conceptual distance, and yet continuum, between the flâneur and the phoneur is marked by the paradigmatic shift of the urban as once a geospatial image of, and for, the bourgeoisie, as opposed to the phoneur which sees the city transformed into informational circuit in which the person is just a mere node with little agency. Beyond dystopian narrations about the role of technology in maintaining a sense of intimacy, community and place, we can find various ways in which the tenacity of the local retains control. In particular, through the tension between mobile media and Big Data, we can see how the local and the urban can be re-imagined in new ways.
The flâneur (or the wanderer of the modern city), best encapsulated by German philosopher Walter Benjamin’s discussion of Baudelaire’s painting, has been defined as an important symbol of Paris and modernity as it moved into nineteenth century urbanity. Thanks to the restructuring of one third of the small streets into boulevards by Baron Hausmann, Paris of the nineteenth century took a new sense of place and space.
Luke’s phoneur, on the other hand, is the ‘user’ as as part of the informational network flows constituting contemporary urbanity. If the flâneur epitomised modernism and the rise of nineteenth-century urban, then for Luke, the phoneur is the twenty-first-century extension of this tradition as the icon of modernity. As Luke observes, in a networked city one is connected as part of circuit of information in which identity and privacy is at the mercy of system. The picture of the urban city today painted by Luke is one in which the individuals have minimal power in the rise of corporate surveillance.
Neighbour before the House problematises Luke’s dystopian view of the phoneur. The picture painted by Neighbour before the House is much more ambivalent. However it does make the audience reflect upon the changing nature of surveillance in an age of Big Data.[20]
These tensions around the dystopian phoneur and a more embodied and emplaced version can be found running as an undercurrent in the work of Neighbour before the House.
Conclusion
In this chapter we have explored the cross-cultural video collaboration, The Neighbour before the House, to consider the changing relationship between a sense of place, information and the politics of visuality. As we have suggested, with the rise of location-based camera phone practices and Big Data we are seeing new forms of visuality that are best described as emplaced rather than networked. The notion of emplaced reflects some of the tensions around contemporary representations of mobility and movement, particularly prevalent in the often displaced and diasporic experiences of Palestine.
Filmed in Palestine,The Neighbour before the House explores the notion of place as entangled and embedded at the same time as displaced through the rise of ICTs. By providing some of the paradoxes and ambivalences surrounding contemporary media practices and its relationship between information and place, it allows for a space for reflection and contemplation about the surveillence and privacy.
[1]. Jean Burgess, Vernacular creativity and new media (Doctoral dissertation), 2007. Retrieved from http://eprints.qut.edu.au/16378/
[2]. Sarah Pink and Larissa Hjorth Emplaced Cartographies: Reconceptualising camera phone practices in an age of locative media’, Media International Australia, 145 (2012): 145-156.
[3]. Doreen Massey
[4]. Shaina Anand interviewed by Nishant Shah, December 2012.
[5]. Raine, L. and B. Wellman 2012, Networked, Cambridge, Mass, MIT Press.
[6]. Ibid.
[7]. Mizuko Ito, ‘Mobiles and the Appropriation of Place’. Receiver 8, 2002, (consulted 5 December 2012) http://academic.evergreen.edu/curricular/evs/readings/itoShort.pdf ; Hjorth, L. (2005) ‘Locating Mobility: Practices of Co-Presence and the Persistence of the Postal Metaphor in SMS/MMS Mobile Phone Customization in Melbourne’, Fibreculture Journal, 6, (consulted 10 December 2006) http://journal.fibreculture.org/issue6/issue6_hjorth.html.
[8]. Rowan Wilken and Gerard Goggin, ‘Mobilizing Place: Conceptual Currents and Controversies’, in R. Wilken and G. Goggin (Eds) Mobile Technology and Place, New York, Routledge, 2012, pp. 3-25 (5).
[9].Ibid 6.
[10]. Doreen Massey,For Space, London, Sage, 2005 (130).
[11]. Sarah Pink, Doing Sensory Ethnography, London, Sage, 2009.
[12]. Anne Beaulieu, ‘From Co-location to Co-presence: Shifts in the Use of Ethnography for the Study of Knowledge’. Social Studies of Science, 40 (3) 2010: June. 453-470.
[13]. Dong-Hoo Lee, ‘Women’s creation of camera phone culture’. Fibreculture Journal 6, 2005, URL (consulted 3 February 2006) http://www.fibreculture.org/journal/issue6/issue6_donghoo_print.html; Larissa Hjorth, ‘Snapshots of almost contact’. Continuum, 21 (2) 2007: 227-238.
[14]. Alison Gazzard, ‘Location, Location, Location: Collecting Space and Place in Mobile Media’. Convergence: The International Journal of Research into New Media Technologies, 17 (4) 2011: 405-417.
[15]. Lisa Gye, ‘Picture this: the impact of mobile camera phones on personal photographic practices,’ Continuum: Journal of Media & Cultural Studies 21(2) 2007: 279–288.
[16]. Ibid 279.
[17]. Ibid 279.
[18]. Søren Mørk Petersen,Common Banality: The Affective Character of Photo Sharing, Everyday Life and Produsage Cultures, PhD Thesis, ITU Copenhagen.
[19]. Robert Luke, ‘The Phoneur: Mobile Commerce and the Digital Pedagogies of the Wireless Web’, in P. Trifonas (ed.) Communities of Difference: Culture, Language, Technology, pp. 185-204, Palgrave, London, 2006.
[20]. Sites such as www.pleaserobme.com, that seek to raise awareness about over-sharing of personal data, highlight not only the localised nature of privacy but also that privacy is something we do rather than something we possess.
MAG Notice
 MAG-meeting-notice.pdf
—
PDF document,
161 kB (165692 bytes)
MAG-meeting-notice.pdf
—
PDF document,
161 kB (165692 bytes)
Data Privacy Day, Chennai
 TACTiCS Symposium - Data Privacy 2014 - Program.pdf
—
PDF document,
282 kB (288831 bytes)
TACTiCS Symposium - Data Privacy 2014 - Program.pdf
—
PDF document,
282 kB (288831 bytes)
February 11: The Day We Fight Back Against Mass Surveillance
The expanding scope and extent of massive data collection and surveillance undertaken by bodies like the USA’s National Security Agency compromises our privacy and stifles our freedom of speech and expression in its most vital public spheres, affecting the civil liberties of citizens of countries all across the world.
The previous year has been a watershed year for reclaiming the internet as a free and open space, primarily through the exposure of the unwarranted systems of surveillance that threaten it, by whistle-blowers like Edward Snowden and WikiLeaks. Despite all these efforts, they have only managed a dent in the surveillance regimes, which continue unbridled, with the protection of the state and the surveillance industry. The future of a free internet depends upon the systematic challenge of these programs by the millions of internet users they affect.
February 11, 2014 is the day we fight back against mass surveillance. Organized by the Electronic Frontier Foundation, and supported by thousand of organizations like Mozilla and the Centre for Internet and Society, on this day of action, citizens around the world will demand an end to these programs that threaten the freedom of the internet. You can support this cause by signing and supporting the 13 Principles (International Principles on the Application of Human Rights to Communications Surveillance), and contacting your local media, petitioning your local legislators and telling your friends and colleagues about the topic. Publicizing the movement and creating a buzz around it will help spread the message to many others across the internet. Do anything that will make the fight more visible and viable, such as organizing or attending public lectures, or creating tools or memes or art to spread information. For more ways in which you can contribute, and more information on the event, visit the website.
The users of the internet deserve a free and open internet and deserve and end to mass surveillance. If we can make enough noise, make enough of an impact, we can greatly bolster the movement for reclaiming the internet.
The Internet Way
Click to download the file (PDF, 2436 Kb). Dr. Nishant Shah's review can be found on page 16.
The Age of Amazon’ is not just the title of a book, it is a retrospective on the history of e-commerce as well as a prophecy for the shape of things to come. In his meticulously reported book, Brad Stone takes us through the roller coaster ride of the ‘Everything Store’ that Amazon has become, building a gripping tale of an idea that has become synonymous to the world of online shopping in just over two decades.
The book reads well as a biopic on the visionary lunacy of Jeff Bezos, the founder of Amazon, as well as a gripping tale of how ideas grow and develop in the digital information age. Stone is an expert storyteller, not only because of his eye for the whimsical, the curious and the enchantment of the seemingly banal, but also because of his ability to question his own craft.
At the very outset, Stone warns us that the book has been compiled through workers at employee, but not Bezos himself. This helps Stone separate the maker from the brand — unlike Steve Jobs who became the cult icon for Apple, Bezos himself has never become the poster child of his brand, allowing
Amazon to become not only an everything store but everybody store. But it means that Stone’s task was to weave together the personal biography of Bezos, his dramatic journey through life with the tumultuous and adventurous inception and growth of Amazon, and his skill lies in the meeting of the twines, which he does with style, ease and charm.
One of the easiest accusations to throw at a book like this is to state that it reduces the murky, blurred, messy and incoherent set of events into a narrative that establishes causes and attributes design and intention where none existed. However, Stone was confronted with the idea of ‘Narrative Fallacy’ — a concept coined by Nassim Nicholas Taleb in his Black Swan, referring to the tendency of human beings to reduce complex phenomenon to “soothing but oversimplified stories”. In fact, the challenge to not reduce the book to a series of connected anecdotes was posed by Bezos when Stone pitched the book to him. And what has emerged is a book about accidents, serendipity, risk, redundancy, failure charting the ineffable, inscrutable and inexplicable ways in which digital technologies are shaping the worlds we live in.
With the rigour and journalistic inquiry that Stone has displayed in his regular writings in The Businessweek, The Everything Store has stories which are as memorable as they are unexpected. Stone does a fantastic job of charting Bezos’ life — from tracking down the lost father who had no idea what his son, who he had abandoned at age three, has become, to the chuckleworthy compilation of Bezos’ favourite quotes (Stone calls it his ‘greatest hits’), the book is filled with pointed and poignant observations and stories that give us an idea of the extraordinary life of Jeff Bezos. But unlike the expected character creation of a mad genius, what you get is the image of a man who lived in contradictions: wedded to his internal idea of truth but also ruthless in his business policies which were predatory and competitive to say the least; a businessman who once wrote a memo titled ‘Amazon.love’ about how he wanted a company to be “loved not feared” but also used the metaphor of a “cheetah preying on the gazelles” in its acquisition of smaller businesses; a man who thought of himself as a “missionary rather than a mercenary” and yet built a business empire that embodies some of the most discriminatory, exploitative and stark conditions of adjunct, adhoc, underpaid and contract-based labour of our precariously mobile worlds.
Stone is masterful as he segues from Bezos’ personal life and ambitions into the monomaniacal and turbulent trajectory of Amazon. Amazon is not a simple success story. It tried and failed at many things, but what remains important is how, it failed at the traditional way of doing things and succeeded at the internet way of thinking. So when Amazon failed, it was not a failure to succeed, but a failure that resulted because the infrastructure needed to make it succeed was not yet in place. Stone’s narrative that effortlessly takes us through the economics, trade, policies, regulation, administration and struggles of Amazon, shows how it was a company that had to invent the world it wanted to succeed in, in order to succeed. In many ways, the book becomes not only about Amazon and its ambitions to sell everything from A-Z, but about how it built prototypes for the rest of the world so that it could become relevant and rule.
But the book is not a Martin-Scorsese-type homage to the scoundrel or the villain. While it is imbued up and spit you out. And if you are good, he will jump on your back and ride you into the ground.” Or as Stone himself suggests, that is the way the company is going to grow “until either Jeff Bezos exits the scene or no one is left to stand in his way”. This policy of taking everything from its employees and channelling it to the relentless growth of the company accounts for not only the high attrition rate of top executives but also the growing controversies about work and labour conditions in Amazon warehouses and on-the-ground delivery services.
Stone’s book does not go into great detail about the new work force that companies like Amazon produce — a work force that is reduced to being a cog in a system, performing mechanical tasks, working at minimal wage, and without the protections that are offered to the white collar high-level technology executives that are the popup children of the digital trade. Stone reminds us that behind the incredible platform that Amazon is, is a massive physical infrastructure which almost reminds us of the early industrial days where the labourer was in a state of exploitation and precariousness. And even as we celebrate the rise of these global behemoths, we might forget that behind the seductive interfaces and big data applications, that under the excitement of drone-based delivery systems and artificial intelligence that will start delivering things even before you place the order, is a system that pushes more and more workers in unprotected and exploitative work conditions.
All in all, The Everything Store is a little bit like Amazon itself. It is a love story of a man with his ideas, and how the rest of the world has shifted, tectonically, to accommodate these eruptions. In its historical retrospective, it shows us the full scope of the ideas and possibilities that inform Amazon, and thus the future that it is going to build for us. And with masterful craftsmanship, Brad Stone writes that it is as much about the one man and his company, as it is about the physical and affective infrastructure of our rapidly transforming digital worlds.
Biblio Review File
 Biblio Jan-Feb2014.pdf
—
PDF document,
2436 kB (2495370 bytes)
Biblio Jan-Feb2014.pdf
—
PDF document,
2436 kB (2495370 bytes)
MAG Meeting Notice 2014
 Meeting Notice (MAG).pdf
—
PDF document,
232 kB (237603 bytes)
Meeting Notice (MAG).pdf
—
PDF document,
232 kB (237603 bytes)
MAG Order
 MAG - ORDER.pdf
—
PDF document,
824 kB (844396 bytes)
MAG - ORDER.pdf
—
PDF document,
824 kB (844396 bytes)
Counter Surveillance Panel: DiscoTech & Hackathon (Flyer)
 Invite_CIS_MIT-2.pdf
—
PDF document,
287 kB (294119 bytes)
Invite_CIS_MIT-2.pdf
—
PDF document,
287 kB (294119 bytes)
Calcutta High Court Strengthens Whistle Blower Protection
In the absence of any law for the protection of whistle-blowers in the country, exposing the rampant corruption in our public institutions has become a hazardous occupation, with reports of threat and intimidation and even incidents of murder of whistle-blowers commonplace.[1] With the Whistle blower’s Protection Bill in abeyance and without any strict laws protecting the identities of the whistle-blowers who challenge such a corrupt system, even the mechanisms like the Right to Information Act which are meant to safeguard against systemic abuse and ensure transparency are being severely undermined.
For this reason, the Calcutta High Court’s affirmation of whistle-blowers’ privacy and identity protection is an important development. Through its order on the 20th of November, 2013, the Calcutta High Court held that for the purposes of section 6(2), which requires an application to the Public Information Officer to provide contact details of the applicant, it is sufficient in such application to disclose only the post-box number of the applicant. The court directed the Government to accept RTI applications without personal details or detailed whereabouts, when a post-box number or sufficient detail has been provided to establish contact between the whistle-blower and the authority. However if a public authority has any difficulty contacting the applicant through the Post Box No. the applicant may be asked to provide other contact details. The court further directed that personal details of applicants are not to be posted on the authorities’ websites.
The order, which was notified by the Government last week, ensures to some extent the protection of a whistle-blowers identity, and reduces the chances of the RTI being undermined by threats or acts of violence by those who are a part of the corrupt system, against persons exercising their right to information. However, its implementation is liable to be contingent on the authorities’ interpretation of when it would be “difficult” to establish contact between the authority and the applicant. Certain practical difficulties could also undermine the actual impact of the order, such as the fact that many applications are sent through registered or speed post, which cannot be mailed to a post-box number, especially since ordinary post cannot be tracked online like speed or registered post.[2]
Developing a system in which ordinary citizens do not have to fear retaliation for exposing corruption requires a comprehensive legislation protecting whistle-blowers identities and ensuring data security. However, the important message this judgement sends out is that the judiciary is still committed to protecting whistle-blowers, in lieu of the government’s actions. This is a particularly important stance taken by the Court, considering the Supreme Court in the past has refused to frame guidelines for whistle-blower protection, citing the imperative in enacting a whistle-blower legislation to be the Parliament’s.[3]
A full text of the judgement is available here.
