India Subject to NSA Dragnet Surveillance! No Longer a Hypothesis — It is Now Officially Confirmed
As of last week, it is officially confirmed that the metadata of everyone´s communications is under the NSA´s microscope. In fact, the leaked data shows that India is one of the countries which is under NSA surveillance the most!
This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC. This blog was cross-posted in Medianama on 24th June 2013.
¨Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?”, the democratic senator, Ron Wyden, asked James Clapper, the director of national intelligence a few months ago. “No sir”, replied Clapper.
True, the National Security Agency (NSA) does not collect data on millions of Americans. Instead, it collects data on billions of Americans, Indians, Egyptians, Iranians, Pakistanis and others all around the world.
Leaked NSA surveillance
Verizon Court Order
Recently, the Guardian released a top secret order of the secret Foreign Intelligence Surveillance Court (FISA) requiring Verizon on an “ongoing, daily basis” to hand over information to the NSA on all telephone calls in its systems, both within the US and between the US and other countries. Verizon is one of America's largest telecoms providers and under a top secret court order issued on 25 April 2013, the communications records of millions of US citizens are being collected indiscriminately and in bulk supposedly until 19 July 2013. In other words, data collection has nothing to do with whether an individual has been involved in a criminal or terrorist activity or not. Literally everyone is potentially subject to the same type of surveillance.
USA Today reported in 2006 that the NSA had been secretly collecting the phone call records of millions of Americans from various telecom providers. However, the April 25 top secret order is proof that the Obama administration is continuing the data mining programme begun by the Bush administration in the aftermath of the 09/11 terrorist attacks. While content data may not be collected, this dragnet surveillance includes metadata such as the numbers of both parties on a call, location data, call duration, unique identifiers, the International Mobile Subscriber Identity (IMSI) number and the time and duration of all calls.
Content data may not be collected, but metadata can also be adequate to discover an individual's network of associations and communications patterns. Privacy and human rights concerns rise from the fact that the collection of metadata can result in a highly invasive form of surveillance of citizens´ communications and lives. Metadata records can enable the US government to know the identity of every person with whom an individual communicates electronically, as well as the time, duration and location of the communication. In other words, metadata is aggregate data and it is enough to spy on citizens and to potentially violate their right to privacy and other human rights.
PRISM
Recently, a secret NSA surveillance programme, code-named PRISM, was leaked by The Washington Post. Apparently, not only is the NSA gaining access to the meta data of all phone calls through the Verizon court order, but it is also tapping directly into the servers of nine leading Internet companies: Microsoft, Skype, Google, Facebook, YouTube, Yahoo, PalTalk, AOL and Apple. However, following these allegations, Google, Microsoft and Facebook recently asked the U.S. government to allow them to disclose the security requests they receive for handing over user data. It remains unclear to what extent the U.S. government is tapping into these servers.
Yet it appears that the PRISM online surveillance programme enables the NSA to extract personal material, such as audio and video chats, photographs, emails and documents. The Guardian reported that PRISM appears to allow GCHQ, Britain's equivalent of the NSA, to secretly gather intelligence from the same internet companies. Following allegations that GCHQ tried to circumvent UK law by using the PRISM computer network in the US, the British foreign secretary, William Hague, stated that it is “fanciful nonsense” to suggest that GCHQ would work with an agency in another country to circumvent the law. Most notably, William Hague emphasized that reports that GCHQ are gathering intelligence from photos and online sites should not concern people who have nothing to hide! However, this implies that everyone is guilty until proven innocent...when actually, democracy mandates the opposite.
James R. Clapper, the US Director of National Intelligence, stated:
“Information collected under this program is among the most important and valuable foreign intelligence information we collect, and is used to protect our nation from a wide variety of threats. The unauthorized disclosure of information about this important and entirely legal program is reprehensible and risks important protections for the security of Americans.”
So essentially, Clapper stated that in the name of US national security, the personal data of billions of citizens around the world is being collected. By having access to data stored in the servers of some of the biggest Internet companies in the world, the NSA ultimately has access to the private data of almost all the Internet users in the world.
Boundless Informant
And once the NSA has access to tons of data through the Verizon court order and the PRISM surveillance programme, how does it create patterns of intelligence and generally mine huge volumes of data?
The Guardian released top secret documents about the NSA data mining tool, called Boundless Informant; this tool is used to detail and map by country the volumes of information collected from telephone and computer networks. The focus of the Boundless Informant is to count and categorise the records of communication, known as metadata, and to record and analyse where its intelligence comes from. One of the leaked documents states that the tool is designed to give NSA officials answers to questions like: “What type of coverage do we have on country X”. According to the Boundless Informant documents, the NSA has been collecting 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. During the same month, 97 billion pieces of intelligence from computer networks were collected worldwide.
