Battle for the Internet
In this article written by Latha Jishnu and published by Down to Earth, Issue: March 15 2011, the author reports about the events in the United States in the post WikiLeaks scenario.
As the Internet becomes the public square and the marketplace of our world, it is increasingly becoming a contested terrain. Its potential for diffusing knowledge and subverting the traditional channels of information is tremendous. So it is not surprising that governments, corporations and even seemingly innocuous social networking sites all want to control and influence the way the Internet operates. It’s easy to see why. Close to a third of humanity is linked to this system—and the dramatic growth in Internet usage over the past decade is set to explode in coming years. So is its commercial promise. Latha Jishnu looks at events in the US following the WikiLeaks exposé of its diplomatic cables, and in the hot spots of political turmoil across the world to understand the significance of the Internet in today’s interconnected world and the threats it faces. Arnab Pratim Dutta explains the technology used to block access to the Net.
 |
|
An opposition supporter holds up a laptop showing images of celebrations in Cairo's Tahrir Square, after Egypt's President Hosni Mubarak resigned (Photo: Reuters) |
Ideas and ideologies, images and reports of events, both minor and cataclysmic, fly on the Internet, swirling through cyberspace, gathering resonance, metamorphosing and touching millions of lives in different ways. Many of the ideas—and visuals—could be banal (as they very often are), some dangerous, others bringing promise of change. Some have the power to subvert, helping to stir and stoke the smouldering embers of political and social unrest as recent uprisings in north Africa, West Asia and Asia have shown. To many, the Internet is the rebel hero of our times, subverting conventional media and leaking news and information that governments would like to censor. Even a village in the remote reaches of Odisha’s Malkangiri district which may have no electricity is in some way linked to cyberspace through smart cell phones because mobile operators are increasingly turning Internet service providers (ISPs) and bringing the worldwide web to the conflict-ridden forests of central India.
It is about the power and reach of connection, unprecedented since people first began communicating with each other. The Internet, therefore, is turning into a conflict zone with everyone seeking control of it: governments, corporations and social networking sites, all of whom have different agendas. Social networks may seem innocuous but they are as much a hazard as the others to Internet freedom. Surveillance of “netizens” is becoming commonplace, whether in democracies or in totalitarian regimes, through a host of new laws and regulations ostensibly aimed at strengthening national security, cyber security or protecting business interests.
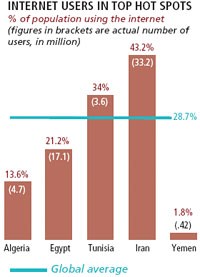 |
While most governments are seeking to filter and block specific content, in extreme cases, as in Egypt, the Net has been blacked out using what some experts say is the “kill switch” (see ‘The Egypt shutdown’). This could emerge as the biggest threat to the Internet since other regimes could be tempted to go the Egyptian way. Most governments, however, prefer not to use it, not even the censorship-obsessed Chinese and Saudi regimes because the Internet is also about business—commerce of increasing significance is being routed through its sinews. Take one small example: In January alone, Britons spent a whopping £5.1 billion online, recording a 21 per cent jump in e-commerce revenues over January 2010, according to the latest edition of the IMRG/CapGemini e-Retail Sales Index. It is the kind of figure that stops authorities from reaching for the kill switch. |
In the case of China, e-commerce transactions hit 4.5 trillion yuan (US $682.16 billion) in 2010, up 22 per cent year-on-year, according to China e- Business Research Center and CNZZ Data Center. Of this, online B2B or business-to-business deals accounted for the bulk: 3.8 trillion yuan (US
$576.05 billion). And retail sales are expected to zoom, too, pretty soon with e-commerce websites selling directly to customers growing to more than 18,600 last year. Thanks to a dramatic spike in the rate of Net penetration and impressive growth of online business.