[1].Whistleblower shot dead in Bihar, THE HINDU, available at http://www.thehindu.com/news/national/whistleblower-shot-dead-in-bihar/article4542293.ece; Tamil Nadu Whistleblower alleges death threats; Silence from Government, NDTV, available at http://www.ndtv.com/article/india/tamil-nadu-whistleblower-alleges-death-threats-silence-from-govt-410450.
[2]. Indian Postal Tracking Portal, http://www.indiapost.gov.in/tracking.aspx.
[3]. Supreme Court refuses to frame guidelines for protection of whistleblowers, Daily News and Analysis, available at http://www.dnaindia.com/india/report-supreme-court-refuses-to-frame-guideline-for-protection-of-whistleblowers-1525622.
CIS Welcomes 52nd Report on Cyber Crime, Cyber Security, and Right to Privacy
The Report consists of questions on the state of cyber security, cyber crime, and privacy posed by the Standing Committee and briefings and evidence provided by the Department of Electronics and Information Technology (DEITY ) in reply. The Report concludes with recommendations from the Standing Committee on the way forward.
The Report represents an important step forward in the realm of privacy and cyber security in India as the evidence provided by DEITY clarifies a number of aspects of India’s present and upcoming cyber security policies and practices. Furthermore, the recommendations by the Standing Committee highlight present gaps and inadequacies in India’s policies and practices and needed steps forward– particularly the need for a privacy legislation in India in the context of cyber security, increased transactions of sensitive data, and governmental projects like the Unique Identification Project.
Broadly, the Standing Committee sought input from DEITY on eight different aspects of cyber crime, cyber security, and privacy in India - namely: the growing incidents of cyber crime and resulting financial loss, the challenges and constraints of cyber crime, the role of relevant governmental organizations in India with respect to cyber security, preparedness and policy initiatives, cyber security and the right to privacy, monitoring and grievance redressal mechanism, and education and awareness initiatives. The evidence provided by DEITY sheds light on the present mindset of the Government at this time, upcoming policies, and capacity and infrastructure gaps in India’s cyber security framework.
The Centre for Internet and Society appreciates the Report and we would like to highlight and emphasize the following aspects:
Need for a privacy legislation and inadequacy of privacy provisions in Information Technology Act: When asked by the Standing Committee about the right to privacy and cyber security, DEITY highlighted the fact that the Information Technology Act contains sufficient safeguards for privacy, and added that the Department of Personnel and Training (DoPT) is in the process of developing a privacy legislation that will address the general concerns of privacy in the country, and thus the two together will be sufficient. DEITY also noted that no study on the extent of privacy breach due to cyber crime in India has been conducted. In their recommendations, the Standing Committee noted that it was unhappy that the Government has yet to institute a legal framework on privacy, as the increased transfer of sensitive data and projects like the UID leave citizens vulnerable to privacy violations . Significantly, the Standing Committee recommended that though the DoPT is currently responsible for drafting the Privacy Bill, DEITY should coordinate with the DoPT and become involved in the process.
As recognized by the Standing Committee, the Centre for Internet and Society would like to further emphasize the inadequacy of the provisions relating to privacy in the Information Technology Act, and the need for a privacy legislation in India. Inadequate aspects of the provisions have been pointed out by a number of sources. For example:
- The Report of the Group of Experts on Privacy: Prepared by the committee chaired by Justice AP Shah
- First Analysis of the Personal Data Protection Law in India: Prepared by the University of Namur for the Commission of the European Communities Directorate General for Justice, Freedom, and Security
- Comments on the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011: Prepared by the Centre for Internet and Society and submitted to the Committee on Subordinate Legislation of the 15th Lok Sabha
- India’s U-Turns on Data Privacy: Prepared by Graham Greenleaf for the Privacy Laws & Business International Report, Issues 110 -114, 2011
Unclear Enforcement of 43A and associated rules: In evidence provided, DEITY, while discussing section 43A and the associated Rules, noted that the Data Security Council of India and empanelled security auditors through CERT-in are responsible for the ‘auditing of best practice’s (pg 24). The Standing Committee did not directly respond to this comment.
The Centre for Internet and Society would like to point out that DEITY did not clearly state that DSCI and the auditors through CERT-in were responsible for auditing organizational security practices for compliance with 43A. Furthermore, there is no publicly available information regarding audits ensuring compliance with 43A or information about the number of companies that have been found to be compliant. The Centre for Internet and Society would like to encourage that this information be made public, and compliance with 43A be enforced at the organizational level.
UIDAI not in compliance with 43A and associated Rules: In evidence provided, DEITY noted that “..Section 43A and the rules published under that Section cover the entire privacy in case of digital data. These are being followed by UIDAI also and other organisations...” (pg.46) In their recommendations the Standing Committee did not directly address this comment, but did emphasize the need for a privacy legislation in light of the UID scheme.
The Centre for Internet and Society appreciates that the Standing Committee raised concern about the privacy implications of the UID project. We would like to highlight that the UIDAI is not a Body Corporate, and is not in compliance with 43A or the subsequent Rules in the Information Technology Act. Furthermore, the UID project involves the handling and processing of data in analogue and digital formats, and thus the privacy protections found under 43A are not sufficient.
The potential harms of metadata: In evidence provided, the Department noted “...we have been assured that whatever data has been gathered by them for surveillance relates only to the metadata..but we expressed that any incursion into the content will not be tolerated and is not tolerable from the Indian stand and point of view.” (pg.47) The Standing Committee did not respond directly to this comment.
The Centre for Internet and Society would like to thank the Standing Committee for noting that the Government should have taken prior steps to preventing such an interception from taking place and for recommending the Department to take develop a policy to prevent future instances of interception from taking place. The Centre for Internet and Society would like to emphasize the importance and potential sensitive nature of metadata. Metadata can, and often does, disclose more about an individual or an activity than the actual content. For example, metadata can reveal identity, behaviour patterns, associations, and can enable the mapping of location and individual movement. As such, the Centre for Internet and Society would recommend that the Government of India treat access to all information generated by individual and governmental communications as sensitive and confidential.
Inadequacy of the Information Technology Act: When asked by the Standing Committee if the Information Technology Act provided sufficient legal safeguards for cyber security and cyber crime, DEITY highlighted the fact that the Information Technology Act 2000 addresses all aspects of cyber crime in a comprehensive manner. DEITY also pointed out that the National Cyber Security Policy 2013 has provisions to enable the development of a legal framework, and the Department of Personnel and Training is in the process of drafting a privacy legislation for India that will fill any gaps that exist. In their recommendations, the Standing Committee recognized that the Information Technology Act does contain provisions that address cyber security and cyber crime, but, especially in the recent controversy over section 66A of the Act, Standing Committee emphasized the need for periodical reviews of the IT Act.
The Centre for Internet and Society appreciates the fact that the Committee recognized the need for periodical review of the Information Technology Act, particularly in light of the controversy over 66 A. The Centre for Internet and Society would like to underscore the problems associated with 66A and would like to highlight that with regards to privacy and cyber security, the IT Act is not adequate and falls short in a number of areas. Research that the Centre for Internet and Society has conducted explaining these weaknesses can be found through the below links:
- Breaking Down Section 66A of the IT Act
- Short note on IT Amendment Act, 2008
Implications of domestic servers: In response to questions posed by the Standing Committee about security risks associated with the importation of electronics and IT products, as well as the hosting of servers outside the country, DEITY noted the security risk of using foreign infrastructure and pointed to the hosting of servers in India as a solution to protecting the security and privacy of Indian data. The Standing Committee supported this initiative, and encouraged DEITY to take further steps towards securing and protecting the privacy of Indian data through the hosting of servers for critical sectors within India.
The Centre for Internet and Society appreciates the fact that the Standing Committee carefully limited the recommendation of locating servers in India to those in critical sectors, but would caution the Government of potential implications on users ability to freely access content and services, and highlight the fact that localization of servers is not a security solution in itself as a comprehensive solution and hardening of critical assets against cyber attacks is essential.
Incorporation of safeguards into MOU’s for international cooperation: When asked about MOU’s for international cooperation that DEITY has engaged in with other countries, DEITY reported that currently CERT-in is entering into a number of MOU’s with other countries to facilitate cooperation for cyber security purposes. Presently there are MOUs with the US, Japan, South Korea, Mauritius, Kasakhstan, Finland, and the Canada Electronics and ICT sector. DEITY is also seeking MOUs with Malaysia, Israel, Egypt, Canada, and Brazil. The Standing Committee supported India entering into MOU’s for purposes of international cooperation, and encouraged DEITY to continue entering into MOU’s to mitigate jurisdictional complications when seeking to address issues related to cyber security.
The Centre for Internet and Society recognizes the importance of international cooperation when handling issues related to cyber security and cyber crime. To ensure that this process is in line with human rights, the Centre for Internet and Society would encourage DEITY to ensure that all MOU’s and/or Mutual Legal Assistance Agreements:
- Uphold the principle of dual criminality
- Apply the highest level of protection for individuals in the case where the laws of more than one state could apply to communications surveillance
- Are not used by any party involved to circumvent domestic legal restrictions on communications surveillance.
- Are clearly documented and publicly available
- Contain provisions guaranteeing procedural fairness.[1]
Hactivism as a benefit to society: In evidence provided on page 14, DEITY, among other elements, referred to Hactivism as a societal challenge to securing cyber security and tackling cyber crime. The Standing Committee did not directly address this comment.
The Centre for Internet and Society would like to point out that hacktivism is a complex topic and consists of methods. Though some methods used by hacktivists are illegal, and some use hacktivism for censorship purposes and to target certain groups, other forms of hacktivism can benefit society and strengthen cyber security by finding and revealing vulnerabilities in a system, and bringing attention to illegal or violative practices.
This works towards ensuring that a system is adequately secure. Because of the dynamic nature of hacktivism, the Centre for Internet and Society believes that hacktivism needs to be evaluated on a case by case basis and the Government should not broadly label hacktivism as a challenge to cyber security and cyber crime.[2]
Importance of the anonymous speech: In evidence provided, DEITY noted the threat to cyber security that the anonymous nature of the internet posed. This was reiterated by the Standing Committee in their recommendations.
While recognizing the potential threat to cyber security that the anonymous nature of the internet can pose, the Centre for Internet and Society would like to highlight the importance of anonymous speech online to an individual’s right to free expression.
Conclusion
Recognizing the direct connection between a strong privacy framework and a strong cyber security framework, as security cannot be achieved without privacy, and recognizing the need for a privacy legislation in light of governmental projects like the UID, the Centre for Internet and Society welcomes the Fifty Second Report on Cyber Crime, Cyber Security, and the Right to Privacy and echoes the Standing Committees recommendation and emphasis on the need for a comprehensive privacy legislation to be passed in India.
[1]. These safeguards are reflected in the principle of “safeguards for International Cooperation” found in the International Principles on the Application of Human Rights to Communications Surveillance” https://en.necessaryandproportionate.org/text
[2]. For more information about hacktivism see: Activism, Hacktivism, and Cyberterrorism. The Internet as a Tool for Influencing Foreign Policy. By Dorothy E. Denning. Georgetown University. Available at: http://www.iwar.org.uk/cyberterror/resources/denning.htm
Privacy Protection Bill
 Privacy (Protection) Bill - 20 Jan 2014.pdf
—
PDF document,
224 kB (230067 bytes)
Privacy (Protection) Bill - 20 Jan 2014.pdf
—
PDF document,
224 kB (230067 bytes)
Open Call for Comments: The Privacy Protection Bill 2013 drafted by the Centre for Internet and Society
In early 2013 the Centre for Internet and Society drafted the Privacy (Protection) Bill 2013 as a citizen’s version of privacy legislation for India. The Privacy (Protection) Bill, 2013 seeks to protect privacy by regulating (i) the manner in which personal data is collected, processed, stored, transferred and destroyed — both by private persons for commercial gain and by the state for the purpose of governance; (ii) the conditions upon which, and procedure for, interceptions of communications — both voice and data communications, including both data-in-motion and data-at-rest — may be conducted and the authorities permitted to exercise those powers; and, (iii) the manner in which forms of surveillance not amounting to interceptions of communications — including the collection of intelligence from humans, signals, geospatial sources, measurements and signatures, and financial sources — may be conducted.
The Centre for Internet and Society has been collecting comments to the Privacy Protection Bill since April 2013 with the intention of submitting the Bill to the Department of Personnel and Training as a citizen’s version of a privacy legislation for India. If you would like to submit comments on the Privacy Protection Bill to be included as part of the Centre for Internet and Society’s submission to the Department of Personnel and Training, please email comments to [email protected].
Download the latest version of the Privacy Protection Bill (February 2014)
Comparison of Section 35(1) of the Draft Human DNA Profiling Bill and Section 4 of the Identification Act Revised Statute of Canada
In continuance of research around the Draft Human DNA Profiling Bill that has been drafted the Department of Biotechnology, this blog entry reviews best practices for the communication of DNA profiles from the DNA Bank Manager to law enforcement and the police, compares the section 35(1) of the Draft Human DNA Profiling Bill and section 4 of the Identification Act Revised Statute of Canada, and recommends a revision of the present provision in the Draft Human DNA Profiling Bill.
Indian Provision
35 (1) “On receipt of a DNA profile for entry in the DNA Data Bank, the DNA Bank Manager shall cause it to be compared with the DNA profiles in the DNA Data Bank in order to determine whether it is already contained in the DNA Data Bank and shall communicate, for the purposes of the investigation or prosecution in a criminal offence, the following information to a court, tribunal, law enforcement agency or DNA laboratory in India which the DNA Data Bank Manager considers is concerned with it, appropriate, namely –
(a) As to whether the DNA profile received is already contained in the Data Bank; and
(b) Any information, other than the DNA profile received, is contained in the Data Bank in relation to the DNA profile received.
(2) The information as to whether a person’s DNA profile is contained in the offenders’ index may be communicated to an official who is authorized to receive the same as prescribed.”
Canadian Provision vs. Indian Provision
According to the Draft Human DNA Profiling Bill 35(1) was adopted from the DNA Identification Act Revised Statute of Canada section 4. The provision found in the Draft Human DNA Profiling Bill is different in three ways:
- The Canadian statute limits the communication of whether a DNA profile is contained in the Data Bank or not to law enforcement agencies or other DNA laboratories, where as the provision in the Draft Human DNA Profiling Bill allows the communication to law enforcement agencies, other DNA data banks, and courts and tribunals.
- The Canadian statute limits the comparison of any DNA profile to that as entered in the convicted offenders index or the crime scene index with those DNA profiles that are already contained in the databank, where as the Draft Human DNA Profiling Bill allows for any received profile to be compared with the other profiles in the DNA Data Bank.
- The Canadian statute defines four types of information that may be communicated to law enforcement or another DNA databank including:
- (a) if the DNA profile is not already contained in the data bank, the fact that it is not;
- (b) if the DNA profile is already contained in the data bank, the information contained in the data bank in relation to that DNA profile;
- (c) if the DNA profile is, in the opinion of the Commissioner, similar to one that is already contained in the data bank, the similar DNA profile; and
- (d) if a law enforcement agency or laboratory advises the Commissioner that their comparison of a DNA profile communicated under paragraph (c) with one that is connected to the commission of a criminal offence has not excluded the former as a possible match, the information contained in the data bank in relation to that profile.
While the Draft Human DNA Profiling Bill provides for communication of only (a) and (b) by the DNA Data Bank Manager.
Concerns with 35(1) and Best Practices
The Centre for Internet and Society finds 35(1) problematic because a DNA profile is never a complete match, and is instead a scientific and statistical based probability. There are a number of steps that go into the analysis of a DNA profile. According to the US National Institute of Justice, these include: “1) the isolation of the DNA from an evidence sample containing DNA of unknown origin, and generally at a later time, the isolation of DNA from a sample (e.g., blood) from a known individual; 2) the processing of the DNA so that test results may be obtained; 3) the determination of the DNA test results (or types), from specific regions of the DNA; and 4) the comparison and interpretation of the test results from the unknown and known samples to determine whether the known individual is not the source of the DNA or is included as a possible source of the DNA.”