The following “global heat map” reveals how much data is being collected by the NSA from around the world:
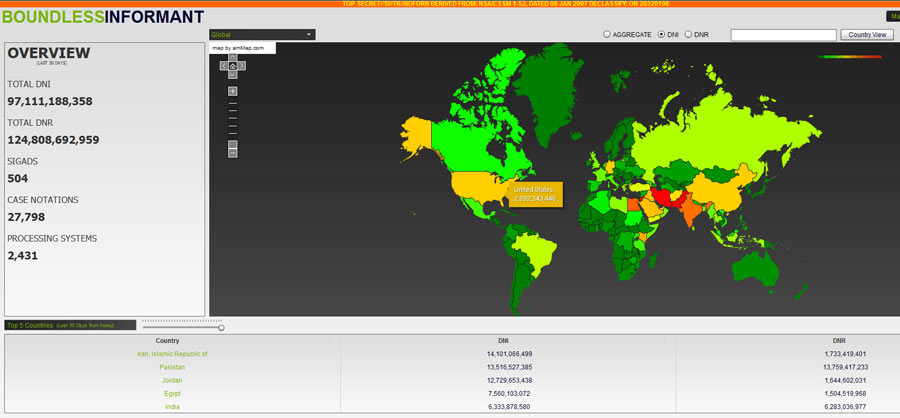
The colour scheme of the above map ranges from green (least subjected to surveillance) through yellow and orange to red (most surveillance). India is notably orange and is thus subject to some of the highest levels of surveillance by the NSA in the world.
During a mere 30-day period, the largest amount of intelligence was gathered from Iran with more than 14 billion reports, while Pakistan, Jordan and Egypt were next in line in terms of intelligence gathering. Unfortunately, India ranks 5th worldwide in terms of intelligence gathering by the NSA. According to the map above, 6.3 billion pieces of intelligence were collected from India by the NSA from February to March 2013. In other words, India is currently one of the top countries worldwide which is under the US microscope, with 15% of all information being tapped by the NSA coming from India during February-March 2013.
Edward Snowden is the 29-year-old man behind the NSA leaks...who is responsible for one of the most important leaks in US (and one may argue, global) history.
So what does this all mean for India?
In his keynote speech at the 29th Chaos Communications Congress, Jacob Appelbaum stated that surveillance should be an issue which concerns “everyone´s department”, especially in light of the NSA spying on citizens all over the world. True, the U.S. appears to have a history in spying on civilians, and the Corona, Argon, and Lanyard satellites used by the U.S. for photographic surveillance from the late 1950s is proof of that. But how does all this affect India?
By tapping into the servers of some of the biggest Internet companies in the world, such as Google, Facebook and Microsoft, the NSA does not only gain access to the data of American users, but also to that of Indian users. In fact, the “global heat map” of the controversial Boundless Informant data mining tool clearly shows that India ranked 5th worldwide in terms of intelligence gathering, which means that not only is the NSA spying on Indians, but that it is also spying on India more than most countries in the world. Why is that a problem?
India has no privacy law. India lacks privacy legislation which could safeguard citizens from potential abuse by different types of surveillance. But the worst part is that, even if India did have privacy laws, that would still not prevent the NSA from tapping into Indians´ data through the servers of Internet companies, such as Google. Moreover, the fact that India lacks a Privacy Commissioner means that the country lacks an expert authority who could address data breaches.
Recent reports that the NSA is tapping into these servers ultimately means that the U.S. government has access to the data of Indian internet users. However, it remains unclear how the U.S. government is handling Indian data, which other third parties may have access to it, how long it is being retained for, whether it is being shared with other third parties or to what extent U.S. intelligence agencies can predict the behaviour of Indian internet users through pattern matching and data mining.
Many questions remain vague, but one thing is clear: through the NSA´s total surveillance programme, the U.S. government can potentially control the data of billions of internet users around the world, and with this control arises the possibility of oppression. It´s not just about the U.S. government having access to Indians´ data, because access can lead to control and according to security expert, Bruce Schneier:
“Our data reflects our lives...and those who control our data, control our lives”.
How are Indians supposed to control their data, and thus their lives, when it is being stored in foreign servers and the U.S. has the “right” to tap into that data? The NSA leaks mark a significant point in our history, not only because they are resulting in corporations seeking data request transparency, but also because they are unveiling a major global issue: surveillance is a fact and can no longer can be denied. The massive, indiscriminate collection of Indians´ data, without their prior knowledge or consent, and without the provision of guarantees in regards to how such data is being handled, poses major threats to their right to privacy and other human rights. The potential for abuse is real, especially since the larger the database, the larger the probability for error. Mining more data does not necessarily increase security; on the contrary, it increases the potential for abuse, especially since technology is not infallible and data trails are not always accurate.
What does this mean? Well, probably the best case scenario is that an individual is targeted. The worst case scenario is that an individual is imprisoned (or maybe even murdered - remember the drones?) because his or her data “says” that he or she is guilty. Is that the type of world we want to live in?
What can we do now?
Let´s start from the basics. India needs privacy legislation. India needs privacy legislation now. India needs privacy legislation now, more than ever.