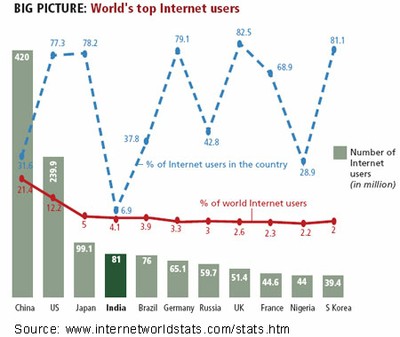
But the world has a long way to go before the Internet becomes ubiquitous or an all-encompassing global commons. Currently, just two billion people are linked to the system (see above: ‘Big picture’), which is less than a third of the world’s population. And the reach, as the chart shows, is rather patchy. India may be in the top five Internet user nations with a total of 81 million users but penetration is an abysmal 6.9 per cent, the worst in the list. Blame that on our pathetic education levels and poverty. China, however, is the undisputed leviathan with 420 million users in 2010—some estimates put the figure closer to 500 million now—who account for more than a fifth of the world’s Internet users. No other country’s growth in this sector matches China’s either in speed or drama.
 |
This is one reason Washington frequently raises the issue of China’s policing of the Internet in different fora. The most recent was on February 15 when secretary of state Hillary Clinton made the second of her rousing speeches on safeguarding the Internet from all kinds of government interference. Speaking at George Washington University in Washington DC, Clinton pointed out that the attempts to control the Internet were rife across the world but singled China for repeated attacks.
“In China, the government censors content and redirects search requests to error pages. In Burma, independent news sites have been taken down with distributed denial of service (DDoS) attacks. In Cuba, the government is trying to create a national intranet, while not allowing their citizens to access the global internet. In Vietnam, bloggers who criticize the government are arrested and abused. In Iran, the authorities block opposition and media websites, target social media, and steal identifying information about their own people in order to hunt them down. These actions reflect a landscape that is complex and combustible, and sure to become more so in the coming years as billions of more people connect to the Internet.”
 |
That seemed a fair assessment of the trends but the irony is that even as the secretary of state was speaking, the Department of Justice was seeking to enforce a court order to direct Twitter Inc, to provide the US government records of three individuals, including Birgitta Jonsdottir, a member of Iceland's Parliament who had been in touch with others about WikiLeaks and its founder Juan Assange last year when WikiLeaks released its huge cache of US diplomatic cables. |
A commentary in China Daily noted with asperity: “The Assange case reveals such rhetoric is just so much hypocrisy. It is apparent that when Internet freedom conflicts with self-declared US national interests, or when Internet freedom exposes lies by the self-proclaimed open and transparent government, it immediately becomes a crime.”
The Assange case more than anything else has exposed how vulnerable the Net is to political meddling and control. In December last year, Amazon said it stopped hosting the WikiLeaks website because it “violated its terms of service” and not because the office of the Senate Homeland Security Committee chaired by Joe Lieberman had questioned Amazon about its relationship with WikiLeaks.
WikiLeaks had turned to Amazon to keep its site available after hackers tried to flood it and prevent users accessing the classified information. Few people were willing to credit Amazon’s feeble explanation for cutting off WikiLeaks and the general surmise was that Lieberman had put some kind of pressure on the webhosting platform. According to one analyst, the simple reason is that the US government is one of the company’s biggest clients. According to a press note issued by the company: “Government adoption of AWS (Amazon Web Services) grew significantly in 2010. Today we have nearly 20 government agencies leveraging AWS, and the US federal government continues to be one of our fastest growing customer segments.”
As Amazon abandoned WikiLeaks, Paypal, Visa and MasterCard had also dumped WikiLeaks. This set off a fullscale cyber war in which a fourth party made its presence felt: Hackers/ ‘hacktivists’ who unleashed operation payback for what they deemed unfair targeting of WikiLeaks and Assange. This involved a series of (DDOS) attacks on Paypal, MasterCard, Swiss Bank PostFinance and Lieberman’s website.
So while governments in many parts of the world block sites, jail or kill dissidents for expressing their views on the Net, threats to the freedom of the Internet come primarily from the paranoia that governments suffer and from badly crafted policies they implement to protect business and other interests.
The US, the ultimate symbol of liberal democracy, is no less uneasy about the power of the Internet. A slew of laws are making their way through the Senate, laws that will give the administration sweeping powers to seize domain names and shut down websites, even those outside its territory, and laws that strengthen the powers of the president in the time of a cyber emergency, including the use of a kill switch. In September, the US Senate introduced the Combating Online Infringement and Counterfeits Act, which would allow the government to create a blacklist of websites that are suspected to be infringing IP rights and to pressure or require all ISPs to block access to those sites. In these cases, no due process of law protects people before they are disconnected or their sites are blocked.