Though it is common for DNA Banks to communicate responses such as “match”, “no match”, or “partial match” or “inclusion”, “exclusion”, or “inconclusive” to inquiries received from law enforcement and other DNA Banks, this is not the case for communications to courts and tribunals. For example in England and Wales guidelines for presenting DNA evidence in court were laid out in the rule Rv. Dohemy and Adams (1997) 1 Cr. App. R. 396. Along with comprehensive guidelines on how experts should conduct themselves in court to prevent bias, the guidelines require the following information to be presented when DNA material is used as evidence in a case:
- “The scientist should adduce the evidence of the DNA comparisons between the crime stain and the defendant’s sample together with the calculations of the Random Match Probability.
- Whenever DNA evidence is adduced the Crown should serve on the defence details as to how the calculations have been carried out which are sufficient to enable the defence to scrutinize the basis of the calculations.
- The Forensic Science Service should make available to a defence expert, if requested, the databases upon which the calculations have been made.
- The expert will, on the basis of empirical statistical data, five the jury the random occurrence rations - the frequency with which the matching DNA characteristics are likely to be found in the population at large.
- Provided that the expert has the necessary data, it may then be appropriate for him to indicate how many people with the matching characteristics are likely to be found in the United Kingdom...”
Recommendations
Given the influential weight that DNA evidence can have in a case, it is critical that the evidence is accurately presented to the court and other key stakeholders. The Centre for Internet and Society recommends that the Bill should distinguish the DNA Bank Manager’s response to law enforcement and other DNA Laboratory’s and the DNA Bank Manger’s response to courts and tribunals as below:
- Response to Law enforcement agency and DNA Laboratory: The DNA Bank Manger should respond to a request from law enforcement or a DNA laboratory with either: "match" or "partial match" .
- Response to Court and tribunal: When DNA evidence is used in a court of law, the Bill should provide that the presentation should include:
- The random match probability: The probability that the profile is in the sample from the individual tested if the individual tested has been selected at random.
- The frequency with which the matching DNA characteristics are likely to be found in the population at large.
- The probability of contamination.
The Bill should also provide for the database upon which the calculations were based to be made available when requested. In addition, the Bill should provide for rules to be made prescribing the procedure for presentation.
[]. http://nij.gov/topics/forensics/evidence/dna/basics/Pages/analyzing.aspx
[2]. http://www.medicalgenomics.co.uk/pdf/Barrister_vol32-2007.pdf
Organizational Chart
 Organisational Chart.pdf
—
PDF document,
669 kB (686078 bytes)
Organisational Chart.pdf
—
PDF document,
669 kB (686078 bytes)
Freedom of Expression and Privacy
 Freedom of Expression and Privacy.pdf
—
PDF document,
356 kB (364792 bytes)
Freedom of Expression and Privacy.pdf
—
PDF document,
356 kB (364792 bytes)
Law Enforcement, National Security, and Privacy
 Law Enforcement or National Security.pdf
—
PDF document,
422 kB (432893 bytes)
Law Enforcement or National Security.pdf
—
PDF document,
422 kB (432893 bytes)
Big Democracy, Big Surveillance: India's Surveillance State
This article by Maria Xynou was published by OpenDemocracy on 10 February 2014.
Worried about the secret, mass surveillance schemes being carried out by the NSA? While we should be, some of the surveillance schemes in the world's largest democracy, India, are arguably in the same league.
Surveillance is being globalised to the extent that even India, a country with huge poverty issues, is investing millions of dollars in creating an expansive surveillance regime. However, why would communications monitoring interest Indian authorities, when the majority of the population lives below the line of poverty and only 17% of the population has access to the Internet?
The official political motivation behind surveillance in India appears to be the government's determination to tackle terrorism in the country. The 2008 Mumbai terrorist attacks were arguably a similar landmark to the 9/11 terrorist attacks in the US, and both governments officially announced their intention to carry out surveillance as a counter-terrorism measure. However, unlike in the west, terrorist attacks in India are much more common, and the National Security Adviser reported in 2008 that 800 terrorist cells were operational in the country. With India’s history of major terror attacks in India over the last 25 years, it's easy for one to be persuaded that terrorism is actually a major threat to national security.
India's surveillance schemes
India’s surveillance programs mostly started following the 2008 Mumbai terror attacks. That was when the Ministry of Home Affairs first proposed the creation of a National Intelligence Grid (NATGRID), which will give 11 intelligence and investigative agencies real-time access to 21 citizen data sources to track terror activities. These citizen data sources will be provided by various ministries and departments, otherwise called “provider agencies”, and will include bank account details, telephone records, passport data and vehicle registration details, among other types of data.
The Ministry of Home Affairs has sought over Rs. 3,400 crore (around USD 540 million!) for the implementation of NATGRID, which aims to create comprehensive patterns of intelligence by collecting sensitive information from databases of departments like the police, banks, tax and telecoms to supposedly track any terror suspect and incident.
But NATGRID is far from India's only data sharing scheme. In 2009 the Cabinet Committee on Economic Affairs approved the creation and implementation of the Crime and Criminal Tracking Network & Systems (CCTNS), which would facilitate the sharing of databases among 14,000 police stations across all 35 states and Union Territories of India, excluding 6,000 police offices which are high in the police hierarchy. Rs. 2,000 crore (around USD 320 million) have been allocated for the CCTNS, which is being implemented by the National Crime Records Bureau under the national e-governance scheme. The CCTNS not only increases transparency by automating the function of police stations, but also provides the civil police with tools, technology and information to facilitate the investigation of crime and detection of criminals.
But apparently, sharing data and linking databases is not enough to track criminals and terrorists. As such, in the aftermath of the 2008 Mumbai terror attacks, the Indian government also implemented various interception systems. In September 2013 it was reported that the Indian government has been operating Lawful Intercept & Monitoring (LIM) systems, widely in secret. In particular, mobile operators in India have deployed their own LIM systems allowing for the so-called “lawful interception” of calls by the government. And possibly to enable this, mobile operators are required to provide subscriber verification to the Telecom Enforcement, Resource and Monitoring (TERM) cells of the Department of Telecommunications.
In the case of Internet traffic, the LIM systems are deployed at the international gateways of large Internet Service Providers (ISPs) and expand to a broad search across all Internet traffic using “keywords” and “key-phrases”. In other words, security agencies using LIM systems are capable of launching a search for suspicious words, resulting in the indiscriminate monitoring of all Internet traffic, possibly without court oversight and without the knowledge of ISPs.
India has also automated and centralized the interception of communications through the Central Monitoring System (CMS). This project was initially envisioned in 2009, following the 2008 Mumbai terror attacks and was approved in 2011. The CMS intercepts all telecommunications in India and centrally stores the data in national and regional databases. The CMS will be connected with the Telephone Call Interception System (TCIS) which will help monitor voice calls, SMS and MMS, fax communications on landlines, CDMA, video calls, GSM and 3G networks. Agencies which will have access to the CMS include the Intelligence Bureau (IB), the Central Bureau of Investigation (CBI), the Directorate of Revenue Intelligence (DRI), the Research and Analysis Wing (RAW) and the National Investigation Agency (NIA).
Unlike mainstream interception, where service providers are required to intercept communications and provision interception requests to law enforcement agencies, the Central Monitoring System will automate the entire process of interception. This means that the CMS authority will have centralized access to all intercepted data and that the authority can also bypass service providers in gaining such access. Once security agencies have access to this data, they are equipped with Direct Electronic Provisioning, filters and alerts on the target numbers, as well as with Call Details Records (CDR) analysis and data mining tools to identify the personal information of target numbers.
Given that roughly 73% of India's population uses mobile phones, this means that the Central Monitoring System can potentially affect about 893 million people, more than double the population of the United States! However, how is it even possible for Indian authorities to mine the data of literally millions of people? Who supplies Indian authorities with the technology to do this and what type of technology is actually being used?
India's surveillance industry
India has the world's second largest population, consisting of more than a billion people and an expanding middle class. Undoubtedly, India is a big market and many international companies aspire in investing in the country. Unfortunately though, along with everything else being imported into India, surveillance technologies are no exception.
Some of the biggest and most notorious surveillance technology companies in the world, such as ZTE, Utimaco and Verint, have offices in India. Even FinFisher command and control servers have been found in India. However, in addition to allowing foreign surveillance technology companies to create offices and to sell their products and solutions in the country, local companies selling controversial spyware appear to be on the rise too.
Kommlabs Dezign is an Indian company which loves to show off its Internet monitoring solutions at various ISS trade shows, otherwise known as “the Wiretapper's Ball”. In particular, Kommlabs Dezign sells VerbaNET, an Internet Interception Solution, as well as VerbaCENTRE, which is a Unified Monitoring Centre that can even detect cognitive and emotional stress in voice calls and flag them! In other words, Kommlabs Dezign makes a point that not only should we worry about what we text and say over our phones, but that we should also worry about what we sound like when on the phone.
Vehere is another Indian company which sells various surveillance solutions and notably sells vCRIMES, which is a Call Details Records (CDR) analysis system. VCRIMES is used to analyse and gather intelligence and to unveil hidden interconnections and relations through communications. This system also includes a tool for detecting sleeper cells through advanced statistical analysis and can analyse more than 40 billion records in less than 3 seconds.
Paladion Networks is headquartered in Bangalore, India and sells various Internet Monitoring Systems, Telecom Operator Interception Systems, SSL Interception and Decryption Systems and Cyber Cafe Monitoring Systems to law enforcement agencies in India and abroad. In fact, Paladion Networks even states in its website that its customers include India's Ministry of Information Technology and the U.S Department of Justice.
ClearTrail Technologies is yet another Indian company which not only sponsors global surveillance trade shows but also sells a wide range of monitoring solutions to law enforcement agencies in India and abroad. ComTrail is a solution for the centralised mass interception and monitoring of voice and data networks, including Gmail, Yahoo, Hotmail, BlackBerry, ICQ and GSM voice calls. Furthermore, ComTrail is equipped to handle millions of communications per day, correlating identities across multiple networks, and can instantly analyse data across thousands of terabytes.
ClearTrail also sells xTrail, which is a solution for the targeted interception, decoding and analysis of data traffic over IP networks and which enables law enforcement agencies to intercept and monitor targeted communications without degrading the service quality of the IP network. Interestingly, xTrail can filter based on a “pure keyword”, a URL/Domain with a keyword, a mobile number or even with just a user identity, such as an email ID, chat ID or VoIP ID.
Apparently, some the biggest challenges that law enforcement agencies face when monitoring communications include cases when targets operate from public Internet networks and/or use encryption. However, it turns out that ClearTrail's QuickTrail solution is designed to gather intelligence from public Internet networks, when a target is operating from a cyber cafe, a hotel, a university campus or a free Wi-Fi zone. This device can remotely deploy spyware into a target's computer and supports protocol decoding, including HTTP, SMTP, POP3 and HTTPS.
Additionally, QuickTrail can identify a target machine on the basis of metadata, such as an IP address, and can monitor Ethernet LANs in real time, as well as monitor Gmail, Yahoo and all other HTTPS-based communications. ClearTrail's mTrail is designed for the passive 'off-the-air' interception of GSM communications, including the interception of targeted calls from pre-defined suspect lists and the monitoring of SMS and protocol information. MTrail also identifies a target's location by using signal strength, target numbers, such as IMSI, TIMSI, IMEI or MSI SDN, which makes it possible to listen to the conversation of so-called “lawfully intercepted” calls in near real-time.
In short, it looks like India is reaching the top league when it comes to surveillance technologies, especially since many of its companies and their products appear to be just as scary as some of the most sophisticated spying gear sold by the West. India may be the world's largest (by population) democracy, but that means that it has a huge population with way too many opinions...and apparently, the private and public sectors in India appear to be joining forces to do something about it.
So do Indians have nothing to hide?
A very popular rhetoric in both India and the west is that citizens should not be concerned about surveillance because, after all, if they are not terrorists, they should have nothing to hide. However, privacy advocate Caspar Bowden has rightfully stated that this rhetoric is fundamentally flawed and that we should all indeed “have something to hide”. But is privacy just about “having something to hide”? Jacob Appelbaum has stated that this rhetoric is merely a psychological copying mechanism when dealing with security.
It's probably rather comforting and reassuring to think that we are not special or important enough for surveillance to affect us personally. But is that really up to us to decide? Unfortunately not. The very point of data mining is to match patterns, create profiles of individuals and to unveil hidden interconnections and relations. A data analyst can uncover more information about us than what we are even aware of and it is they who decide if our data is “incriminating” or not. Or even worse: in many cases it's up to data mining software to decide how “special” or “important” we are. And unfortunately, technology is not infallible.
The world's largest democracy, which is also one of the most corrupt countries in the world, is implementing many controversial surveillance schemes which lack transparency, accountability and adequate legal backing, and which are largely being carried out in secret. And to make matters worse, India lacks privacy legislation. Over a billion people in a democratic regime are exposed to inadequately regulated surveillance schemes, while a local surveillance industry is thriving without any checks or balances whatsoever. What will this mean for the global future of democracy?
Spreadsheet data on sample of 50 security companies
 CIS - Surveillance Technology Companies in India.pdf
—
PDF document,
2028 kB (2076975 bytes)
CIS - Surveillance Technology Companies in India.pdf
—
PDF document,
2028 kB (2076975 bytes)
MAG Meeting Minutes
 WAY FORWARDpost 1st meeting of MAG-1.doc
—
Microsoft Word Document,
24 kB (25088 bytes)
WAY FORWARDpost 1st meeting of MAG-1.doc
—
Microsoft Word Document,
24 kB (25088 bytes)
APC Event at Wedgewood
 APC_ILL_agenda07022014_v2_FINAL.pdf
—
PDF document,
112 kB (115261 bytes)
APC_ILL_agenda07022014_v2_FINAL.pdf
—
PDF document,
112 kB (115261 bytes)
UIDAI Practices and the Information Technology Act, Section 43A and Subsequent Rules
In the 52nd Report on Cyber Crime, Cyber Security, and the Right to Privacy – in evidence provided, the Department of Electronics and Information Technology stated “...Section 43A and the rules published under that Section cover the entire privacy in case of digital data. These are being followed by UIDAI also and other organisations...” (pg.46) [1]
This blog post explains the requirements found under Section 43A of the Information Technology Act 2000 and the subsequent Information Technology “ Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules 2011[2] and analyses publicly available documents from the UIDAI website[3] as well as the UIDAI enrolment form[4] to demonstrate the ways in which:
- UIDAI practices are in line with section 43A and the Rules,
- UIDAI practices are not in line with section 43A and the Rules,
- UIDAI practices are partially in with section 43A and the Rules
- Where more information is needed to draw a conclusion.
Applicability and Scope
Section 43A of the Information Technology Act 2008 and subsequent Rules apply only to Body Corporate and to digital information.
Body Corporate under the Information Technology Act 2008 is defined as:
“Any company and includes a firm, sole proprietorship or other association of individuals engaged in commercial or professional activities”
UIDAI Practices - not in line: The UIDAI is not a body corporate. The UIDAI is an attached office under the aegis of the Planning Commission that was set up by an executive order.[5]
The UIDAI collects, processes, stores, and shares both digital and non-digital information. As section 43A and subsequent Rules apply only to digital information, there is not sufficient protection provided over all the information collected, processed, stored, and used by the UIDAI.
Privacy Policy on Website
Rule 4 requires body corporate to provide a privacy policy on their website. The privacy policy must include:
- Clear and easily accessible statements of its practices and policies
- Type of personal or sensitive personal data or information collected
- Purpose of collection and usage of such information
- Disclosure of information including sensitive personal information
- Reasonable security practices and procedures as provided under rule 8
UIDAI Practices - Partially in Line
- Though the UIDAI has placed a privacy policy[6] on their website, the privacy policy only addresses the use of website and does not comprehensively provide clear and accessible statements about all of the UIDAI’s practices and policies.