Privacy legislation would regulate the collection, access to, sharing of, retention and disclosure of all personal data within India. Such legislation could also regulate surveillance and the interception of communications, in compliance with the right to privacy and other human rights. A Privacy Commissioner would also be established through privacy legislation, and this expert authority would be responsible for overseeing the enforcement of the Privacy Act and addressing data breaches. But clearly, privacy legislation is not enough. The various privacy laws of European countries have not prevented the NSA from tapping into the servers of some of the biggest Internet companies in the world and from gaining access to the data of millions of citizens around the world. Yet, privacy legislation in India should be a basic prerequisite to ensure that data is not breached within India and by those who may potentially gain access to Indian national databases.
As a next- but immediate- step, the Indian government should demand answers from the NSA to the following questions:
-
What type of data is collected from India and which parties have access to it?
-
How long is such data retained for? Can the retention period be renewed and if so, for how long?
-
Is data collected on Indian internet users shared with third parties? If so, which third parties can gain access to this data and under what conditions? Is a judicial warrant required?
In addition to the above questions, the Indian government should also request all other information relating to Indians´ data collected through the PRISM programme, as well as proceed with a dialogue on the matter. Governments are obliged to protect their citizens from the abuse of their human rights, especially in cases when such abuse may occur from foreign agencies. Thus, the Indian government should ensure that the future secret collection of Indians´ data is prevented and that Internet companies are transparent and accountable in regards to who has access to their servers.
On an individual level, Indians can protect their data by using encryption, such as GPG encryption for their emails and OTR encryption for instant messaging. Tor is free software and an open network which enables online anonymity by bouncing communications around a distributed network of relays run by volunteers all around the world. Tor is originally short for “The Onion Router” and “onion routing” refers to the layers of encryption used. In particular, data is encrypted and re-encrypted multiple times and is sent to randomly selected Tor relays. Each relay decrypts a “layer” of encryption to reveal it only to the next relay in the circuit and the final relay decrypts the last “layer” of encryption. Essentially, Tor reduces the possibility of original data being understood in transit and conceals the routing of it.
To avoid surveillance, the use of HTTPS-Everywhere in the Tor Browser is recommended, as well as the use of combinations of additional software, such as TorBirdy and Enigmail, OTR and Diaspora. Tor hidden services are communication endpoints that are resistant to both metadata analysis and surveillance, which is why they are highly recommended in light of the NSA´s surveillance. An XMPP client that ships with an XMPP server and a Tor hidden service is a good example of how to avoid surveillance.
Protecting our data is more important now than ever. Why? Because global, indiscriminate, mass data collection is no longer a hypothesis: it´s a fact. And why is it vital to protect our data? Because if we don´t, we are ultimately sleepwalking into our control and oppression where basic human rights, such as freedom, would be a myth of the past.
The principles formulated by the Electronic Frontier Foundation and Privacy International on communication surveillance should be taken into consideration by governments and law enforcement agencies around the world. In short, these principles are:
-
Legality: Limitations to the right to privacy must be prescribed by law
-
Legitimate purpose: Access to communications or communications metadata should be restricted to authorised public authorities for investigative purposes and in pursuit of a legitimate purpose
-
Necessity: Access to communications or communications metadata by authorised public authorities should be restricted to strictly and demonstrably necessary cases
-
Adequacy: Public authorities should be restricted from adopting or implementing measures that allow access to communications or communications metadata that is not appropriate for fulfillment of the legitimate purpose
-
Competent authority: Authorities must be competent when making determinations relating to communications or communications metadata
-
Proportionality: Public authorities should only order the preservation and access to specifically identified, targeted communications or communications metadata on a case-by-case basis, under a specified legal basis
-
Due process: Governments must respect and guarantee an individual's human rights, that may interference with such rights must be authorised in law, and that the lawful procedure that governs how the government can interfere with those rights is properly enumerated and available to the public
-
User notification: Service providers should notify a user that a public authority has requested his or her communications or communications metadata with enough time and information about the request so that a user may challenge the request
-
Transparency about use of government surveillance: The access capabilities of public authorities and the process for access should be prescribed by law and should be transparent to the public
-
Oversight: An independent oversight mechanism should be established to ensure transparency of lawful access requests
-
Integrity of communications and systems: Service providers are responsible for the secure transmission and retention of communications data or communications metadata
-
Safeguards for international cooperation: Mutual legal assistance processes between countries and how they are used should be clearly documented and open to the public
-
Safeguards against illegitimate access: Governments should ensure that authorities and organisations who initiate, or are complicit in, unnecessary, disproportionate or extra-legal interception or access are subject to sufficient and significant dissuasive penalties, including protection and rewards for whistleblowers, and that individuals affected by such activities are able to access avenues for redress
-
Cost of surveillance: The financial cost of providing access to user data should be borne by the public authority undertaking the investigation
Applying these above principles is a prerequisite, but may not be enough. Now is the time to resist unlawful and non-transparent surveillance. Now is the time for everyone to fight for their right to be free.
Is a world without freedom worth living in?