In India, in the wake of the terrorist attacks in Mumbai in November 2008, Parliament hastily passed amendments to the Information Technology Act, 2000, without any discussion in either House. The December 2008 amendments have some good points but they also allow increased online surveillance. Section 69A permits the Centre to “issue directions for blocking of public access to any information through any computer resource”, which means that the government can block any website.
Pranesh Prakash of the Bengalurubased Centre for Internet and Society notes that while necessity or expediency in terms of certain restricted interests is specified, no guidelines have been specified. “It has to be ensured that they are prescribed first, before any powers of censorship are granted to anybody,” said Prakash in an analysis of the amendments. “In India, it is clear that any law that gives unguided discretion to an administrative authority to exercise censorship is unreasonable.”
Civil rights activists say the section has broadened the scope of surveillance and that there are no legal or procedural safeguards to prevent violation of civil liberties.
As the battle for keeping the Internet is joined by netizens who are aware of the power of connection, governments, too, are ramping up command and control measures. Among the risks to an open, democratic Internet are the following:
Threat to universality
The basic design principle underlying the World Wide Web is universality, and, according to its founder Tim Berners-Lee, several threats are emerging. Among these are: cable companies that sell Internet connectivity wanting to limit their Net users to downloading only the company’s mix of entertainment and social networking sites (see ‘Hidden dangers of Facebook’).
Another is by pricing Net connectivity out of the reach of the poor and allowing differential pricing. Berners- Lee, warned at a recent London conference: “There are a lot of companies who would love to be able to limit what web pages you can see...the moment you let Net neutrality go, you lose the web as it is...You lose something essential—the fact that any innovator can dream up an idea and set up a website at some random place and let it just take off from word of mouth...”
Actions against piracy
The nub of such operations lies in the US Department of Homeland Security, whose Immigration and Customs Enforcement (ICE) and the Department of Justice (DoJ) have been seizing domains because they are suspected of hawking pirated goods. The first seizure was in November last year when 82 websites selling counterfeit goods ranging from handbags to golf clubs were taken out.
Last month, there was another raid on the Internet. According to TorrentFreak and other Internet monitoring sites, the two agencies wrongly shut down 84,000 websites that had not broken the law, falsely accusing them of child pornography crimes. After the mistake was identified, it took about three days for some of the websites to go live again. The domain provider, FreeDNS, was taken aback. “Freedns.afraid.org has never allowed this type of abuse of its DNS service. We are working to get the issue sorted as quickly as possible,” it said.
Earlier, DoJ and ICE had seized the domain of the popular sports streaming and P2P download site Rojadirecta. What is shocking is that the site is based in Spain and is perfectly legal. Two courts in Spain have ruled that the site operates legally, and other than the .org domain the site has no links to the US.
Internet freedom could easily become the biggest casualty in the illconceived and poorly designed procedures adopted by developed countries— France, the UK, South Korea, Taiwan and New Zealand have similar laws—to protect intellectual property from counterfeiters and pirates, primarily at the behest of the film and music recording industries.
There are indications India may be planning to follow suit (see ‘India’s three-strikes policy’), although civil rights groups say it could amount to a form of deprivation of liberty.
Surveillance technology
The problem with the use of technology in keeping the Internet safe cuts both ways. With increasing number of cyber attacks on both official and public websites from an array of hackers and malware, governments are reaching for ever more sophisticated high-tech surveillance systems. For instance, computer systems of the US Congress and the executive branches are under attack an average of 1.8 billion times per month, according to a recent Senate report. The result: more spyware. One such is deep packet inspection technology. It is a tool that protects customers from rampant spam and virus traffic. Experts say the Internet could not survive without this technology and yet, it helps authorities to keep a close watch on what people are doing on the Net. In the US, ISPs are required to have this technology.
So what can be done? Keep close tabs on government involvement in the Internet and ensure that its intrusion in both the content and the engines of this system is kept to the minimum.
Read the original article written by Latha Jishnu in Down to Earth here