- The UIDAI privacy policy does not state the specific types of personal or sensitive data that could be collected, but instead states “As a general rule, this website does not collect Personal Information about you when you visit the site. You can generally visit the site without revealing Personal Information, unless you choose to provide such information.”
Features on the UIDAI website that require individuals to provide personal information and sensitive personal information include: Booking an appointment, checking aadhaar status, enrolling for e-aadhaar, enrolling for aadhaar, updating aadhaar data. Types of information required for these services include: mobile number, name, address, gender, date of birth, and enrolment ID.[7]
The privacy policy goes on to state: “If you are asked for any other Personal Information you will be informed how it will be used if you choose to give it. If at any time you believe the principles referred to in this privacy statement have not been followed, or have any other comments on these principles, please notify the webmaster through the Contact Us page. Note: The use of the term "Personal Information" in this privacy statement refers to any information from which your identity is apparent or can be reasonably ascertained.” - The UIDAI privacy policy does explain the purpose for collection of information on the website and the use of collected information.
- The UIDAI privacy policy does not address the possibility of disclosure of information collected by the UIDAI from the use of its website, except in the case of when an individual provides his/her email at which point the privacy policy states “Your e-mail address will not be used for any other purpose, and will not be disclosed without your consent.”
- The UIDAI privacy policy does not provide information about the security practices adopted by the UIDAI.
Consent
Rule 5 requires that prior to the collection of sensitive personal data, the body corporate must obtain consent, either in writing or through fax regarding the purpose of usage before collection of such information.
UIDAI Practices - in Line
The UIDAI collects written consent from individuals through the enrolment form for the issuance of an Aadhaar number.
Collection Limitation
Rule 5 (2) requires that body corporate only collect sensitive personal data if it is connected to a lawful purpose and if it is considered necessary for that purpose.
UIDAI Practices - in Line
The Aadhaar enrolment form requires only the necessary sensitive personal data for the issuance of an Aadhaar number. Individuals are given the option to provide banking and financial information.
Notice During Direct Collection
Rule 5(3) requires that while collecting information directly from an individual the body corporate must provide the following information:
- The fact that the information is being collected
- The purpose for which the information is being collected
- The intended recipients of the information
- The name and address of the agency that is collecting the information
- The name and address of the agency that will retain the information
UIDAI Practices - Partially in Line
The Aadhaar enrolment form does not provide the following information:
- The intended recipients of the information
- The name and address of the agency collecting the information
- The name and address of the agency that will retain the information
Retention Limitation
Rule 5(4) requires that body corporate must retain sensitive personal data only for as long as it takes to fulfil the stated purpose or otherwise required under law.
UIDAI Practices - Unclear
It is unclear from publicly available information what the UIDAI retention practices are.
Use Limitation
Rule 5(5) requires that information must be used for the purpose that it was collected for.
UIDAI Practices - Unclear
It is unclear from publicly available information if the UIDAI is using collected information only for the purpose for which it was collected for.
Right to Access and Correct
Rule 5(6) requires body corporate to provide individuals with the ability to review the information they have provided and access and correct personal or sensitive personal information.
UIDAI Practices - Partially in Line
Though the UIDAI provides individuals with the ability to access and correct personal information, as stated on the enrolment form, correction is free only if changed within 96 hours of enrolment. Additionally, as stated on the enrolment form, if an individual chooses to allow for the UIDAI to facilitate the opening of a bank account and link present bank accounts to the UID number, this information, after being provided, cannot be corrected. The UIDAI website has a portal for updating information, but only name, address, gender, data of birth, and mobile number can be updated through this method. [9]
Right to ‘Opt Out’ and Withdraw Consent
Rule 5(7) requires that body corporate must provide individuals with the option of 'opting out' of providing data or information sought. Individuals also have the right to withdraw consent at any point of time. Body corporate has the right to withdraw services if consent is withdrawn.
UIDAI Practices - Partially in Line
The UID enrolment form provides individuals with one ‘optional’ field - the option of having the UIDAI open a bank account and link it to the individuals UID number or having the UIDAI link present bank accounts to individuals UID number. No other option to ‘opt out’ or withdraw consent is present on the enrolment form or the UIDAI privacy policy, terms of use, or website.
Security of Information
Rule 8 requires that body corporate must secure information in accordance with the ISO 27001 standard. These practices must be audited on an annual basis or when the body corporate undertakes a significant up gradation of its process and computer resource.
UIDAI Practices - Unclear
The security practices adopted by the UIDAI are not mentioned in the website privacy policy, on the website, or on the enrolment form, thus it is unclear from publicly available information if the UID is compliant with ISO 27001 standards. Though the UIDAI has been functioning since 2010, and it is unclear from publicly available information if annual audits of the UIDAI security practices have been undertaken.
Disclosure with Consent
Rule 6 requires that body corporate must have consent before disclosing sensitive personal data to any third person or party, except in the case with Government agencies for the purpose of verification of identity, prevention, detection, investigation, including cyber incidents and prosecution and punishment of offenses, on receipt of a written request.
UIDAI Practices - Partially in Line
In the enrolment form, consent for disclosure is stated as ‘‘I have no objection to the UIDAI sharing information provided by me to the UIDAI with agencies engaged in delivery of welfare services.” This is a blanket statement and allows for all future possibilities of sharing and disclosure of information provided with any organization that the UIDAI deems as ‘engaged in the delivery of welfare services’.
The UIDAI privacy policy only addresses the disclosure of an individual’s email address with consent. Though not directly addressing disclosure, the UIDAI privacy policy also states “ We will not identify users or their browsing activities, except when a law enforcement agency may exercise a warrant to inspect the service provider's logs.”
Prohibition on Publishing and Further Disclosure
Rule 6(3) and 6(4) prohibit the body corporate from publishing sensitive personal data or information. Similarly, organizations receiving sensitive personal data are not allowed to disclose it further.
UIDAI Practices - in Line
The UDAI does not publish sensitive personal data. It is unclear what practices and standards registrars and enrolment agencies are functioning under.
Requirements for Transfer of Sensitive Personal Data
Rule 7 requires that body corporate may transfer sensitive personal data into another jurisdiction only if the country ensures the same level of protection.
UIDAI Practices - Unclear
It is unclear from publicly available information if information collected by the UIDAI is transferred outside of India.
Establishment of Grievance Officer
Rule 5(9) requires that body corporate must establish a grievance officer and the details must be posted on the body corporates website and grievances must be addressed within a month of receipt.
UIDAI Practices - in Line
The website of the UIDAI provides details of a grievance officer that individuals can contact.[10] It is unclear from publicly available information if grievances are addressed within a month.
[1]. http://164.100.47.134/lsscommittee/Information%20Technology/15_Information_Technology_52.pdf
[2]. http://dispur.nic.in/itact/it-procedures-sensitive-personal-data-rules-2011.pdf
[4]. http://www.jharkhand.gov.in/marpdf/Aadhar-enrolmentform.pdf
[5]. http://uidai.gov.in/organization-details.html
[6]. http://uidai.gov.in/privacy-policy.html
[7]. http://resident.uidai.net.in/home
[8]. http://www.jharkhand.gov.in/marpdf/Aadhar-enrolmentform.pdf
Will You be Paid to Post a Picture?
The article was published in the Indian Express on February 18, 2014
The age of volunteerism is officially over. The last decade of the mass adoption of the internet has been fuelled by endless human hours being spent in producing information which is the new currency of our times. The big transition to Web 2.0 began when the individual “user” became more than either an individual or the user. The individual found herself as a part of a collective, finding a voice and a community of others to belong to. Simultaneously, instead of being a passive consumer of the web, the user started producing data — blogs, videos, tweets, content management systems, online discussion boards, massively multiple online role-playing platforms, social network transactions — all of which became a part of the new Web’s widespread popularity.
Almost everything that we understand as the social web today is contingent upon people producing data in their interactions with the world around them. From knowledge producing websites like Wikipedia to entertainment platforms like YouTube, visualisation and data gathering spaces like Pinterest to photographs of self, food and cute animals on Instagram, political and social commentaries on Tumblr to Listicles and memes on Buzzfeed, the internet is a veritable smorgasbord of new information forms, formats and functions that are generated by the users.
What is possibly the most exciting about this burgeoning information universe has been the amount of free labour that goes into it, and often remains invisible. As digital labour scholar Trebor Schulz points out, the internet has become both a factory and a playground, where our leisure time is capitalised into producing work that sustains the new attention and information economies. For instance, the world’s largest social networking site, Facebook, does not produce any of its contents. It is, in fact, a system of information mining and sorting, which works as long as a growing user base continues to produce information on it. Tomorrow, if all of us stop producing Facebook, and only lurk on it, the platform will collapse. Which is why, Facebook continues to acquire new platforms and applications to be integrated into its universe.
Similarly, the real effort that goes into the sustenance of sites like Wikipedia, which has become the de facto reference for global knowledge systems, is carried out by unsung and invisible editors who patiently, meticulously, and without almost any expectation, continue to add, verify, strengthen and curate reliable information that we can use. When the non-profit organisation WikiMedia Foundation prides itself in running one of the least expensive websites in the top 10 most visited sites in the world, it is signalling its deep appreciation for the countless human hours that have made Wikipedia possible.
But, in recent years, there is noticeable stagnation in the wave of free information production on the Web. Oh, don’t get me wrong. We are producing an unprecedented amount of data — we are constantly being watched by surveillance technologies that detect biometric and genetic make-up of all our transactions, or we are inviting people to watch us on social network sites where we reveal some of our deepest secrets and desires, or we are watching ourselves, quantifying everything from things we ate to the number of hours we sleep. And yet, as we live in a world of Big Data, there is a definite decrease in people contributing to production of free information.
As the digital natives move from the web to mobile phones, traditional websites are already facing a crisis. News and media agencies that have celebrated the global citizen media networks have started realising that the individual user is more interested in local networks and information ecologies which are independent of mainstream conglomerates. And people are realising that their time and effort is worth money. They can be easily compensated for their online activities and gain reputation and importance.
The tension only becomes more palpable when people start realising that there are others who are being paid to work on the platforms that they are contributing to. We all knew that this model of depending on free information was not a sustainable one. But it seems the day has arrived, especially with the recent drives on Wikipedia to build specialised knowledge editors. In the last few months, we have seen people in the FemTechNet project — an academic activist feminist project that seeks to remind us of the intersections of feminism and technology in network societies — carry out “Wikistorming”, where students are adding pages of women’s contribution to technologies on Wikipedia. More recently, medicine students at University of Chicago have taken to correcting and adding accurate information to Wikipedia, which is often a source of health information.
Both of these are fantastic efforts to add to the platform that was the underdog that overthrew the mammoth encyclopaedia like The Encyclopaedia Britannica. We hope more specialised users in different locations, fields, disciplines and languages continue to edit and contribute to Wikipedia. However, it is also a signal that the generalist information producer is on the decline. We are transitioning into a new age, where people are going to need rewards, incentives and benefits for performing information transactions on the web. The user is no longer going to be available for free labour, and it is time we started thinking of “paid usership”.
Surveillance and the Indian Constitution - Part 3: The Public/Private Distinction and the Supreme Court’s Wrong Turn
Gautam Bhatia's blog post was originally published on Indian Constitutional Law and Philosophy Blog
We have seen that Gobind essentially crystallized a constitutional right to privacy as an aspect of personal liberty, to be infringed only by a narrowly-tailored law that served a compelling state interest. After the landmark decision in Gobind, Malak Singh v State of P&H was the next targeted-surveillance history-sheeter case to come before the Supreme Court. In that case, Rule 23 of the Punjab Police Rules was at issue. Its vires was not disputed, so the question was a direct matter of constitutionality. An order of surveillance was challenged by two individuals, on the ground that there were no reasonable bases for suspecting them of being repeat criminals, and that their inclusion in the surveillance register was politically motivated. After holding that entry into a surveillance sheet was a purely administrative measure, and thus required no prior hearing (audi alteram partem), the Court then embarked upon a lengthy disquisition about the scope and limitations of surveillance, which deserves to be reproduced in full:
“But all this does not mean that the police have a licence to enter the names of whoever they like (dislike?) in the surveillance register; nor can the surveillance be such as to squeeze the fundamental freedoms guaranteed to all citizens or to obstruct the free exercise and enjoyment of those freedoms; nor can the surveillance so intrude as to offend the dignity of the individual. Surveillance of persons who do not fall within the categories mentioned in Rule 23.4 or for reasons unconnected with the prevention of crime, or excessive surveillance falling beyond the limits prescribed by the rules, will entitle a citizen to the Court’s protection which the court will not hesitate to give. The very rules which prescribe the conditions for making entries in the surveillance register and the mode of surveillance appear to recognise the caution and care with which the police officers are required to proceed. The note following R. 23.4 is instructive. It enjoins a duty upon the police officer to construe the rule strictly and confine the entries in the surveillance register to the class of persons mentioned in the rule. Similarly R.23.7 demands that there should be no illegal interference in the guise of surveillance. Surveillance, therefore, has to be unobstrusive and within bounds. Ordinarily the names of persons with previous criminal record alone are entered in the surveillance register. They must be proclaimed offenders, previous convicts, or persons who have already been placed on security for good behaviour. In addition, names of persons who are reasonably believed to be habitual offenders or receivers of stolen property whether they have been convicted or not may be entered. It is only in the case of this category of persons that there may be occasion for abuse of the power of the police officer to make entries in the surveillance register. But, here, the entry can only be made by the order of the Superintendent of Police who is prohibited from delegating his authority under Rule 23.5. Further it is necessary that the Superintendent of Police must entertain a reasonable belief that persons whose names are to be entered in Part II are habitual offenders or receivers of stolen property. While it may not be necessary to supply the grounds of belief to the persons whose names are entered in the surveillance register it may become necessary in some cases to satisfy the Court when an entry is challenged that there are grounds to entertain such reasonable belief. In fact in the present case we sent for the relevant records and we have satisfied ourselves that there were sufficient grounds for the Superintendent of Police to entertain a reasonable belief. In the result we reject both the appeals subject to our observations regarding the mode of surveillance. There is no order as to costs.”
Three things emerge from this holding: first, the Court follows Gobind in locating the right to privacy within the philosophical concept of individual dignity, found in Article 21’s guarantee of personal liberty. Secondly, it follows Kharak Singh, Malkani and Gobind in insisting that the surveillance be targeted, limited to fulfilling the government’s crime-prevention objectives, and be limited – not even to suspected criminals, but – repeat offenders or serious criminals. And thirdly, it leaves open a role for the Court – that is, judicial review – in examining the grounds of surveillance, if challenged in a particular case.
After Malak Singh, there is another period of quiet. LIC v Manubhai D Shah, in 1993, attributed – wrongly – to Indian Express Newspapers the proposition that Article 19(1)(a)’s free expression right included privacy of communications (Indian Express itself had cited a UN Report without incorporating it into its holding).
Soon afterwards, R. Rajagopal v State of TN involved the question of the publication of a convicted criminal’s autobiography by a publishing house; Auto Shankar, the convict in question, had supposedly withdrawn his consent after agreeing to the book’s publication, but the publishing house was determined to go ahead with it. Technically, this wasn’t an Article 21 case: so much is made clear by the very manner in which the Court frames its issues: the question is whether a citizen of the country can prevent another person from writing his biography, or life story. (Paragraph 8) The Court itself made things clear when it held that the right of privacy has two aspects: the tortious aspect, which provides damages for a breach of individual privacy; and the constitutional aspect, which protects privacy against unlawful governmental intrusion. (Paragraph 9) Having made this distinction, the Court went on to cite a number of American cases that were precisely about the right to privacy against governmental intrusion, and therefore – ideally – irrelevant to the present case (Paras 13 – 16); and then, without quite explaining how it was using these cases – or whether they were relevant at all, it switched to examining the law of defamation (Para 17 onwards). It would be safe to conclude, therefore, in light of the clear distinctions that it made, the Court was concerned in R. Rajagopal about an action between private parties, and therefore, privacy in the context of tort law. It’s confusing observations, however, were to have rather unfortunate effects, as we shall see.
We now come to a series of curious cases involving privacy and medical law. In Mr X v Hospital Z, the question arose whether a Hospital that – in the context of a planned marriage – had disclosed the appellant’s HIV+ status, leading to his social ostracism – was in breach of his right to privacy. The Court cited Rajagopal, but unfortunately failed to understand it, and turned the question into one of the constitutional right to privacy, and not the private right. Why the Court turned an issue between two private parties – adequately covered by the tort of breach of confidentiality – into an Article 21 issue is anybody’s guess. Surely Article 21 – the right to life and personal liberty – is not horizontally applicable, because if it was, we might as well scrap the entire Indian Penal Code, which deals with exactly these kinds of issues – individuals violating each others’ rights to life and personal liberty. Nonetheless, the Court cited Kharak Singh, Gobind and Article 8 of the European Convention of Human Rights, further muddying the waters, because Article 8 – in contrast to American law – embodies a proportionality test for determining whether there has been an impermissible infringement of privacy. The Court then came up with the following observation:
“Where there is a clash of two Fundamental Rights, as in the instant case, namely, the appellant’s right to privacy as part of right to life and Ms. Akali’s right to lead a healthy life which is her Fundamental Right under Article 21, the RIGHT which would advance the public morality or public interest, would alone be enforced through the process of Court, for the reason that moral considerations cannot be kept at bay.”
With respect, this is utterly bizarre. If there is a clash of two rights, then that clash must be resolved by referring to the Constitution, and not to the Court’s opinion of what an amorphous, elastic, malleable, many-sizes-fit “public morality” says. The mischief caused by this decision, however, was replicated in Sharda v Dharmpal, decided by the Court in 2003. In that case, the question was whether the Court could require a party who had been accused of unsoundness of mind (as a ground for divorce under the wonderfully progressive Hindu Marriage Act) to undergo a medical examination – and draw an adverse inference if she refused. Again, whether this was a case in which Article 21 ought to be invoked is doubtful; at least, it is arguable, since it was the Court making the order. Predictably, the Court cited from Mr X v Hospital Z extensively. It cited Gobind (compelling State interest) and the ECHR (proportionality). It cited a series of cases involving custody of children, where various Courts had used a “balancing test” to determine whether the best interests of the child overrode the privacy interest exemplified by the client-patient privilege. It applied this balancing test to the case at hand by balancing the “right” of the petitioner to obtain a divorce for the spouse’s unsoundness of mind under the HMA, vis-à-vis the Respondent’s right to privacy.
In light of the above analysis, it is submitted that although the outcome in Mr X v Hospital Z and Sharda v Dharmpal might well be correct, the Supreme Court has misread what R. Rajagopal actually held, and its reasoning is deeply flawed. Neither of these cases are Article 21 cases: they are private tort cases between private parties, and ought to be analysed under private law, as Rajagopal itself was careful to point out. In private law, also, the balancing test makes perfect sense: there are a series of interests at stake, as the Court rightly understood, such as certain rights arising out of marriage, all of a private nature. In any event, whatever one might make of these judgments, one thing is clear: they are both logically and legally irrelevant to the Kharak Singh line of cases that we have been discussing, which are to do with the Article 21 right to privacy against the State.
NTIA to give up control of the Internet's root
As it noted in the NTIA's press release:
NTIA’s responsibility includes the procedural role of administering changes to the authoritative root zone file – the database containing the lists of names and addresses of all top-level domains – as well as serving as the historic steward of the [Domain Name System (DNS)]. NTIA currently contracts with [the Internet Corporation for Assigned Names and Numbers, ICANN] to carry out the Internet Assigned Numbers Authority (IANA) functions and has a Cooperative Agreement with Verisign under which it performs related root zone management functions. Transitioning NTIA out of its role marks the final phase of the privatization of the DNS as outlined by the U.S. Government in 1997.
This move was welcomed by "Internet technical leaders".
While this announcement cannot be said to be unexpected, it is nonetheless an important one and is also a welcome one. The NTIA seems to have foreclosed any option of the US government's role being performed by any government-led organization by noting in their press release, "NTIA will not accept a proposal that replaces the NTIA role with a government-led or an inter-governmental organization solution," once again reaffirming their belief in American exceptionalism: the NTIA could fulfil its role despite being a government, but now even a body involving multiple stakeholders can't replace the NTIA's role if it is going to be government-led.
Unfortunately, this announcement to relax American "stewardship" or "oversight" over some aspects of the Internet's technical functioning cannot restore the trust that has been lost due to actions taken by the US government and US companies. This new announcement won't change the US government's ability to 'tap' the Internet, nor will it affect their ability to unilaterally seize .com/.net/.name/.org/.edu/.tv/.cc/.us and other US-based domain names. Nor will a shift away from NTIA oversight lead to any of the chilling visions that some believe might lie in our future: the fears of the Association of National Advertisers and of some politicians and members of the US Congress is based on ignorance of what NTIA's role is.
The European Commission in a communiqué last month noted: "recent revelations of large-scale surveillance have called into question the stewardship of the U.S. when it comes to Internet governance". Unfortunately, the U.S. giving up that stewardship role will not prevent the continuation of their large-scale surveillance, just as the lack of such a stewardship role has not prevented other governments — U.K., India, Canada, Sweden, France, etc. — from engaging in large-scale surveillance.
There are three main benefits from the U.S. giving up this role.
-
First, it will put an end to the political illegitimacy of the U.S. government having a core authority in a global system, somehow making it first among equals;
-
Second, will focus light on ICANN, which under US oversight performs the IANA functions, and might, one hopes, lead to needed reform in ICANN's other functions;
-
Third, it will allow us to collectively move on from this dreaded political issue at the heart of Internet governance, which nevertheless is of little practical consequence if ICANN's accountability mechanisms are strengthened. As difficult as it may be, ICANN has to be accountable not just to one government or another but to the world, and ensuring that accountability to all doesn't become accountability to none, as NetChoice's Steve DelBianco put it, is the formidable task ahead of us.
Yet, all the ICANN reform in the world will still not lead to a less spied-upon, more open, and more equitable Internet.
Net Neutrality and Privacy
The principle behind net-neutrality, simply put, is that the data being transmitted to and from the user should be treated equally, i.e. that data carriage, at the level of ISP’s, should be ‘dumb’. This would mean that internet service providers cannot discriminate between different data based on the content of the data. Without the principle of net-neutrality being followed, ISP’s would become the ‘internet gatekeepers’, choosing what data gets to reach the end-user and how. There are many arguments for favouring or disfavouring net-neutrality, however, advocates of privacy on the internet should be wary of the possible implications of endorsing a non-neutral internet and allowing greater network management by ISP’s. So, how does the net-neutrality debate affect privacy?
It all depends upon what kind of network management ISP’s employ. Deep Packet Inspection (DPI) is a method of data inspection which allows the network manager to scrutinize data at the application level, and in real time. As compared to shallow packet inspection, which identifies based on headers like IP addresses or protocols like TCP and UDP, which are analogous to envelopes on a letter, DPI would be akin to having access to the contents. DPI-based network management can identify the programs, software and applications being used, and what they are being used for in real time. Unlike any ordinary online service provider ISP’s are in the unique position of having comprehensive access to all of their customers’ data. Allowing DPI-based network management for prioritizing certain data or applications, an almost certain outcome if net-neutrality is weakened, would mean that ISP’s would be able to intercept and scrutinize any and all user data, which would reveal substantial information about the user, and would be a serious blow to privacy. While DPI can have several benefits in its application (such as finding and fighting malware or viruses), but where it is used, must be for a targeted and legitimate aim. Even where DPI is not used, if network discrimination is allowed, based on a user-to-user basis it would require inspecting the IP addresses of the user, which can also be a problematic intrusion of privacy, especially since the ISP also has other data like addresses and names of users which it can use to identify them.
Privacy may not necessarily be affected through non-neutral internet systems, but in all probability, with the growth of systems like the DPI and commercial incentives for “gatekeeper ISP’s” who are in a position to profit greatly from an ability to scrutinize and discriminate between data, it is likely that it will. In India, though government ISP’s like MTNL and BSNL deny using DPI,[1] it’s likely that it is still applied by others, and that the government is aware of this (http://www.theinquirer.net/inquirer/news/2161541/indian-isps-block-104-websites). Even as the TRAI advocates and supports net-neutrality, Indian ISP’s seem to be heading the other way.[2] Before the trend becomes the norm, it’s high time for a comprehensive discussion about how policies should be framed for keeping the internet a more neutral, and more private, space.
References
- Apar Gupta, TRAI(ing) to keep it neutral, http://www.iltb.net/2010/09/traiing-keep-it-neutral/
- For a lay discussion on Deep Packet Inspection and net-neutrality, visit http://arstechnica.com/gadgets/2007/07/deep-packet-inspection-meets-net-neutrality/
New Standard Operating Procedures for Lawful Interception and Monitoring
Even as the Central Government prepares the Central Monitoring System for the unrestricted monitoring of all personal communication, the Department of Telecom has issued new guidelines for Telecom Service Providers to assist in responding to requests for interception and monitoring of communications from security agencies.
These guidelines do not appear to be publicly accessible, but according to news items, under the “Standard Operating Procedures for Lawful Interception and Monitoring of Telecom Service Providers”, the TSP’s must now provide for lawful interception and monitoring requests for voice calls, Short message Service (SMS), General Packet Radio Service (GPRS) and Value Added Service (VAS) including Multi Message Service (MMS), data and voice in 3G/4G/Long Term Evolution (LTE) including video call or Voice Over Internet protocol (VoIP). This move comes just days after the Home Ministry suggested that the Department of Telecom either change the rules under their Telecom Policies such as the Unified Access Service Licence (UASL) to include VoIP monitoring, or, drastically, block all VoIP services on the internet, which would include several communication applications including Skype and GTalk. (See the article published by Economic Times).
The guidelines will supposedly also provide for some basic safeguards to ensure that non-authorized interception does not take place, such as ensuring that the interception is only to be provided by the Chief Nodal Officer of a TSP and only upon the issue of an order by the Home Secretary at the Central or State Government. Furthermore, these requests must only be in written, in untampered and sealed envelopes with no overwriting, etc. and bearing the order number issued by the concerned Secretary, with the date of the order. However, in exigent circumstances the order may be provided by email, provided that the physical copy is sent within two days of the order, else the interception order must be terminated. Inquiry processes are detailed under the new SOP’s which can verify whether the request was in original and addressed to the Nodal Officer and from which designated security agency it was issued, and can also verify the issue of an acknowledgment of compliance of the order by the TSP within two days of its receipt. The new guidelines also clarify the issue of interception of roaming subscribers by the State Government where the subscriber is registered. According to the guidelines, an order by the government of the state where such a caller has registered is sufficient and does not need vetting by the Home Secretary at the centre.
Notwithstanding the additional “safeguards” against unlawful or unauthorized interception, the message to take away from these guidelines is the Government’s continued efforts to expand its surveillance regime to comprehensively monitor every action and every communication at its whim. These requests for monitoring, undertaken by “security agencies” which include taxation agencies and the SEBI, are flawed not merely because of the possibility of “unauthorized” interception, rather because the legal basis of the interception is vague, broad and widely susceptible to misuse, as the recent “snoopgate” allegations against the Gujarat government have shown. (See the article published by the Hindu).
The current regime, based on a wide interpretation of Section 5(2) of the Indian Telegraph Act and the telecom policies of the Department of Telecom, do not have adequate safeguards for preventing misuse by those in power – such as the requirement of reasonable suspicion or a warrant. Without a sound legal basis for interception, which protects the privacy rights of individuals, any additional safeguards are more or less moot, since the real threat of intrusive surveillance and infringing of basic privacy exists regardless of whether it is done under the seal of the Home Secretary or not.
Resources
Privacy worries cloud Facebook's WhatsApp Deal
Read the original published in the Economic Times on March 14, 2014
Activists have five main concerns.
- Facebook has a track record of not keeping its promises to users.
- The ethos of both companies when it comes to privacy is diametrically opposite.
- The probability that WhatsApp messages and content will be intercepted because of Facebook's participation in NSA's PRISM spying programme.
- Facebook slurping WhatsApp's large repository of phone numbers.
- Two hundred trackers already monitor your internet use when you are not using Facebook and now they tracking mobile use much more granularly. This week the Indian competition regulator (CCI) also told the media that the acquisition would be subject to scrutiny. However, unlike the US regulator the Indian regulator does not have the mandate to examine the acquisition from a privacy perspective.
LIRNEAsia research in Indonesia paints a very similar picture to one we have in India. When Indonesian mobile phone users were asked if they used Facebook they answered in affirmative. Then the very same users were asked if they used the internet and they replied in negative. A large number of Facebook users in these other similar economies are trapped within what are called "walled gardens."
Walled gardens allow mobile phone subscribers without data connections to get access to a single over-the-top service provider like Facebook because their telcom provider has an arrangement. Software such as Facebook on every phone makes it possible for feature phone users to also enter the walled garden.
According to Facebook it "is a fast and easyto-use native app that works on more than 3,000 different types of feature phones from almost every handset manufacturer that exists today."
Unlike North American and European users of Facebook - who freely roam the "world wild web" and then choose to visit Facebook when they want to many Indian users will first experience data services in a domesticated fashion within a walled garden.
Whether or not they will wander in the wild when they are have full access to the internet remains to be seen. But given our poor rates of penetration, dogmatic insistence on network neutrality at this early stage of internet adoption may not be the right way to maximise welfare and consumer interest.
Fortunately for Facebook and unfortunately for us, India still does not have a comprehensive data protection or horizontal privacy law. The Justice AP Shah Committee that was constituted by the Planning Commission in October 2012 recommended that the Privacy Act articulate national privacy principles and establish the office of the Privacy Commissioner. It further recommended that data protection and surveillance be regulated for both the private sector and the state.
Since then the Department of Personnel and Training has updated the draft bill to implement these recommendations and has been working towards consensus within government.
Since we still don't have our own privacy regulator we will have to depend on foreign data protection authorities and privacy commissioners to protect us from the voracious appetite for personal data of over-the-top service providers like Facebook This is woefully insufficient because they will not act on harm caused to Indian consumers or be aware of how Facebook acts differently in the Indian market.
As we approach the first general election in India when social media will play a small but influential role it would have been excellent if we had someone to look out for our right to privacy.
India's Internet Jam
The article was published in Index on Censorship in August 2012. This is an unedited version of the article.
In a matter of three days, in August 2012, India’s central government ordered internet service providers to block around 309 pieces of online content – mostly individual web pages, YouTube videos and Facebook groups. The blocking orders came days after people originally from north-eastern India living in Bangalore began fleeing the city in fear of attack. Rumours that some Muslims in the city were planning violence in retaliation for recent clashes between the indigenous Bodo tribe and Muslim settlers in Assam spread quickly via text messages and through the media. The Nepali migrant community in Bangalore also received text messages from their families, warning them that they might be mistaken for north-eastern Indians and also be targeted. Indian Railway, catering to the huge demand, organised special trains to Assam for the crowds of people.
Freedom of speech is enshrined in the Constitution of India, which came into force in 1952, and specifically in Article 19(1)(a), which guarantees that ‘all citizens shall have the right to freedom of speech and expression’. While in the United States, it wasn’t until the 1920s that the Supreme Court struck down a law or governmental action on freedom of speech grounds, in India, just one year after the constitution was adopted, government actions against both left- and right-wing political speech were struck down for violating Article 19(1)(a). Enraged, the Congress government then amended Article 19, expanding the list of restrictions to the right to free expression. These included speech pertaining to ‘friendly relations with foreign states’, ‘public order’ and ‘incitement to an offence’. In 1963, in response to the 1962 war with China, the ‘sovereignty and integrity of India’ was also added, taking the number of categories of permissible restrictions up to eight. While the constitution categorically stipulates that no further restrictions should be imposed, courts have on occasion added to the list (privacy, for instance) through judicial interpretation without explicitly stating that they are doing so. Comparisons are often drawn between the constitution’s ‘reasonable restrictions’ and the categorical prohibition enshrined in the US Constitution’s First Amendment: ‘Congress shall make no law … abridging the freedom of speech, or of the press’ – a meaningless comparison as there are indeed many categories of speech that are seen as being protected under the US constitution and even speech that is protected may be restrained in a number of ways.
Today, there are a number of laws that regulate freedom of speech in India, from the Indian Penal Code (IPC), the Victorian legislation meant to codify crimes, to the Information Technology Act, which was amended in 2008 and in some cases makes behaviour that is perfectly legal offline into a criminal activity when online.
Sedition and social harmony
The Indian Penal Code criminalises sedition; speech intended to cause enmity between communities; speech intended to ‘outrage religious feelings of any class’; selling, singing or displaying anything obscene; and defamation. It also prohibits ‘causing someone, by words or gestures, to believe they’re the target of divine displeasure’. Each of these provisions has been misused, as there are indeed many catagories of speech that are not seen as being protected under thw US constitution, and even speech that is protected may be restrained in a number of ways.
In recent years, sedition charges have been brought against human rights activists (Binayak Sen and Arundhati Roy), journalists (Seema Azad), cartoonists (Aseem Trivedi) and protesters (thousands of villagers in Koodankulam and neighbouring villages who demonstrated against a nuclear reactor in their area). It is usually the higher judiciary that dismisses such cases, while the lower judiciary seems to be supplicant to the bizarre claims of government, the police and complainants. Similarly, the higher judiciary has had to intervene in cases where books and films have been banned for ‘causing enmity between communities’ or for intentionally hurting the sentiments of a religious group.
Of the last six books banned by the Maharashtra government, all but one (RV Bhasin’s Islam: A Concept of Political World Invasion by Muslims) have been overturned by the Mumbai High Court. In one case, the court criticised the government for using a violent protest (organised by the Sambhaji Brigade, one of many right-wing political groups that frequently stage demonstrations) as reason enough for banning an academic book on the Maratha king Shivaji. In its decision, the judge pointed out that it is the government’s job to provide protection against such violence. Given India’s history of communal violence there is indeed a need for the law to address incitement to violence – but these laws should be employed at the actual time of incitement, not after the violence has already taken place. But, as recent events have shown, the government is willing to censor ‘harmful’ books and films and less likely to take action against individuals who incite violence during demonstrations.
Online speech and the law
There are regular calls for the government to introduce legislation that deals specifically with online behaviour, despite the fact that the vast majority of the laws regarding sedition and social harmony apply online as well as offline. One example is the recent move to introduce amendments to the Indecent Representation of Women Act (1986) so that it applies to ‘audiovisual media and material in electronic form’.
But the government’s attempts to control online speech began long before the introduction of any internet-specific legislation. Indeed, when state-monopoly internet service provider VSNL censored content, it did so under the terms of a contract it had entered with its customers, not under any law. In 1998, a mailing list called Middle East Socialist Network was blocked on national security grounds. In 1999, Pakistani newspaper Dawn’s website was blocked during the Kargil conflict. In both of the latter cases, the government relied on the Indian Telegraph Act (1885) to justify its actions, though that act contains no explicit provisions for such censorship.
In 2000, the Information Technology (IT) Act was passed and the Indian Computer Emergency Response Team (CERT-In) was created, which (unlawfully) assumed the role of official online censor. Importantly, while the IT Act did
make the publication of obscene content online illegal (though it already was under the IPC), it did not grant permission for authorities to block websites. Despite this, an executive order passed on 27 February 2003 granted CERT-In the power to block. Had this been challenged in a court, it may well have been deemed unconstitutional since, in the absence of a statutory law, an executive order cannot reverse the freedom granted under Article 19. And although the telecommunications sector in India was being liberalised around this time, as part of their licence agreements, all internet service providers (ISPs) have to agree to block links upon being requested to do so by the government. In 2008, when the IT Act was amended, it clearly stated that the government can block websites not only when it deems it necessary to do so but also when it is deemed expedient in relation to matters of public interest, national security and with regard to maintaining friendly relations with foreign states. The power to block does not, however, extend to obscenity or defamation offences. At the same time, further categories of speech crimes were introduced, along with other new offences, including the electronic delivery of ‘offensive messages through communication services’ or anything ‘for the purpose of causing annoyance or inconvenience’. This has often been abused, including by the chief minister of West Bengal, who issued proceedings against a professor for forwarding an email containing a cartoon that mocked him. Under this draconian and unconstitutional provision, the police do not need an arrest warrant and the punishment can be as much as three years’ imprisonment, longer than even the punishment for causing death by negligence. The amendment also granted the government extensive powers to monitor and intercept online speech and data traffic, greatly extending the powers provided under colonial laws such as the Indian Telegraph Act (1885). As legislation has been introduced, the penalties for online offences have increased significantly. For example, the penalty for the first-time publication of an obscene ebook is up to five years in prison and a 1,000,000 rupee (US$18,800) fine, compared with two years’ imprisonment and a 2,000 rupee (US$38) fine as stipulated in the IPC for publishing that same material in print version. New laws introduced in 2009 pertain specifically to blocking (section 69a), interception, decryption and monitoring (69 and 69b) and are in accordance with the constitution. However, the amendments were brought in without any attempt at transparency or accountability.
Power in the hands of intermediaries
In April 2011, despite critical submissions received during its public consultation, the government announced new ‘intermediary guidelines’ and ‘cyber cafe rules’, both of which have adverse effects on freedom of expression. The rules, which were issued by the Department of Information and Technology (DIT), grant not only the government but citizens significant powers to censor the internet. They require all intermediaries – companies that handle content, including web hosts, telecom companies, domain name providers and other such intermediaries – to remove ‘disparaging’ content that could ‘harm minors in any way’. They prohibit everything from jokes (if the person sharing the joke does not own copyright to it) to anything that is disparaging. In a recent case, in December 2011, thousands of people used the hashtag #=IdiotKapilSibal on Twitter to criticise the minister of communications and information technology, Kapil Sibal, who had requested that officials from Google, Microsoft, Yahoo! and Facebook in India pre-screen online content. These guidelines and rules are badly drafted and unconstitutional, as they go beyond the limits allowed under Article 19 in the constitution. And do so in a manner that lacks any semblance of due process and
fairness. They are inconsistent with offline laws, too: for example, because the guidelines also refer to gambling, the government of Sikkim can publish advertisements for its PlayWin lottery in newspapers but not online. It’s far easier to persuade officials to remove online material than it is to persuade them to remove books from a bookstore or artwork from a gallery. Police are only empowered to seize books if the government or a court has been persuaded that it violates a law and issues such an order. This fact is always recorded, in government or legal records, police files or in the press. By contrast, web content can be removed on the basis of one email complaint; intermediaries are required to ‘disable’ the relevant content within 36 hours of the complaint. A court order is not required, nor is there a requirement to notify the owner of the content that a complaint has been received or that material has been removed. The effect is that of almost invisible censorship.
This assertion – that it only takes one complaint – may seem far-fetched. But a researcher from the Centre for Internet and Society sent complaints to several intermediaries on a number of occasions, resulting in content being removed in a majority of cases. If intermediaries choose not to take action, they risk losing their immunity against punishment for content. In essence, the law is the equivalent of punishing a post office for the letters that people send via the postal service.
| The amendments were brought in without any attempt at transparency or accountability |
In 1984, Indira Gandhi was forced to sue Salman Rushdie for defamation in a London court in order to ensure one sentence was expurgated from his novel Midnight’s Children. Today Gandhi wouldn’t need to win a lawsuit against publishers. She would merely have to send a complaint to websites selling the book and it would have to be removed from sale. It is easier to block Akbari.in – the online newspaper run by Vinay Rai, who filed a criminal complaint against multiple internet companies in December 2011 for all manner of materials – than it is to prevent its print publication. There is no penalty for frivolous complaints, such as those sent by researchers from the Centre for Internet and Society, nor is there any requirement for records to be kept of who has removed what. Such great powers of censorship without any penalties for abuse of these powers are a sure-fire way of moving towards greater intolerance, with the internet – that republic of opinions and expressions – being a casualty.
Censorship outside the law
Since 2011, governments and private companies alike have increasingly engaged in internet censorship. In April 2011, in response to a right to information request, the DIT released a list of 11 websites that had been officially blocked under the IT Act since 2009, when the amended act came into force. But, according to a recent Google Transparency Report, government requests for the removal of material far exceeds that number. The report reveals that the government (including state governments) requested that Google remove 358 items from January 2011 to June 2011. Of this number, only eight were considered to be hate speech and only one item was related to concerns over national security. The remaining material, 255 items (71 per cent of all requests), was taken down because of ‘government criticism’. Criticism of the government is protected under the country’s constitution but, nonetheless, Google complied with take-down requests 51 per cent of the time. It’s clear, then, that governmental censorship is far more widespread than officially acknowledged.
In July 2011, Reliance Entertainment obtained a ‘John Doe’ order to protect its intellectual property rights with regard to its film Singham, which was scheduled for release that month. The order prohibited both online and offline infringement of copyright for the film and was sent to a number of ISPs, which then blocked access to file-sharing websites, even though there was no proof of the film having been available on any of them. According to Reliance Entertainment, they merely asked ISPs ‘not to make the film available’ on their networks, even though the order did not authorise it. But a right to information request pertaining to a similar case dealing with the distribution of the film Dhammu showed that the entertainment company’s lawyers had in fact asked for dozens of websites – not just deep-link URLs to infringing content – to be blocked, despite publicly claiming otherwise. If web users encountered any information at all about why access to the sites was blocked, it was that the Department of Telecom had ordered the blocking, which was plainly untrue. In February 2012, following a complaint from the Indian Music Industry (a consortium of 142 music companies), the Calcutta High Court ordered 387 ISPs to block 107 websites for music piracy. At least a few of those, including Paktimes.com and Filmicafe.com, were general interest entertainment sites. The most famous of these sites, Songs.pk, re-emerged shortly after the block as Songspk.pk, highlighting the pointlessness of the block. And outside the realm of copyright, in December 2011, the domain name CartoonsAgainstCorruption.com was suspended based on an unlawful complaint from the Mumbai police requesting its suspension, despite there being no powers for them to do so under any law.
Between August and November 2011, the DIT also went to great efforts to compel big internet companies including Indiatimes, Facebook, Google, Yahoo!, and Microsoft, to ‘self-regulate’. This revealed the department’s desire to gain ever greater powers to control ‘objectionable’ content online, effectively bypassing the IT Act. It’s obvious, too, that by encouraging internet companies to ‘self-regulate’ the government will avoid embarrassing statistics such as those revealed by Google’s Transparency Report.
New dangers
A way forward, at least for internet-specific laws, could be to rekindle the Cyber Regulations Advisory Committee – a multi-stakeholder committee required by the IT Act – and to practise at home what we preach abroad on matters of internet governance: the value of a multi-stakeholder system, which includes industry, academia and civil society and not just governments. The idea of a multi-stakeholder framework has gained prominence since it was placed at the core of the ‘Declaration of Principles’ at the first World Summit on Information Society in Geneva in 2003. It has also been at the heart of India’s pronouncements at the Internet Governance Forum and the India-Brazil-South Africa Dialogue Forum. The Internet Governance Division, which formulates the country’s international stance on internet governance, has long recognised that these decisions must be taken in an open and collaborative manner. It is time the DIT’s Cyber-Law and ESecurity Group, which formulates the country’s national stance on the internet, realises the same.
Freedom of speech means nothing in a democratic society if it does not allow everyone to speak. Despite the internet being a very elite space, the number of people who have used it to express themselves since its introduction in India in 1994 is vast, especially when compared to the number of people in India who have expressed themselves in print since 1947 when the country won its independence. Online speech is indeed a big shift from edited and usually civil discussions in the world of print media. Perhaps this gives us some indication of why there is some support among the mass media for government regulations on speech. Too many discussions of online speech laws in India descend into arguments about the lack of civility online. However, the press – and all of us – would do well to remember that civility and decency in speech, while desirable in many contexts, cannot be the subject of legislation. But in India, the greatest threat to freedom of expression is not a government clampdown on dissent but threats from political and corporate powers with a range of tools at their disposal, including fostering a climate of selfcensorship. The government has passed bad laws that have given way to private censorship. And many of these laws are simply a result of gross ineptitude.
We cannot take sufficient comfort in the fact that, in India, censorship is limited and nowhere on the scale that it is in China or Iran. It is crucial that, from a legal, cultural and technological standpoint we do not open the door for further censorship. And currently, we are failing.
Pranesh Prakash is Policy Director at the Centre for Internet and Society in Bangalore. Part of this article appeared in a blog by the author on the centre’s website, cis-india.org, in January 2012
Leaked Privacy Bill: 2014 vs. 2011
Note: After obtaining a copy of the leaked Privacy Bill 2014, we have replaced the blog "An Analysis of the New Draft Privacy Bill" which was based off of a report from the Economic Times, with this blog post.
This represents the third leak of potential privacy legislation for India that we know of, with publicly available versions having leaked in April 2011 and September 2011.
When compared to the September 2011 Privacy Bill, the text of the 2014 Bill includes a number of changes, additions, and deletions. Below is an outline of significant changes from the September 2011 Privacy Bill to the 2014 Privacy Bill:
- Scope: The 2014 Bill extends the right to Privacy to all residents of India. This is in contrast to the 2011 Bill, which extended the Right to Privacy to citizens of India. The 2014 Bill furthermore recognizes the Right to Privacy as a part of Article 21 of the Indian Constitution and extends to the whole of India, whereas the 2011 Bill did not explicitly recognize the Right to Privacy as being a part of Article 21, and excluded Jammu and Kashmir from its purview.
- Definitions: The 2014 Bill includes a number of new definitions, redefines existing terms, and deletes others.
Terms that have been added in the 2014 Bill and the definitions
- Personal identifier: Any unique alphanumeric sequence of members, letters, and symbols that specifically identifies an individual with a database or a data set.
- Legitimate purpose: A purpose covered under this Act or any other law for the time being in force, which is certain, unambiguous, and limited in scope for collection of any personal data from a data subject.
- Competent authority : The authority which is authorized to sanction interception or surveillance, as the case may be, under this Act or rules made there under or any other law for the time being in force.
- Notification: Notification issued under this Act and published in the Official Gazette
- Control : And all other cognate forms of expressions thereof, means, in relation to personal data, the collection or processing of personal data and shall include the ability to determine the purposes for and the manner in which any personal data is to be collected or processed.
- Telecommunications system: Any system used for transmission or reception of any communication by wire, radio, visual or other electromagnetic means but shall not include broadcasting services.
- Privacy standards: The privacy standards or protocols or codes of practice. developed by industry associations.
Terms that have been re-defined in the 2014 Bill from the 2011 Bill and the 2014 Bill definitions
- Communication data:The data held or obtained by a telecommunications service provider in relation to a data subject including the data usage of the telecommunications
- Data subject : Any living individual, whose personal data is controlled by any person
- Interception: In relation to any communication in the course of its transmission through a telecommunication system, any action that results in some or all of the contents of that communication being made available, while being transmitted, to a person other than the sender or the intended recipient of the communication.
- Person: Any natural or legal person and shall include a body corporate, partnership, society, trust, association of persons, Government company, government department, urban local body, or any other officer, agency or instrumentality of the state.
- Sensitive personal data: Personal data relating to: (a) physical and mental health including medical history, (b) biometric, bodily or genetic information, (c) criminal convictions (d) password, (e) banking credit and financial data (f) narco analysis or polygraph test data, (g) sexual orientation. Provided that any information that is freely available or accessible in public domain or to be furnished under the Right to Information Act 2005 or any other law for time being in force shall not be regarded as sensitive personal data for the purposes of this Act.
- Individual: a resident of Indian
- Covert surveillance: covert Surveillance" means obtaining private information about an individual and his private affairs without his knowledge and includes: (i) directed surveillance which is undertaken for the purposes of specific investigation or specific operation in such a manner as is likely to result in the obtaining of private information about a person whether or not that person was specifically identified in relation to the investigation or operation; (ii) intrusive surveillance which is carried out by an individual or a surveillance device in relation to anything taking place on a residential premise or in any private vehicle. It also covers use of any device outside the premises or a vehicle wherein it can give information of the same quality and detail as if the device were in the premises or vehicle; (iii) covert human intelligence service which is information obtained by a person who establishes or maintains a personal or other relationship with an individual for the covert purpose of using such a relationship to obtain or to provide access to any personal information about that individual
- Re-identify: means the recovery of data from an anonymised data, capable of identifying a data subject whose personal data has been anonymised;
- Process: “process" and all other cognate forms of expressions thereof, means any operation or set of operations, whether carried out through automatic means or not by any person or organization, that relates to:(a) collation, storage, disclosure, transfer, updating, modification, alteration or use of personal data; or (b) the merging, linking, blocking, degradation or anonymisation of personal data;
- Direct marketing: Direct Marketing means sending of a commercial communication to any individual
- Data controller: any person who controls, at any point in time, the personal data of a data subject but shall not include any person who merely provides infrastructure for the transfer or storage of personal data to it data controller;
- Government: the Central Government or as the case may be, the State Government and includes the Union territory Administration, local authority or any agency and instrumentality of the Government;
Terms that have been removed from the 2014 Bill that were in the 2011 Bill and the 2011 definition:
- Consent: Includes implied consent
- Maintain: Includes maintain, collect, use, or disseminate.
- Data processor: In relation to personal data means any person (other than the employee of the data controller), who processes the data on behalf of the data controller.
- Local authority: A municipal committee, district board, body of port commissioners, council, board or other authority legally entitled to, or entrusted by the Government with, the control or management of a municipal or local fund.
- Prescribed: Prescribed by rules made under this Act.
- Surveillance: Surveillance undertaken through installation and use of CCTVs and other system which capture images to identify or monitor individuals (this was removed from the larger definition of surveillance.)
- DNA: Cell in the body of an individual, whether collected from a cheek, cell, blood cell, skin cell or other tissue, which allows for identification of such individual when compared with other individual.
Terms that have remained broadly (with some modification) the same between the 2014 Bill and 2011 Bill (as per the 2014 Bill definition):
- Authority: The Data Protection Authority of India
- Appellate tribunal: the Cyber Appellate Tribunal established under Sub-Section (1) of section n48 of the Information Technology Act, 2000.
- Personal data: Any data which relates to a data subject, if that data subject can be identified from that data, either directly or indirectly, in conjunction with other data that the data controller has or is likely to have and includes any expression of opinion about such data subject.
- Member: Member of the Authority
- Disclose: and all other cognate forms of expression thereof, means disclosure, dissemination, broadcast, communication, distribution, transmission, or make available in any manner whatsoever, of personal data.
- Anonymised: The deletion of all data that identifies the data subject or can be used to identify the data subject by linking such data to any other data of the data subject, by the data controller.
- Exceptions to the Right to Privacy: According to the 2011 Bill, the exceptions to the Right to Privacy included:
- Sovereignty, integrity and security of India, strategic, scientific or economic interest of the state
- Preventing incitement to the commission of any offence
- Prevention of public disorder or the detection of crime
- Protection of rights and freedoms of others
- In the interest of friendly relations with foreign state
- Any other purpose specifically mentioned in the Act.
The 2014 Bill reflects almost all of the exceptions defined in the 2011 Bill, but removes ‘detection of crime’ from the list of exceptions. The 2014 Bill also qualifies that the application of each exception must be adequate, relevant, and not excessive to the objective it aims to achieve and must be imposed on the manner prescribed – whereas the 2011 Bill stated only that the application of exceptions to the Right to Privacy cannot be disproportionate to the purpose sought to be achieved.
- Acts not to be considered deprivations of privacy: The 2011 Bill lists five instances that will not be considered a deprivation of privacy - namely
- For journalistic purposes unless it is proven that there is a reasonable expectation of privacy,
- Processing data for personal or household purposes,
- Installation of surveillance equipment for the security of private premises,
- Disclosure of information via the Right to Information Act 2005,
- And any other activity exempted under the Act.
The 2014 limits these instances to:
- The processing of data purely for personal or household purposes,
- Disclosure of information under the Right to Information Act 2005,
- And any other action specifically exempted under the Act.
- Privacy Principles: Unlike the 2011 Bill, the 2014 Bill defines nine specific privacy principles: notice, choice and consent, collection limitation, purposes limitation, access and correction, disclosure of information, security, openness, and accountability. The Privacy Principles will apply to all existing and evolving practices.
- Provisions for Personal Data: Both the 2011 Bill and the 2014 Bill have provisions that apply to the processing of personal and sensitive personal data. The 2011 Bill includes provisions addressing the:
- Collection of personal data,
- Processing of personal data,
- Data quality,
- Provisions relating to sensitive personal data,
- Retention of personal data,
- Sharing (disclosure) of personal data,
- Security of personal data,
- Notification of breach of security,
- Access to personal data by data subject,
- Updation of personal data by data subject
- Mandatory processing of data,
- Trans border flows of personal data.
Of these, the 2014 Bill broadly (though not verbatim) reflects the 2011 Bill provisions relating to the:
- Collection of personal data,
- Processing of personal data,
- Access to personal data,
- Updating personal data
- Retention of personal data
- Data quality,
The 2014 Bill has further includes provisions addressing:
- Openness and accountability,
- Choice,
- Consent,
- Exceptions for personal identifiers.
The 2014 Bill has made changes to the provisions addressing:
- Provisions relating to sensitive personal data,
- Sharing (disclosure of personal data),
- Notification of breach of security,
- Mandatory processing of data
- Security of personal data
- Trans border flows of personal data.
The changes that have been made have been mapped out below:
Provisions Relating to Sensitive Personal Data: The 2011Bill and 2014 Bill both require authorization by the Authority for the collection and processing of sensitive personal data. At the same time, both Bills include a list of circumstances under which authorization for the collection and processing of sensitive personal data is not required. On the whole, this list is the same between the 2011 Bill and 2014 Bill, but the 2014 Bill adds the following circumstances on which authorization is not needed for the collection and processing of sensitive personal data:
- For purposes related to the insurance policy of the individual if the data relates to the physical or mental health or medical history of the individual and is collected and processed by an insurance company.
- Collected or processed by the Government Intelligence agencies in the interest of the sovereignty, integrity, security or the strategic, scientific or economic interest of India.
The 2014 Bill also allows the Authority to specify additional regulations for sensitive personal data, and requires that any additional transaction sought to be performed with the sensitive personal information requires fresh consent to first be obtained. The 2014 Bill carves out another exception for Government agencies, allowing disclosure of sensitive personal data without consent to Government agencies mandated under law for the purposes of verification of identity, or for prevention, detection, investigation including cyber incidents, prosecution, and punishment of offences.
Notification of Breach of Security: The provisions relating to the notification of breach of security in the 2014 Bill differ from the 2011 Bill. Specifically, the 2014 Bill removes the requirement that data controllers must publish information about a data breach in two national news papers. Thus, in the 2014 Bill, data controllers must only inform the data protection authority and affected individuals of the breach.
Notice: The 2014 Bill changes the structure of the notice mechanism – where in the 2011 Bill, prior to the processing of data, data controllers had to take all reasonable steps to ensure that the data subject was aware of the following:
- The documented purposes for which such personal data is being collected
- Whether providing of personal data by the data subject is voluntary or mandatory under law or in order to avail of any product or service
- The consequences of the failure to provide the personal data
- The recipient or category of recipients of the personal data
- The name and address of the data controller and all persons who are or will be processing information on behalf of the data controller
- If such personal data is intended to be transferred out of the country, details of such transfer.
In contrast the 2014 Bill provides that before personal data is collected, the data controller must give notice of:
- What data is being collected and
- The legitimate purpose for the collection.
If the purpose for which the data was collected has changed the data controller will then be obligated to provide the data subject with notice of:
- The use to which the personal data will be put
- Whether or not the personal data will be disclosed to a third party and if so the identity of such person
- If the personal data being collected is intended to be transferred outside India and the reasons for doing so, how the transfer helps in achieving the legitimate purpose and whether the country to which such data is transferred has suitable legislation to provide for adequate protection and privacy of the data.
- The security and safeguards established by the data controller in relation to the personal data
- The processes available to a data subject to access and correct his personal data
- The recourse open to a data subject, if he has any complaints in respect of collection or processing of the personal data and the procedure relating thereto
- The name, address, and contact particulars of the data controller and all persons who will be processing the personal data on behalf of the data controller.
Disclosure of personal data: Though titled as ‘sharing of personal data’ both the 2011 Bill and 2014 Bill require consent for the disclosure of personal information, but list exceptional circumstances on which consent is not needed. In the 2011 bill, the relevant provision permits disclosure of personal data without consent only if (i) the sharing was a part of the documented purpose, (ii) the sharing is for any purpose relating to the exceptions to the right to privacy or (iii) the Data Protection Authority has authorized the sharing. In contrast, the 2014 Bill permits disclosure of personal data without consent if (i) such disclosure is part of the legitimate purpose (ii) such disclosure is for achieving any of the objectives of section 5 (iii) the Authority has by order authorized such disclosure (iv) the disclosure is required under any law for the time being in force (v) the disclosure is made to the Government Intelligence agencies in the interest of the sovereignty, integrity, security or the strategic, scientific or economic interest of India. As a safeguard, the 2014 Bill requires that any person to whom personal information is disclosed, whether a resident or not, must adhere to all provisions of the Act. Furthermore, the disclosure of personal data must be limited to the extent which is necessary to achieve the purpose for which the disclosure is sought and no person can make public any personal data that is in its control.
Transborder flow of information: Though both the 2011 Bill and the 2014 Bill require any country that data is transferred to must have equivalent or stronger data protection standards in place, the 2014 Bill carves out an exception for law enforcement and intelligence agencies and the transfer of any personal data outside the territory of India, in the interest of the sovereignty, integrity, security or the strategic, scientific or economic interest of India.
Mandatory Processing of Data: Both the 2011 Bill and 2014 Bill have provisions that address the mandatory processing of data. These provisions are similar, but the 2014 Bill includes a requirement that data controllers must anonymize personal data that is collected without prior consent from the data subject within a reasonable time frame after collection.
Security of Personal Data: The provision relating to the security of personal information in the 2014 Bill has been changed from the 2011 Bill by expanding the list and type of breaches that must be prevented, but removing requirements that data controllers must ensure all contractual arrangements with data processors specifically ensure that the data is maintained with the same level of security.
- Conditions on which provisions do not apply: Both the 2011Bill and 2014 Bill define conditions on which the provisions of updating personal data, access, notification of breach of security, retention of personal data, data quality, consent, choice, notice, and right to privacy will not apply to personal data. Though the 2011 Bill and 2014 Bill reflect the same conditions, the 2014 Bill carves out an exception for Government Intelligence Agencies - stating that the provisions of updating personal data, access to data by the data subject, notification about breach of security, retention of personal data, data quality, processing of personal data, consent, choice, notice, collection from an individual will not apply to data collected or processed in the interest of the sovereignty, integrity, security or the strategic, scientific or economic interest of India.
- Privacy Officers: Unlike the 2011 Bill, the 2014 Bill defines the role of the privacy officer that must be established by every data controller for the purpose of overseeing the security of personal data and implementation of the provisions of the Act.
- Power of Authority to Exempt: Both the 2011 Bill and 2014 Bill contain provisions that enable the Authority to waive the applicability of specific provisions of the Act. The circumstances on which this can be done are based on the exceptions to the Right to Privacy in both the 2011 and 2014 Bill. To this extent, the 2014 Bill differs slightly from the 2011 Bill, by removing the power of the Authority to exempt for the ‘detection of crime’ and ‘any other legitimate purpose mentioned in this Act’ .
- The Data Protection Authority: The 2011 Bill and 2014 Bill both establish Data Protection Authorities, but the 2014 Bill further clarifies certain aspects of the functioning of the Authority and expands the functions and the powers of the Authority. For example, new functions of the Authority include:
- Auditing any or all personal data controlled by the data controller to assess whether it is being maintained in accordance with the Act,
- Suggesting international instruments relevant to the administration of the Act,
- Encouraging industry associations to evolve privacy standards for self regulations, adjudicating on disputes arising between data controllers or between individuals and data controllers.
The 2014 Bill also expands the powers of the Data Protection Authority – importantly giving him the power to receive, investigate complaints about alleged violations of privacy and issue appropriate orders or directions.
At the same time, the 2014 Bill carves out an exception for Government Intelligence Agencies and Law Enforcement agencies – preventing the Authority from conducting investigations, issuing appropriate orders or directions, and adjudicating complaints in respect to actions taken by the Government Intelligences Agencies and Law Enforcement, if for the objectives of (a) sovereignty, integrity or security of India; or(b) strategic, scientific or economic interest of India; or(c) preventing incitement to the commission of any offence, or (d) prevention of public disorder, or(e) the investigation of any crime; or (f) protection of rights and freedoms of others; or (g) friendly relations with foreign states; or (h) any other legitimate purpose mentioned in this Act.
This power is instead vested with a court of competent jurisdiction.
- The National Data Controller Registry: The 2014 Bill removes the National Data Controller Registry and requirements for data controllers to register themselves and oversight of the Registry by the Data Protection Authority.
- Direct Marketing: Both the 2011 and 2014 Bills contain provisions regulating the use of personal information for direct marketing purposes. Though the provisions are broadly the same, the 2011 Bill envisions that no person will undertake direct marketing unless he/she is registered in the ‘National Data Registry’ and one of the stated purposes is direct marketing. As the 2014 Bill removes the National Data Registry, the 2014 Bill now requires that any person undertaking direct marketing must have on record where he/she has obtained personal data from.
- Interception of Communications: Though maintaining some of the safeguards defined in the 2011 Bill for interception, 2014 Bill changes the interception regime envisioned in the 2011 Bill by carving out a wide exception for organizations monitoring the electronic mail of employees, removing provisions requiring the interception take place only for the minimum period of time required for achieving the purposes, and removing provisions excluding the use of intercepted communications as evidence in a court of law. Similar to the 2011 Bill, the 2014 Bill specifies that the principles of notice, choice and consent, access and correction, and openness will not apply to the interception of communications.
- Video Recording Equipment in public places: Unlike the 2011 Bill, which addressed only the use of CCTV’s, the 2014 Bill addresses the installation and use of video recording equipment in public places. Though both the 2011 Bill and 2014 Bill both prevent the use of recording equipment and CCTVs for the purpose of identifying an individual, monitoring his personal particulars, or revealing personal, or otherwise adversely affecting his right to privacy - the 2014 Bill requires that the use of recording equipment must be in accordance with procedures, for a legitimate purpose, and proportionate to the objective for which the equipment was installed.
The 2014 Bill makes a broad exception to these safeguards for law enforcement agencies and government intelligence agencies in the interest of the sovereignty, integrity, security or the strategic, scientific, or economic interest of India.
- Privacy Standards and Self Regulation: The 2014 Bill establishes a specific mechanism of self regulation where industry associations will develop privacy standards and adhere to them. For this purpose, an industry ombudsman should be appointed. The standards must be in conformity with the National Privacy Principles and the provisions of the Privacy Bill. The developed standards will be submitted to the Authority and the Authority may frame regulations based on the standards. If an industry association has not developed privacy standards, the Authority may frame regulations for a specific sector.
- Settlement of Disputes and Appellate Tribunal: The 2014 Bill makes significant change to the process for settling disputes from the 2011 Bill. In the 2014 Bill an Alternative Dispute Mechanism is established where disputes between individuals and data controllers are first addressed by the Privacy Officer of each Data Controller or the industry level Ombudsman. If individuals are not satisfied with the decision of the Ombudsman they may take the complaint to the Authority. Individuals can also take the complaint directly to the Authority if they wish. If an individual is aggrieved with the decision of the Authority, by a privacy officer or ombudsman through the Alternative Dispute Resolution mechanism, or by the adjudicating officer of the Authority, they may approach the Appellate Tribunal. Any order from the Appellate Tribunal can be appealed at a high court.
In the 2011 Bill disputes between the data controller and an individual can be taken directly to the Appellate Tribunal and orders from the Authority can be appealed at the Tribunal. There is not further path for appeal to an order of the tribunal.
- Offences and Penalties: The 2014 Bill changes the structure of the offences and penalties section by breaking the two into separate sections - one addressing offences and one addressing penalties while the 2011 Bill addressed offences and penalties in the same section.
- Offences: The 2014 Bill penalizes every offence with imprisonment and a fine and empowers a police officer not below the rank of Deputy Superintendent of Police to investigate any offence, limits the courts ability to take cognizance of an offence to only those brought by the Authority, requires that the Court be no lower than a Chief Metropolitan Magistrate or a Chief Judicial Magistrate, and permits courts to compound offences. The 2014 Bill further specifies that any offence that is punishable with three years in prison and above is cognizable, and offences punishable with three years in prison are bailable. . Under the 2014 Bill offences are defined as:
- Unauthorized interception of communications
- Disclosure of intercepted communications
- Undertaking unauthorized Covert Surveillance
- Unauthorized use of disclosure of communication data
The offences defined under the Act are reflected in the 2011 Bill, but the time in prison and fine is higher in the 2014 Bill.
Penalties: The 2014 Bill provides a list of penalties including:
- Penalty for obtaining personal data on false pretext
- Penalty for violation of conditions of license pertaining to maintenance of secrecy and confidentiality by telecommunications service providers
- Penalty for disclosure of other personal information
- Penalties for contravention of directions of the Authority
- Penalties for data theft
- Penalties for unauthorised collection, processing, and disclosure of personal data
- Penalties for unauthorized use of personal data for direction marketing. These penalties reflect the penalties in the 2011 bill, but prescribe higher fines
Adjudicating Officer: Unlike the 2011 Bill that did not have in place an adjudicating officer, the 2014 Bill specifies that the Chairperson of the Authority will appoint a Member of the Authority not below the Rank of Director of the Government of India to be an adjudicating officer. The adjudicating officer will have the power to impose a penalty and will have the same powers as vested in a civil court under the Code of Civil Procedure. Every proceeding before the adjudicating officer will be considered a judicial processing. When adjudicating the officer must take into consideration the amount of disproportionate gain or unfair advantage, the amount of loss caused, the respective nature of the default
Civil Remedies and compensation: Both the 2011 and 2014 Bill contain provisions that permit an individual to pursue a civil remedy, but the 2014 Bill limits these instances to - if loss or damage has been suffered or an adverse determination is made about an individual due to negligence on complying with the Act, and provides for the possibility that the contravening parties will have to provide a public notice of the offense.
The 2014 Bill removes provisions specifying that individuals that have suffered loss due to a contravention by the data controller of the Act are entitled to compensation.
Exceptions for intelligence agencies: Unlike the 2011 Bill, the 2014 Bill includes an exception for Government Intelligence Agencies and Law Enforcement Agencies – stating that the Authority will not have the power to conduct investigations, issue appropriate orders and directions or otherwise adjudicate complaints in respect of action taken by the Government intelligence agencies and Law Enforcement agencies for achieving any of the objectives that reflect the defined exceptions to privacy.
The Centre for Internet and Society welcomes many of the changes that are reflected in the Privacy Bill 2014, but are cautious about the wide exceptions that have been carved out for law enforcement and intelligence agencies in the Bill.
In 2012, the Report of Group of Expert s on Privacy was developed for the purpose of informing a privacy framework for India. As such the Centre for Internet and Society will be analyzing in upcoming posts the draft Privacy Bill 2014 and the recommendations in the Report of the Group of Experts on Privacy.
Surveillance and Privacy
 privacy-lirneasia.pdf
—
PDF document,
37 kB (38903 bytes)
privacy-lirneasia.pdf
—
PDF document,
37 kB (38903 bytes)
Marco Civil da Internet: Brazil’s ‘Internet Constitution’
Introduction:
Marco Civil da Internet:
The fundamentals:
Rights and responsibilities of users and service providers:
Conclusion:
Intermediary Liability Resources
- Shielding the Messengers: Protecting Platforms for Expression and Innovation. The Centre for Democracy and Technology. December 2012, available at: https://www.cdt.org/files/pdfs/CDT-Intermediary-Liability-2012.pdf: This paper analyses the impact that intermediary liability regimes have on freedom of expression, privacy, and innovation. In doing so, the paper highlights different models of intermediary liability regimes, reviews different technological means of restricting access to content, and provides recommendations for intermediary liability regimes and provides alternative ways of addressing illegal content online.
- Internet Intermediaries: Dilemma of Liability: Article 19. 2013, available at: http://www.article19.org/data/files/Intermediaries_ENGLISH.pdf:This Policy Document reviews different components of intermediary liability and highlights the challenges and risks that current models of liability have to online freedom of expression. Relying on international standards for freedom of expression and comparative law, the document includes recommendations and alternative models that provide stronger protection for freedom of expression. The key recommendation in the document include: web hosting providers or hosts should be immune from liability to third party content if they have not modified the content, privatised enforcement should not be a model and removal orders should come only from courts or adjudicatory bodies, the model of notice to notice should replace notice and takedown regimes, in cases of alleged serious criminality clear conditions should be in place and defined.
- Comparative Analysis of the National Approaches to the Liability of Internet Intermediaries: Prepared by Daniel Seng for WIPO, available at http://www.wipo.int/export/sites/www/copyright/en/doc/liability_of_internet_intermediaries.pdf:This Report reviews the intermediary liability regimes and associated laws in place across fifteen different contexts with a focus on civil copyright liability for internet intermediaries. The Report seeks to find similarities and differences across the regimes studied and highlight principles and components in different that can be used in international treaties and instruments, upcoming policies, and court decisions.
- Freedom of Expression, Indirect Censorship, & Liability for Internet Intermediaries. The Electronic Frontier Foundation. February 2011, available at: http://infojustice.org/download/tpp/tpp-civil-society/EFF%20presentation%20ISPs%20and%20Freedom%20of%20Expression.pdf:This presentation was created for the Trans-Pacific Partnership Stakeholder Forum in Chile and highlights that for freedom of expression to be protected, clear legal protections for internet intermediaries are needed and advocates for a regime that provides blanket immunity to intermediaries or is based on judicial takedown notices.
- Study on the Liability of Internet Intermediaries. Contracted by the European Commission. 2007, available at: http://ec.europa.eu/internal_market/e-commerce/docs/study/liability/final_report_en.pdf. This Report provides insight on the application of the intermediary liability sections of the EU e-commerce directive and studies the impact of the regulations under the Directive on the functioning of intermediary information society services. To achieve this objective, the study identifies relavant case law across member states, calls out and evaluates developing trends across Member States, and draws conclusions.
- Internet Intermediary Liability: Identifying Best Practices for Africa. Nicolo Zingales for the Association for Progressive Communications, available at: https://www.apc.org/en/system/files/APCInternetIntermediaryLiability_BestPracticesAfrica_20131125.pdf: This background paper seeks to identify challenges and opportunities in addressing intermediary liability for countries in the African Union and recommend safeguards that can be included in emerging intermediary liability regimes in the context of human rights. The paper also reviews different models of intermediary liability and discusses the limitations, scope, and modes of operation of each model.
- The Liability of Internet Intermediaries in Nigeria, Kenya, South Africa, and Uganda: An uncertain terrain. Association for Progressive Communications. October 2012, available at: http://www.academia.edu/2484536/The_liability_of_internet_intermediaries_in_Nigeria_Kenya_South_Africa_and_Uganda_An_uncertain_terrain:This Report reviews intermediary liability in Nigeria, Kenya, South Africa and Uganda – providing background to the political context, relevant legislation, and present challenges . In doing so, the Report provides insight into how intermediary liability has changed in recent years in these contexts and explores past and present debates on intermediary liability. The Report concludes with recommendations for stakeholders affected by intermediary liability.
- The Fragmentation of intermediary liability in the UK. Daithi Mac Sithigh. 2013, available at: http://jiplp.oxfordjournals.org/content/8/7/521.full.pdf?keytype=ref&ijkey=zuL8aFSzKJqkozT. This article looks at the application of the Electronic Commerce Directive across Europe and argues that it is being intermixed and subsequently replaced with provisions from national legislation and provisions of law from area specific legislation. Thus, the article argues that systems for intermediary liability are diving into multiple systems – for example for content related to copyright intermediaries are being placed with new responsibilities while for content related to defamation, there is a reducing in the liability that intermediaries are held to.
- Regimes of Legal Liability for Online Intermediaries: an Overview. OECD, available at: http://www.oecd.org/sti/ieconomy/45509050.pdf. This article provides an overview of different intermediary liability regimes including EU and US.
- Closing the Gap: Indian Online Intermediaries and a Liability System Not Yet Fit for Purpose. GNI. 2014, available at: http://www.globalnetworkinitiative.org/sites/default/files/Closing%20the%20Gap%20-%20Copenhagen%20Economics_March%202014_0.pdf. This Report argues that the provisions of the Information Technology Act 2000 are not adequate to deal with ICT innovations , and argues that the current liability regime in India is hurting the Indian internet economy.
- Intermediary Liability in India. Centre for Internet and Society. 2011, available at: http://cis-india.org/internet-governance/intermediary-liability-in-india.pdf. This report reviews and ‘tests’ the effect of the Indian intermediary liability on freedom of expression. The report concludes that the present regime in India has a chilling effect on free expression and offers recommendations on how the Indian regime can be amended to protect this right.
- The Liability of Internet Service providers and the exercise of the freedom of expression in Latin America have been explored in detail through the course of this research paper by Claudio Ruiz Gallardo and J. Carlos Lara Galvez. The paper explores the efficacy and the implementation of proposals to put digital communication channels under the oversight of certain State sponsored institutions in varying degrees. The potential consequence of legal intervention in media and digital platforms, on the development of individual rights and freedoms has been addressed through the course of this study. The paper tries to arrive at relevant conclusions with respect to the enforcement of penalties that seek to redress the liability of communication intermediaries and the mechanism that may be used to oversee the balance between the interests at stake as well as take comparative experiences into account. The paper also analyses the liability of technical facilitators of communications while at the same time attempting to define a threshold beyond which the interference into the working of these intermediaries may constitute an offence of the infringement of the privacy of users. Ultimately, it aims to derive a balance between the necessity for intervention, the right of the users who communicate via the internet and interests of the economic actors who may be responsible for the service: http://www.palermo.edu/cele/pdf/english/Internet-Free-of-Censorship/02-Liability_Internet_Service_Providers_exercise_freedom_expression_Latin_America_Ruiz_Gallardo_Lara_Galvez.pdf
Click to read the newsletter from the Association of Progressive Communications. The summaries for the reports can be found below:
Internet Intermediaries: The Dilemma of Liability in Africa. APC News, May 2014, available at: http://www.apc.org/en/node/19279/. This report summarizes the challenges facing internet content regulators in Africa, and the effects of these regulations on the state of the internet in Africa. Many African countries do not protect intermediaries from potential liability, so some intermediaries are too afraid to transmit or host content on the internet in those countries. The report calls for a universal rights protection for internet intermediaries.
APC’s Frequently Asked Questions on Internet Intermediary Liability: APC, May 2014, available at: http://www.apc.org/en/node/19291/. This report addresses common questions pertaining to internet intermediaries, which are entities which provide services that enable people to use the internet, from network providers to search engines to comments sections on blogs. Specifically, the report outlines different models of intermediary liability, defining two main models. The “Generalist” model intermediary liability is judged according to the general rules of civil and criminal law, while the “Safe Harbour” model protects intermediaries with a legal safe zone.
New Developments in South Africa: APC News, May 2014, available at: http://www.apc.org/en/news/intermediary-liability-new-developments-south-afri. This interview with researchers Alex Comninos and Andrew Rens goes into detail about the challenges of intermediary in South Africa. The researchers discuss the balance that needs to be struck between insulating intermediaries from a fear of liability and protecting women’s rights in an environment that is having trouble dealing with violence against women. They also discuss South Africa’s three strikes policy for those who pirate material.
Preventing Hate Speech Online In Kenya: APCNews, May 2014, available at: http://www.apc.org/en/news/intermediary-liability-preventing-hate-speech-onli. This interview with Grace Githaiga investigates the uncertain fate of internet intermediaries under Kenya’s new regime. The new government has mandated everyone to register their SIM cards, and indicated that it was monitoring text messages and flagging those that were deemed risky. This has led to a reduction in the amount of hate speech via text messages. Many intermediaries, such as newspaper comments sections, have established rules on how readers should post on their platforms. Githaiga goes on to discuss the issue of surveillance and the lack of a data protection law in Kenya, which she sees as the most pressing internet issue in Kenya.
New Laws in Uganda Make Internet Providers More Vulnerable to Liability and State Intervention: APCNews, May 2014, available at: http://www.apc.org/en/news/new-laws-uganda-make-internet-providers-more-vulne. In an interview, Lilian Nalwoga discusses Uganda’s recent anti-pornography law that can send intermediaries to prison. The Anti-Pornography Act of 2014 criminalizes any sort of association with any form of pornography, and targets ISPs, content providers, and developers, making them liable for content that goes through their systems. This makes being an intermediary extremely risky in Uganda. The other issue with the law is a vague definition of pornography. Nalwoga also explains the Anti-Homosexuality Act of 2014 bans any promotion or recognition of homosexual relations, and the monitoring technology the government is using to enforce these laws.
New Laws Affecting Intermediary Liability in Nigeria: APCNews, May 2014, available at: http://www.apc.org/en/news/new-laws-affecting-intermediary-liability-nigeria. Gbenga Sesan, executive director of Paradigm Initiative Nigeria, expounds on the latest trends in Nigerian intermediary liability. The Nigerian Communications Commission has a new law that mandates ISPs store users data for at least here years, and wants to make content hosts responsible for what users do on their networks. Additionally, in Nigeria, internet users register with their real name and prove that you are the person who is registration. Sesan goes on to discuss the lack of safe harbor provisions for intermediaries and the remaining freedom of anonymity on social networks in Nigeria.
Internet Policies That Affect Africans: APC News, May 2014, available at: http://www.apc.org/en/news/intermediary-liability-internet-policies-affect-af. The Associsation for Progressive Communcations interviews researcher Nicolo Zingales about the trend among African governments establishing further regulations to control the flow of information on the internet and hold intermediaries liable for content they circulate. Zingales criticizes intermediary liability for “creating a system of adverse incentives for free speech.” He goes on to offer examples of intermediaries and explain the concept of “safe harbor” legislative frameworks. Asked to identify best and worst practices in Africa, he highlights South Africa’s safe harbor as a good practice, and mentions the registration of users via ID cards as a worst practice.
Towards Internet Intermediary Responsibility: Carly Nyst, November 2013, available at: http://www.genderit.org/feminist-talk/towards-internet-intermediary-responsibility. Nyst argues for a middle ground between competing goals in internet regulation in Africa. Achieving one goal, of protecting free speech through internet intermediaries seems at odds with the goal of protecting women’s rights and limiting hate speech, because one demands intermediaries be protected in a legal safe harbor and the other requires intermediaries be vigilant and police their content. Nyst’s solution is not intermediary liability but responsibility, a role defined by empowerment, and establishing an intermediary responsibility to promote positive gender attitudes.


